1. Understanding Password Policies
Your domain’s password policy is configured by a GPO scoped to the domain. Within the GPO, in the Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy node, you can configure the policy settings that determine password requirements. The Password Policy node is shown in Figure 1.
You can understand the effects of the policies by considering the life cycle of a user password. A user is required to change his or her password within the number of days specified by the Maximum Password Age policy setting. When the user enters a new password, the length of the new password is compared to the number of characters in the Minimum Password Length policy. If the Password Must Meet Complexity Requirements policy is enabled, the password must contain at least three of four character types:
- Uppercase—for example, A to Z
- Lowercase—for example, a to z
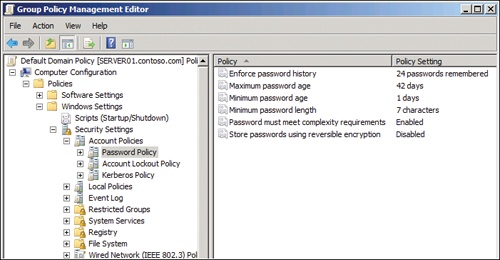
Figure 1. The Password Policy node of a GPO
- Numeric—0 to 9
- Nonalphanumeric—symbols such as !, #, %, or &
If the new password meets the requirements, Active Directory puts the password through a mathematical algorithm that produces a representation of the password called the hash code. The hash code is unique; no two passwords can create the same hash code. The algorithm used to create the hash code is called a one-way function. You cannot put the hash code through a reverse function to derive the password. The fact that it is a hash code, and not the password itself, that is stored in Active Directory helps to increase the security of the user account.
Occasionally, applications require the ability to read a user’s password. This is not possible because, by default, only the hash code is stored in Active Directory. To support such applications, you can enable the Store Passwords Using Reversible Encryption policy. This policy is not enabled by default, but if you enable the policy, user passwords are stored in an encrypted form that can be decrypted by the application. Reversible encryption significantly reduces the security of your domain, so it is disabled by default, and you should strive to eliminate applications that require direct access to passwords.
Additionally, Active Directory can check a cache of the user’s previous hash codes to make sure that the new password is not the same as the user’s previous passwords. The number of previous passwords against which a new password is evaluated is determined by the Enforce Password History policy. By default, Windows maintains the previous 24 hash codes.
If a user is determined to reuse her password when the password expiration period occurs, she could simply change her password 25 times to work around the password history. To prevent that from happening, the Minimum Password Age policy specifies an amount of time that must pass between password changes. By default, it is one day. Therefore, the determined user would have to change her password once a day for 25 days to reuse a password. This type of deterrent is generally successful at discouraging such behavior.
These policy settings—history, minimum age, and maximum age—affect users changing their passwords. The settings do not affect administrators using the Reset Password command to change another user’s password.
2. Understanding Account Lockout Policies
An intruder can gain access to the resources in your domain by determining a valid user name and password. User names are relatively easy to identify because most organizations create user names from an employee’s email address, initials, combinations of first and last names, or employee IDs. After a user name is known, the intruder might determine the correct password by guessing or by repeatedly logging on with combinations of characters or words until the logon is successful.
This type of attack, called brute force, can be thwarted by limiting the number of incorrect logons allowed. That is exactly what account lockout policies achieve. Account lockout policies are located in the node of the GPO directly below Password Policy. The Account Lockout Policy node is shown in Figure 2.
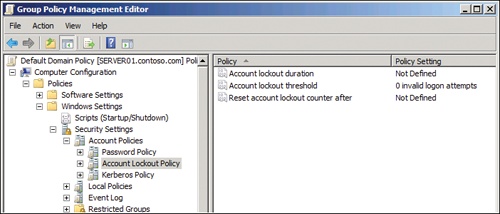
Figure 2. The Account Lockout Policy node of a GPO
Three settings are related to account lockout. The first of these settings, Account Lockout Threshold, determines the number of invalid logon attempts permitted within a time specified by the second of these settings, Reset Account Lockout Counter After. If an attack results in more unsuccessful logons within that time frame, the user account is locked out. When an account is locked out, Active Directory denies logon to that account, even if the correct password is specified.
3. Configuring the Domain Password and Lockout Policy
Active Directory supports one set of password and lockout policies for a domain. These policies are configured in a GPO that is scoped to the domain. A new domain contains a GPO called Default Domain Policy that is linked to the domain and includes the default policy settings for password, account lockout, and Kerberos policies, shown in Figures Figure 1 and Figure 2. You can change the settings by editing the Default Domain Policy.
Note
PRACTICE IT
You can practice configuring a domain’s password and lockout policies in Exercise 1, “Configure the Domain’s Password and Lockout Policies,” in the practice for this lesson.
Note
BEST PRACTICE DO NOT OVERLOAD THE DEFAULT DOMAIN POLICY GPO
The best practice is to edit the Default Domain Policy GPO to specify the password policy settings for your organization. You should also use the Default Domain Policy GPO to specify account lockout policies and Kerberos policies. Do not use the Default Domain Policy GPO to deploy any other custom policy settings. In other words, use the Default Domain Policy GPO to define the password, account lockout, and Kerberos policies for the domain, and nothing else. Additionally, do not define password, account lockout, or Kerberos policies for the domain in any other GPO.
Note
ACCOUNT SETTINGS OVERRIDE POLICIES
The password settings configured in the Default Domain Policy affect all user accounts in the domain. The settings can be overridden, however, by the password-related properties of the individual user accounts. On the Account tab of a user’s Properties dialog box, shown in Figure 3, you can specify settings such as Password Never Expires or Store Password Using Reversible Encryption. For example, if five users have an application that requires direct access to their passwords, you can configure the accounts for those users to store their passwords using reversible encryption.
