Understanding Windows Firewall with Advanced Security
Windows Firewall with Advanced Security is a host-based, stateful firewall included in Windows Server 2012 and Windows 8. The feature was first introduced in Windows Vista and Windows Server 2008, and its functionality has been enhanced in several ways in later Windows versions.
As a host-based firewall, Windows Firewall with Advanced Security is designed to protect the local computer, unlike a perimeter firewall, which is designed to protect the network itself. However, to protect a network, you also need to protect each computer on the network because even if a single computer is compromised, it could provide an attacker with a way to compromise the rest of the network.
As a stateful firewall, Windows Firewall with Advanced Security can keep track of the state of packets as they travel across the network. Packets that match a specified rule can be either allowed or denied depending on how the rule has been configured. Windows Firewall with Advanced Security can inspect and filter both inbound and outbound packets, and it supports both Internet Protocol version 4 (IPv4) and version 6 (IPv6).
Windows Firewall with Advanced Security also includes built-in functionality for creating rules that govern IPsec communications. This means you can use Windows Firewall with Advanced Security to encrypt and secure communications between computers on the network.
Windows Firewall with Advanced Security interoperates with other Windows features to help ensure the security of the computer. To fully understand how Windows Firewall with Advanced Security works, you need to understand these other features:
- Windows Filtering Platform
- Windows service hardening
- Network location awareness
Windows Filtering Platform
Windows Filtering Platform (WFP) is a collection of application programming interfaces (APIs) and system services that allow for the creation of network-filtering applications on Windows Vista or later. By using WFP, third-party developers can create host-based security tools such as these:
- Firewalls
- Intrusion-detection systems
- Network-monitoring tools
- Antivirus programs
- Parental controls
WFP is also the underlying engine used for implementing packet-filtering logic in Windows Firewall with Advanced Security. The components of WFP include the following:
- Base Filter Engine (BFE) This component runs in user mode and receives filtering requests from Windows Firewall with Advanced Security. Such requests are then forwarded to the Generic Filter Engine.
- Generic Filter Engine (GFE) This component runs in kernel mode and receives filtering requests from the BFE. The GFE then makes such requests available to callout modules that map to different layers of the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol stack. As the TCP/IP protocol stack processes a packet, each callout module calls the GFE to determine whether to accept or reject the packet.
- Callout modules These run in kernel mode and are used by the GFE to inspect the different layers of a packet as the packet is passed down the TCP/IP protocol stack. For example, the Transport Layer module is used to inspect the Transport Layer protocol portion of the packet, which is either TCP or User Datagram Protocol (UDP).
Note
MORE INFO Windows Filtering Platform
When you start a computer running Windows Vista or later, Windows Firewall with Advanced Security initially uses boot-time filters to protect the system during the early stages of the boot process. Once the BFE starts, the boot-time filters are replaced by persistent filters that are stored in the registry and applied whenever the BFE is running. Then once the Windows Firewall service starts, the policy rules and settings that have been configured for Windows Firewall with Advanced Security are applied.
Windows service hardening
Windows service hardening is a collection of strategies that helps protect critical Windows services from behaving abnormally. Windows service hardening is thus designed to help reduce the possible damage that could occur if a Windows service is compromised by an attacker.
Windows service hardening is implemented using strategies such as the following:
- Using LocalService or NetworkService instead of LocalSystem as the security context for a service whenever possible
- Assigning services only the minimum Windows privileges they need to perform their function
- Implementing per-service identity using the per-service security identifier (SID), which allows services to apply explicit access control lists (ACLs) to resources used only by the service
- Applying a write-restricted access token to the service process so that attempts by the service to write to resources that do not explicitly grant access to the per-service SID will fail
Windows service hardening also protects Windows services using service restriction rules, which are not user configurable. Service restriction rules define the types of network packets that can be transmitted by or received from a Windows service. When a packet is being examined, service restriction rules are applied before Windows Firewall with Advanced Security rules are applied.
Network location awareness
Network location awareness is a feature of Windows Vista and later that allows network-aware applications to change their behavior based on the computer’s network connectivity. The three network location types that a computer running Windows can detect are these:
- Public A computer on a public network is considered to be shared with the world. By default, when a Windows computer connects to a new network for the first time, the network location type for that network is configured as public.
- Private A computer on a private network is one that is not directly accessible by the world. To configure the network location type of a Windows computer as private, you must be a local administrator on the computer.
- Domain A computer that belongs to an Active Directory domain is automatically assigned a network location type of domain.
Network location awareness is used by Windows Firewall with Advanced Security to determine which firewall profile will be used for protecting each connection on the computer. This is described in more detail in the next section.
Note
Network location awareness on multihomed computers
If a computer is multihomed (connected to more than one network), each connection is assigned the appropriate network location type based on the type of network to which it is connected.
