Kerberos Authentication
In the Windows
environment, authentication delegation is possible only with the
Kerberos protocol. Therefore, all systems involved in delegation
scenarios must use the Kerberos protocol. There are two main delegation
scenarios:
Basic Kerberos Delegation
As illustrated in Figure 4,
when using the basic Kerberos authentication, the user authenticates to
the front-end server; the server requests data from the back-end server
using the user’s account.
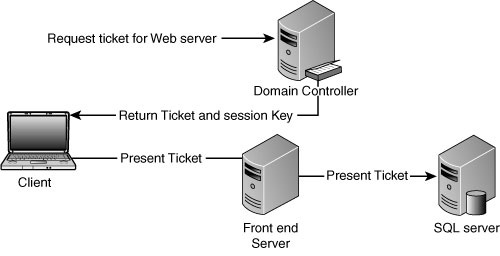
Delegation enables the
user’s credentials to be passed from one server to another and preserves
the user identity. This will allow you to have multiple front-end
servers. This enables you to scale the middle tier for growth.
Note
Kerberos
authentication passes a Kerberos token provided by the Kerberos Ticket
Granting service only after the initial authentication. At no point are
the user’s credentials passed within the server farms.
Kerberos Authentication Using Constrained Delegation
This can allow you to
enforce a limit that applies to which network resources an account
trusted for delegation can access. This feature is supported in Windows
2003 domain functional level and up. Figure 5 shows Kerberos authentication using constrained delegation.
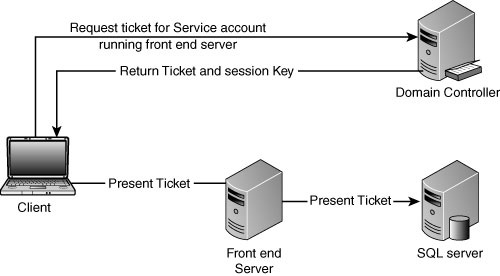
To
limit the resources that services can access on behalf of a user, you
can configure constrained delegation by listing services to which
account can present delegated credentials. This list is in the form of
SPNs (service principle names). Impersonating to any nontrusted back end
will fail authentication.
This is the most common deployment of Kerberos authentication.
Setting Up Kerberos
To use Kerberos completely, you must configure a number of things, including the following:
Figure 6 shows the Kerberos flow.
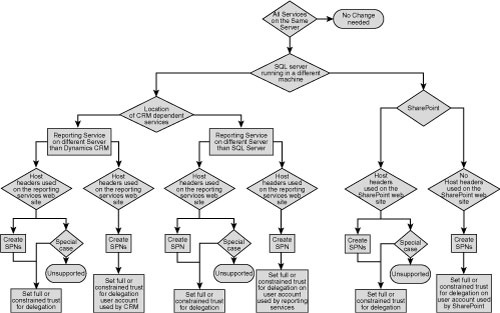
Client Configuration
Before setting up or debugging Kerberos, client settings need to be verified.
Note
To ensure consistency
with the client settings, it is recommended to use Group Policy (GPO) to
enforce the settings on client machines.
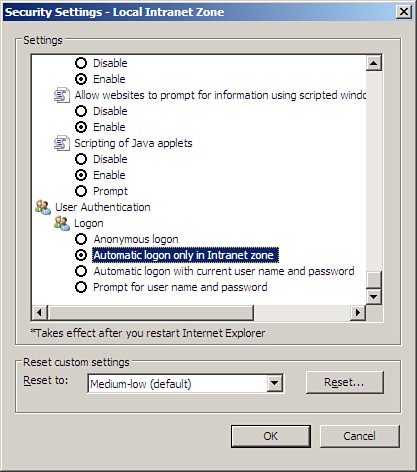
The following steps ensure that integrated authentication is enabled on the client:
In Internet Explorer, click Tools, Internet Options, Advanced, and scroll to Security.
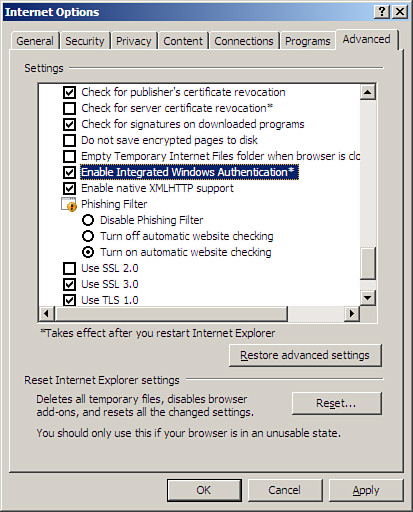
Ensure
Automatic Logon is enabled in the appropriate zone on the client. (In
Internet Explorer, click Tools, Internet Options, Security.)
Note
Client needs to be a member of a trusted domain.
Ensure the URL is part of the client’s local intranet sites.
The domain user must have the Account Is Sensitive and Cannot Be Delegated option unselected in Active Directory.