1. Identifying Operations Master Roles
There are many times when you need to know which server holds which operations master roles. You can get the answer from different graphical user interfaces. However, it’s much easier from the command line with the netdom tool (as netdom query fsmo). The following text shows the output within a domain named pearson.pub:
C:\> netdom query fsmo
Schema master DC1.pearson.pub
Domain naming master DC1.pearson.pub
PDC DC1.pearson.pub
RID pool manager DC1.pearson.pub
Infrastructure master DC1.pearson.pub
The command completed successfully.
Note
Operations master roles were previously called flexible single master operations (FSMO) roles.
2. Joining a Computer to a Domain
You can join a computer to a domain from the command prompt using the netdom join command. The following table shows the different switches available with the netdom join command. Each of these switches is used in the following command, which joins a computer named dc2 to a domain named pearson.pub:
C:\>netdom join dc2 /domain:pearson.pub /userd:[email protected] /passwordd:* /ou:"ou=sales,dc=pearson,dc=pub" /reboot:60
3. Verifying Trust Relationships
You can also use the netdom command to verify trust relationships. The basic syntax of the command is
netdom trust trusting_domain_name /domain:trusted_domain_name
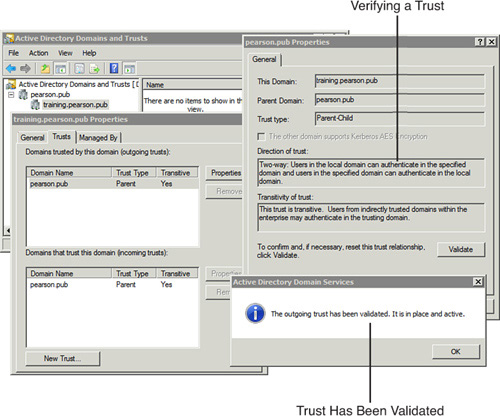
Figure 1 shows the Active Directory Domains and Trusts console with a parent domain (pearson.pub) and a child domain (training.pearson.pub). There is a parent/child trust relationship between the two domains. Furthermore, the outgoing trust has been validated.
Figure 1. Verifying a trust with Active Directory Domains and Trusts
Note
There are two trusts between the domains. The parent trusts the child and the child trusts the domain. These trusts are displayed as an outgoing trust and an incoming trust in Figure 1.
You can perform the same check from the command line with the following command:
netdom trust training.pearson.pub /domain:pearson.pub
The concept of trusted and trusting domains and the terminology can be confusing. Figure 2 shows two domains with a one-way trust between them. Notice that the arrow is pointing to Domain B. When shown this way, it indicates that Domain A trusts Domain B, and users in Domain B can be granted access to resources in Domain A. In other words, Domain B is trusted by Domain A.
Figure 2. One-way trust relationship between two domains

The following table identifies many of the switches that can be used with the netdom trust command to validate a trust.
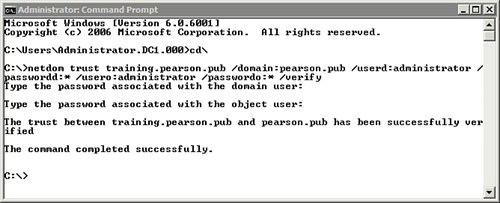
Figure 3 shows the result of entering the following command using some of these switches:
C:\>netdom trust training.pearson.pub /domain:pearson.pub /userd:administrator /passwordd:* /usero:administrator /passwordo:* /verify
Figure 3. Verifying a trust with the netdom command
3.12.11
If it’s a two-way trust, you can verify the trust from the other direction by swapping the trusted and trusting domains like the following command:
C:\>netdom trust pearson.pub /domain:training.pearson.pub /userd:administrator /passwordd:* /usero:administrator /passwordo:* /verify
4. Querying and Resetting Secure Channels with netdom
You can use the netdom command to query and verify secure channels between computers in the domain. When needed, you can use the netdom command to reset these channels.
Tip
Computers have passwords used to establish the secure channels. When the password kept on the system doesn’t match the password kept in the domain, the secure channel is broken. This can happen when the computer has been turned off for a long time, or after restoring Active Directory.
The basic command to query and verify the secure channel with computers in the domain is
netdom query server /verify
The following output shows the partial result of this command:
C:\> netdom query server /verify
Verifying secure channel setup for domain members:
Machine Status/Domain Domain Controller
======= ============= =================
\\SALES73 PEARSON \\DC1.PEARSON.PUB
\\SALES74 PEARSON \\DC1.PEARSON.PUB
\\WIN7PCG ERROR! ( The network path was not found. )
\\DC2 PEARSON \\DC1.PEARSON.PUB
\\PC-1 PEARSON \\DC1.PEARSON.PUB
\\SC1 PEARSON \\DC1.PEARSON.PUB
The command completed successfully.
Notice that the majority of these systems show the domain and the domain controller where the secure channel (trust relationship) has been verified. However, the \\win7pcg computer has a problem.
Note
Before resetting the trust, you should verify that the system is up and operational.
You can also check the channel with just a single computer using the following command:
netdom verify /d:domain computer-name
For example, the following listing shows how to verify the channel with a computer named dc2 in the pearson.pub domain, and the result:
C:\> netdom verify /d:pearson.pub dc2
The secure channel from DC2 to the domain PEARSON.PUB has been
verified. The connection is with the machine \\DC1.PEARSON.PUB.
The command completed successfully.
If the command fails, you can reset the secure channel between the domain and the computer with the following command:
netdom reset /d:domain computer-name
The following listing shows how to reset the secure channel with the computer named dc2 in the pearson.pub domain:
C:\> netdom reset /d:pearson.pub dc2
The secure channel from DC2 to the domain PEARSON.PUB has been reset.
The connection is with the machine \\DC1.PEARSON.PUB.
The command completed successfully.