3. Tracking Auditing Events
After
you’ve enabled the security auditing policies that you want Windows
Home Server to monitor, you can start tracking them to look for
suspicious behavior. You do this using Windows Home Server’s Event
Viewer. Unfortunately, the Security event log (which is where the
auditing events appear) likely has tens of thousands of items. How do
you look for suspicious behavior in such a large database?
Viewing Auditing Events with a Filter
The trick is to filter the log to show just the events you want. Here are the steps to follow:
1. | Log on to Windows Home Server.
|
2. | Select Start, Administrative Tools, Event Viewer. Windows Home Server opens the Event Viewer.
|
3. | Open the Windows Logs, Security branch.
|
4. | In
the Actions pane, click Filter Current Log. Windows Home Server opens
the Filter Current Log dialog box with the Filter tab displayed.
|
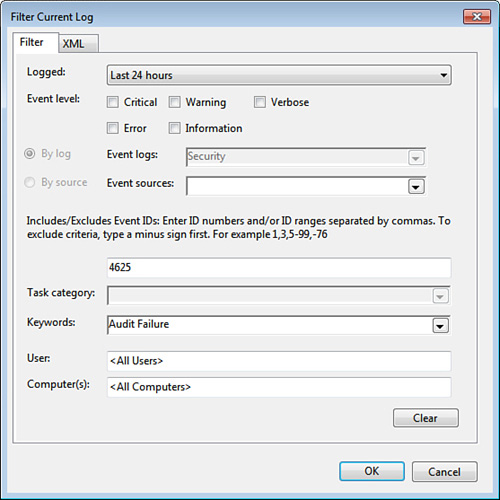
5. | In the Logged list, select the time frame you want to use, such as Last 24 Hours.
|
6. | In
the Includes/Excludes Event IDs text box, type the event ID you want to
find, if any. You can also enter a range (such as 4720–4782), or you
can exclude an ID by preceding it with a minus sign.
|
7. | In the Keywords list, activate the check boxes for just the events you want to see (such as Audit Failure). Figure 8 shows a sample filter.
|
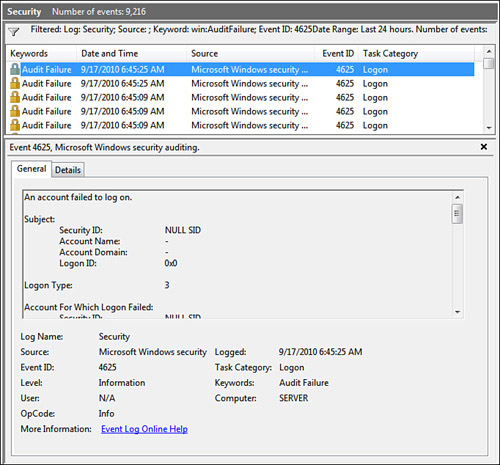
8. | Click OK. Event Viewer filters the Security log using your criteria. Figure 9 shows an example.
|
Viewing Auditing Events with a Script
The
only problem with filtering the Security log, as described in the
previous section, is that you can’t filter based on detailed
information such as the account logon error code. To do that, you need
to use a script. Listing 1
presents a script that extracts just those Security events in which the
type is Audit Failure and the error code is 0xC000006A (which
represents an incorrect password).
Listing 1. A Script That Extracts Events from the Security Log
'
' Use WMI to extract events from the Security log where:
' - The type is "Audit Failure" (5)
' - The date is today
' - The error code points to an incorrect password (0xC000006A)
`
compName = "localhost"
Set objWMI = GetObject("winmgmts:{impersonationLevel=impersonate}!//" & _
compName & "\root\cimv2")
Set colSecLog = objWMI.ExecQuery("SELECT * FROM Win32_NTLogEvent Where " & _
"LogFile = 'Security' And " & _
"EventType = 5 And " & _
"TimeWritten > '" & TodaysDate & "' And " & _
"Message Like '%0xC000006A%'")
'
' Run through the returned events
'
i = 0
For Each objEvent in colSecLog
'
' Display the event data
'
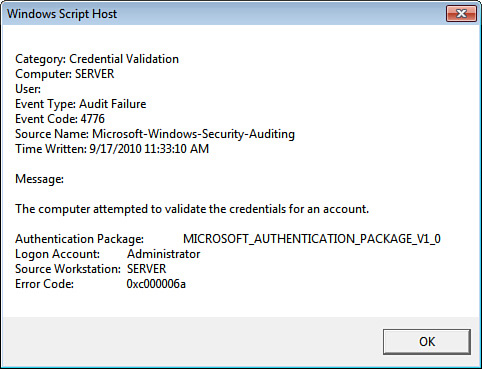
WScript.Echo "Category: " & objEvent.CategoryString & VBCrLf & _
"Computer: " & objEvent.ComputerName & VBCrLf & _
"User: " & objEvent.User & VBCrLf & _
"Event Type: " & objEvent.Type & VBCrLf & _
"Event Code: " & objEvent.EventCode & VBCrLf & _
"Source Name: " & objEvent.SourceName & VBCrLf & _
"Time Written: " & ReturnLogDate(objEvent.TimeWritten) & _
VBCrLf & VBCrLf & _
"Message: " & VBCrLf & VBCrLf & objEvent.Message
i = i + 1
Next
'
' Check for no events
'
If i = 0 Then
WScript.Echo "No events found!"
End If
'
' Release objects
'
Set wmi = Nothing
Set secLog = Nothing
'
' This function creates a datatime string based on today's date
`
Function TodaysDate()
strYear = Year(Now)
If Month(Now) < 10 Then
strMonth = "0" & Month(Now)
Else
strMonth = Month(Now)
End If
If Day(Now) < 10 Then
strDay = "0" & Day(Now)
Else
strDay = Day(Now)
End If
TodaysDate = strYear & strMonth & strDay & "000000.000000-000"
End Function
'
' This function takes the event datetime value and converts
' it to a friendlier date and time format
'
Function ReturnLogDate(logTime)
eventYear = Left(logTime, 4)
eventMonth = Mid(logTime, 5, 2)
eventDay = Mid(logTime, 7, 2)
eventHour = Mid(logTime, 9, 2)
eventMinute = Mid(logTime, 11, 2)
eventSecond = Mid(logTime, 13, 2)
ReturnLogDate = DateSerial(eventYear, eventMonth, eventDay) & " " & _
TimeSerial(eventHour, eventMinute, eventSecond)
End Function
|
The script uses WMI to query the W32_NTLogEvent database, which consists of all the events on the system. The query extracts just those events in which the following is true:
The LogFile property equals Security.
The EventType property equals 5, which represents Audit Failure events.
The TimeWritten property contains only today’s date. The values in the TimeWritten property use the datetime data type, which uses the general format yyyymmddhhmmss.000000-000. So, the script uses the TodaysDate function to return a datetime value that corresponds to midnight today. The query actually looks for events that were written to the log after that time.
The Message property (which holds the error code, among other data) contains the error code 0xC000006A.
Then a For Each...Next loop runs through all the returned events. For each event, various event properties are displayed in a dialog box, as shown in Figure 10. The code calls the ReturnLogDate function to convert the TimeWritten property’s datetime value into a more readable format.