Now that you are familiar with the task of creating
OUs, you should find creating and managing other Active Directory
objects quite simple. The following sections look at the details.
1. Overview of Active Directory Objects
When you install and configure a domain controller,
Active Directory sets up some organization for you, and you can create
and manage several types of objects. This section describes these
features.
1.1. Active Directory Organization
By default, after you install and configure a domain
controller, you will see the following organizational sections within
the Active Directory Users And Computers tool (they look like folders):
Built-In
The Built-In container includes all of the
standard groups that are installed by default when you promote a domain
controller. You can use these groups to administer the servers in your
environment. Examples include the Administrators group, Backup
Operators, and Print Operators.
Computers
By default, the Computers container contains a
list of the workstations in your domain. From here, you can manage all
of the computers in your domain.
Domain Controllers
The Domain Controllers container includes a list of all of the domain controllers for the domain.
Foreign security principals
Foreign security principals are any objects to which security can be assigned and that are not part of the current domain. Security principals
are Active Directory objects to which permissions can be applied, and
they can be used to manage permissions in Active Directory.
Users
The Users container includes all of the security
accounts that are part of the domain. When you first install the domain
controller, there will be several groups in this container. For
example, the Domain Admins group and the Administrator account are
created in this container.
1.2. Active Directory Objects
You can create and manage several different types of Active Directory objects. The following are specific object types:
Computer
Computer objects represent workstations that are
part of the Active Directory domain. All computers within a domain
share the same security database, including user and group information.
Computer objects are useful for managing security permissions and
enforcing Group Policy restrictions.
Contact
Contact objects
are usually used in OUs to specify the main administrative contact.
Contacts are not security principals like users. They are used to
specify information about individuals within the organization.
Group
Group objects
are logical collections of users primarily for assigning security
permissions to resources. When managing users, you should place them
into groups and then assign permissions to the group. This allows for
flexible management without the need to set permissions for individual
users.
Organizational Unit
An OU object is created to build a hierarchy
within the Active Directory domain. It is the smallest unit that can be
used to create administrative groupings, and it can be used to assign
group policies. Generally, the OU structure within a domain reflects a
company's business organization.
Printer
Printer objects map to printers.
Shared Folder
Shared Folder objects
map to server shares. They are used to organize the various file
resources that may be available on file/print servers. Often, Shared
Folder objects are used to give logical names to specific file
collections. For example, systems administrators might create separate
shared folders for common applications, user data, and shared public
files.
User
A User object
is the fundamental security principal on which Active Directory is
based. User accounts contain information about individuals, as well as
password and other permission information.
InetOrgPerson
The InetOrgPerson object
is an Active Directory object that defines attributes of users in
Lightweight Directory Access Protocol (LDAP) and X.500 directories.
MSMQ Queue Alias
An MSMQ Queue Alias object
is an Active Directory object for the MSMQ-Custom-Recipient class type.
The MSMQ (Microsoft Message Queuing) Queue Alias object associates an
Active Directory path and a user-defined alias with a public, private,
or direct single-element format name. This allows a queue alias to be
used to reference a queue that might not be listed in Active Directory
Domain Services (AD DS).
1.2.1. Creating Objects Using the Active Directory Users And Computers Tool
Exercise 1
walks you through the steps you need to take to create various objects
within an Active Directory domain. In this exercise, you create some
basic Active Directory objects.
Open the Active Directory Users And Computers tool. Expand
the current domain to list the objects currently contained within it.
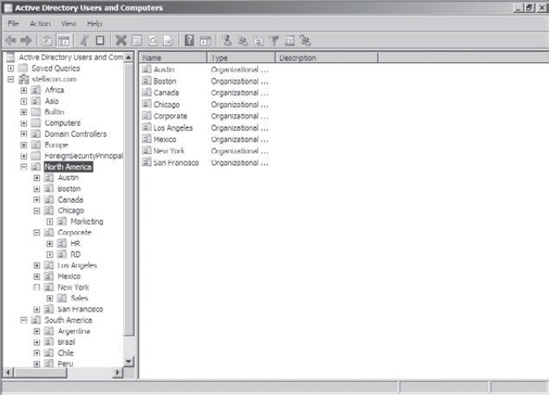
For this exercise you will use the second- and third-level OUs
contained within the North America top-level OU, as shown in the
following graphic.
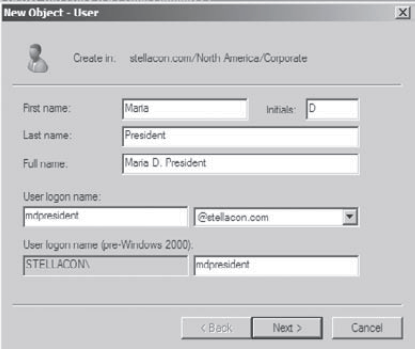
Right-click the Corporate OU, and select New => User. Fill in the following information: First Name: Maria Initial: D Last Name: President Full Name: (leave as default) User Logon Name: mdpresident (leave default domain)
Click Next to continue.