Managing firewall profiles
Computers today are often connected to different networks at different times, and they might even be connected to several networks at the same time. Each type of network can have a different set of security requirements:
- A computer connected to a public network should consider that network unsafe because of the threat of malware from the Internet. As a result, Windows Firewall with Advanced Security on such a computer should be configured to restrict most forms of traffic.
- A computer connected to a private network, such as a small office/home office (SOHO) with Internet access provided by a network address translation (NAT) router, should have Windows Firewall with Advanced Security configured in a less restrictive way than for a public network. This is needed to allow the computer to communicate freely with other computers on the same private network.
- A computer that belongs to an Active Directory domain should have Windows Firewall with Advanced Security configured even less restrictively than for a private network. This is because Active Directory environments usually include additional layers of security, such as perimeter firewalls that further isolate the network from the outside world.
A typical day with an enterprise laptop might be as follows:
- Bob brings his laptop to work, inserts it into the docking station, turns it on, and logs on to Active Directory.
- Bob takes a lunch break and decides to get more work done, so he uses the Wi-Fi hotspot at the coffee shop to establish a connection to the Internet and browses the news for a while. Because his company has implemented DirectAccess, Bob can also safely connect to resources on his company’s network even while he’s connected to the public Internet.
- When Bob returns to the office, he is informed that he has to visit a small customer site to help them troubleshoot a problem on their workgroup network. When Bob arrives at the customer site, he connects his laptop to their network so that he can help them resolve their problem.
- While connected to the customer’s network, Bob realizes he needs to access a resource on his own company’s network. Unfortunately, the NAT router on the customer’s network has not been configured to allow DirectAccess traffic, so Bob has to establish a virtual private network (VPN) connection with his company’s network.
Examining the day just described for Bob, you can see that the following scenarios came into play:
- In the morning, Bob connects to one network (his company’s network). This network has a network location type of domain.
- At lunch, Bob connects to two networks:
- A Wi-Fi network, which has a network location type of public
- His company’s network (via DirectAccess), which has a network location type of domain
- At the customer site, Bob initially connects to one network (the customer’s network). Because this network is a workgroup and not a domain, the network location type is private.
- Later at the customer site, Bob needs to remain connected to the customer’s network while also connecting to his own company’s network. To do this, Bob establishes a VPN connection to his company’s network. At this point, Bob is connected to two networks:
- The customer’s network, which has a network location type of private
- His own company’s network, which has a network location type of domain
Although the preceding example uses client systems, it’s also common for servers to be multihomed and connected to multiple networks in certain scenarios. For example, a clustered Hyper-V host in a production environment might be simultaneously connected to the following networks:
- Production network This is the network that client systems are able to access and consume services from.
- Management network This network is used only for managing the servers using a systems-management platform such as Microsoft System Center Configuration Manager.
- Failover clustering network This network is used for failover cluster communications, such as heartbeat communications, and for connecting to a cluster shared volume (CSV).
- Live migration network This network is used to support the live migration of virtual machines.
Multihomed servers are also common in edge scenarios where the server is connected to both the corporate intranet and the public Internet.
Windows Firewall with Advanced Security makes securing the preceding scenarios possible by implementing a separate firewall profile for each network connection on the computer. A firewall profile is a grouping of firewall rules and other configuration settings that are applied to a network connection that has a specific network location type. Windows Firewall with Advanced Security applies firewall profiles to all types of network connections on the computer, including network adapters and tunnel interfaces.
Windows Firewall with Advanced Security has three firewall profiles, which correspond to the three network location types on the Windows platform:
- Domain profile This profile is automatically applied to any network connection that Windows identifies as having a network location type of domain.
- Private profile This profile is automatically applied to any network connection that Windows identifies as having a network location type of private.
- Public profile This profile is automatically applied to any network connection that Windows identifies as having a network location type of public.
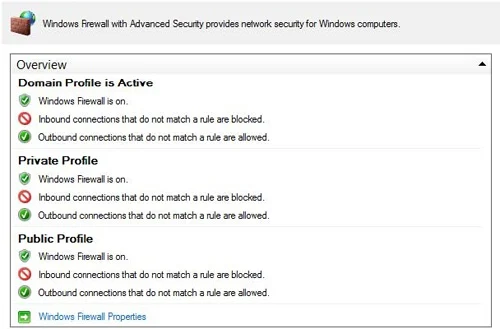
All three profiles can be active at the same time on a computer if Windows detects that there are network connections of each type present. You can view the status of each firewall profile on a computer by opening the Windows Firewall with Advanced Security Microsoft Management Console (MMC) snap-in. One way of doing this on Windows Server 2012 is by selecting Windows Firewall with Advanced Security from the Tools menu of Server Manager. Once the snap-in is open, select the root node in the console tree and examine the Overview section in the details pane.
Figure 1 shows an example of this for a computer that has only one network connection of the domain type. Note that all three profiles have Windows Firewall turned on for them, but only the domain profile is active. The reason the other profiles are turned on is so that if a connection to a private or public network is established on the computer, firewall protection will immediately be implemented for such connections.