1. Using Loopback Processing
Group Policy settings applied to users normally take
precedence over Group Policy settings that apply to computers. As a
reminder, the last Group Policy that is applied is the one that takes
precedence. Because a computer boots up before a user can log on, the
Group Policy settings for the computer is applied first, and the Group
Policy settings for the user are applied last.
Note
A simple way of understanding loopback processing is
that it ensures that the policies applying to the computer take
precedence over the policies applying to the user. For example, if you
want to enable folder redirection for users ONLY when they log on to
terminal servers, you can enable loopback processing in a GPO that
applies to users only when they log on to computers in the terminal
server OU.
However, there are times when you want this
reversed. In other words, you want the Group Policy settings for the
computer to take precedence over the Group Policy settings for the
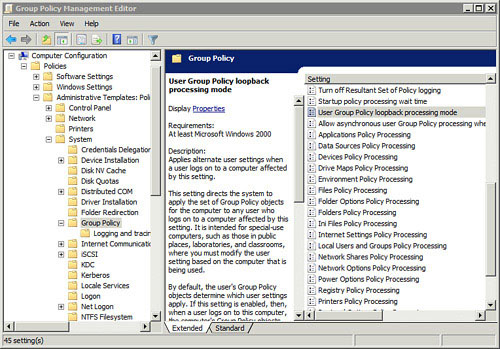
user. You can do so by enabling Loopback Processing. Figure 1 shows the location of this setting.
2. Running Scripts with Group Policy
You can write scripts and have them automatically
run through Group Policy. The great strength of this is that you write
and configure the script once, and it runs on all the computers in your
domain or all the computers in a specific OU, depending on where you
link the GPO holding the script.
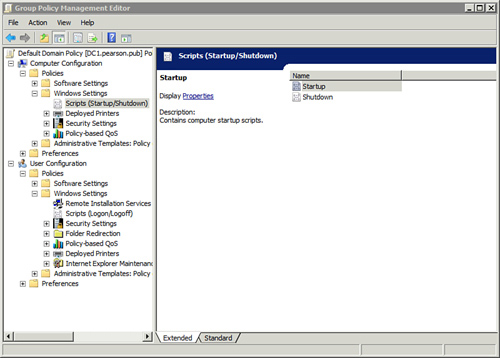
Figure 2 shows the locations of these GPO settings and the following table explains them.
| Group Policy Script Events | Comments |
|---|
| Computer Startup | The script runs when the computer starts.
The Group Policy setting for a domain GPO is in the Computer Configuration, Policies, Windows Settings, Scripts node. |
| Computer Shutdown | The script runs when the computer shuts down.
The Group Policy setting for a domain GPO is in the Computer Configuration, Policies, Windows Settings, Scripts node. |
| User logon | The script runs when the user logs on.
The Group Policy setting for a domain GPO is in the User Configuration, Policies, Windows Settings, Scripts node. |
| User logoff | The script runs when the user logs off.
The Group Policy setting for a domain GPO is in the User Configuration, Policies, Windows Settings, Scripts node. |
Scripts can run either synchronously or asynchronously.
| Script Behavior Types | Comments |
|---|
| Synchronous | Scripts run one after the other.
Users cannot interact with the system until all scripts have completed. |
| Asynchronous | Multiple scripts run at the same time.
User can interact with system before the scripts have completed. |
All scripts run asynchronously by default on Windows
Server 2008 and Windows Server 2008 R2. This includes both computer
startup and user logon scripts.
Tip
The default behavior for computer startup and user
logon scripts before Windows Server 2008 was synchronous. Users could
not interact with the system until all scripts completed. However,
computers boot quicker with this set to asynchronous and the behavior
is changed in Windows Server 2008, Server 2008 R2, Windows Vista, and
Windows 7. You can modify the new default behavior if needed.