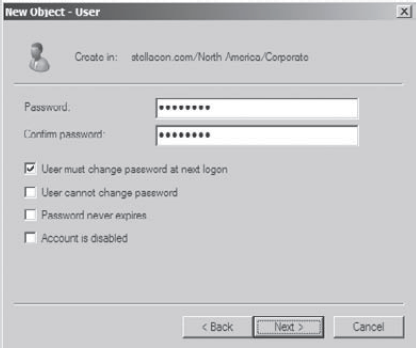
Enter in "P@ssw0rd"
for the password for this user, and then confirm it. Note that you can
also make changes to password settings here. Click Next.
You will see a summary of the user information. Click Finish to create the new user. Click on the RD container and create another user in that container with the following information: First Name: John Initials: Q Last Name: Admin Full Name: (leave as default) User Logon Name: jqadmin (leave default domain)
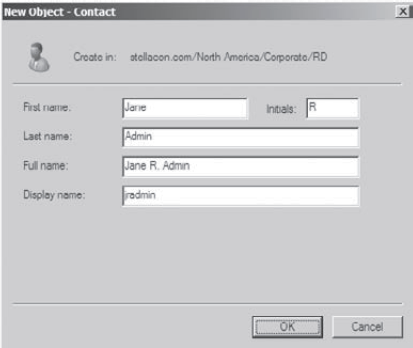
Click Next to continue. Assign the password "P@ssw0rd". Click Next, and then click Finish to create the user. Right-click the RD OU, and select New => Contact. Use the following information to fill in the properties of the Contact object: First Name: Jane Initials: R Last Name: Admin Display Name: jradmin
Click OK to create the new Contact object.
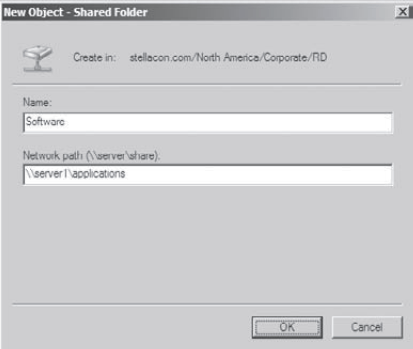
Right-click the RD OU, and select New => Shared Folder. Enter Software for the name and \\server1\applications
for the network path (also known as the Universal Naming Convention
[UNC] path). Note that you can create the object even though this
resource (the physical server) does not exist. Click OK to create the
Shared Folder object.
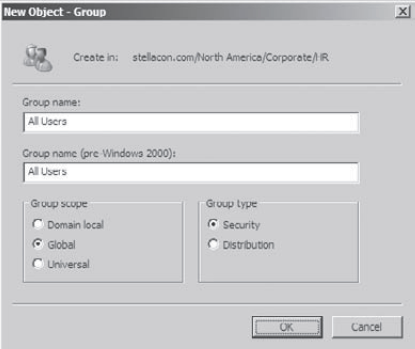
Right-click the HR OU, and select New => Group. Type All Users
for the group name. Do not change the value in the Group Name
(Pre–Windows 2000) field. For the Group Scope, select Global, and for
the Group Type, select Security. To create the group, click OK.
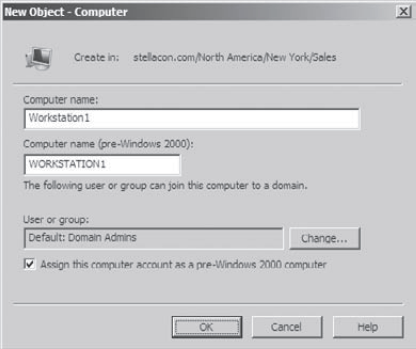
Right-click the Sales OU and select New => Computer. Type Workstation1
for the name of the computer. Notice that the pre–Windows 2000 name is
automatically populated and that, by default, the members of the Domain
Admins group are the only ones that can add this computer to the
domain. Place a check mark in the Assign This Computer Account As A
Pre–Windows 2000 Computer box, and then click OK to create the Computer
object.
Close the Active Directory Users And Computers tool.
|
1.2.2. Importing Objects from a File
In Exercise 1
we created an account using the Active Directory Users And Computers
tools. But what if we needed to bulk import accounts? There are two
main applications for doing bulk imports of accounts: the ldifde.exe utility and the csvde.exe utility. Both utilities import accounts from files.
The ldifde utility imports from
line-delimited files. This utility allows an administrator to export
and import data, thus allowing batch operations like Add, Modify, and
Delete to be performed in Active Directory. Windows Server 2008
includes ldifde.exe to help support batch operations.
csvde.exe performs the same export functions as ldifde.exe, but csvde.exe uses a comma-separated file format. The csvde.exe utility does not allow administrators to modify or delete objects. It only supports adding objects to Active Directory.
1.2.3. Active Directory Migration Tool (ADMT) v3
Another tool you can use to help import and migrate
users is the Active Directory Migration Tool (ADMT) v3. The ADMT v3
allows an administrator to migrate users, groups, and computers from a
Microsoft Windows NT 4.0 domain to a Windows Server 2008 Active
Directory domain.
Administrators can also use the ADMT v3 to migrate
users, groups, and computers between Active Directory domains in
different forests (interforest migration) and between Active Directory
domains in the same forest (intraforest migration).
ADMT v3 also helps administrators perform
security translations from a Windows NT 4.0 domain to a Windows Server
2008 Active Directory domain. ADMT v3 will also allow the security
translations between Active Directory domains in different forests.