Today, the Internet (and the world) is mostly
running on IPv4 networks. As more and more operating system and devices
natively support IPv6, and even require it, making IPv6 work globally
will quickly become necessary. Because IPv4 and IPv6 devices cannot
natively communicate with one another, protocols have been developed to
bridge the gap, and these are known as the IPv6 transition technologies.
Before discussing transition technologies, or
how we can make IPv6 devices communicate with IPv4 devices, we need to
examine the different types of nodes on the networks, as defined in RFC
2893:
• IPv4-only node—This
type of nodes uses IPv4 only and most likely does not even have the
IPv6 protocol installed. This is Windows XP and Windows Server 2003 and
earlier, by default, but IPv6 can be installed and configured on these
operating systems.
• IPv6/IPv4 node—This
is the typical node today, which has both IPv4 and IPv6 protocols
installed and uses both protocols. Windows Vista, Windows Server 2008
and later client and server operating systems are IPv6/IPv4 nodes.
• IPv6-only node—A
node that only has the IPv6 protocol installed and in use. In today’s
world, finding a node that fits this description is nearly impossible.
• IPv6 node—A node that uses IPv6, regardless of whether IPv4 is also used. This is a more generic term
• IPv4 node—A node that uses IPv4, regardless of whether IPv6 is also used. This is a more generic term.
Communication between
IPv4 and IPv6 devices does not directly occur. Devices need to
communicate using the same protocol. You can enable IPv6 devices to
communicate over IPv4 networks by using some form of tunneling, but
when IPv6/IPv4 nodes are in use on the same network and properly
addressed, they use transition technologies built in to the protocol
stack architectures. Windows XP and Windows Server 2003 use the dual
stack, and later operating systems (Windows Vista and Windows Server
2008 and later) leverage the dual layer. With the dual stack, when data
is prepared for the network, it is prepared for both protocols
separately, requiring more overhead within the operating system. With
the dual layer, the upper-stack layers are shared, thus reducing
overhead, and that is the architecture in use with the more recent
operating systems. Future releases will most likely do away with the
dual layer and move toward an IPv6-only stack. Figure 2 compares the dual stack and dual layer architectures.
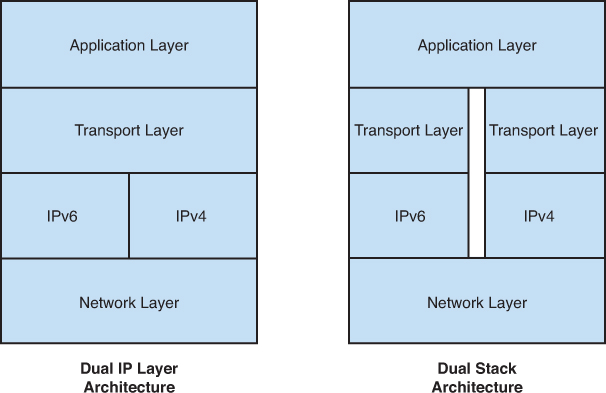
Figure 2. Dual IP layer and dual stack architectures.
IPv6 Tunneling
When IPv6 nodes are separated between IPv4
networks, they cannot directly communicate. To bridge the gap, the IPv6
nodes can tunnel through the IPv4 network. This tunneling can occur on
the host itself or through a designated IPv6 router tunneling router.
When IPv6 is tunneled through an IPv4 network, the IPv6 packet is
encapsulated within an IPv4 packet. Figure 3 shows an example of an encapsulated header.
Figure 3. IPv6 packet encapsulated in IPv4.
There are two different IPv6 tunnel
configurations. The first is a configured tunnel, in which the
endpoints and static routes for IPv6 traffic through an IPv4 network
are defined. The second is an automatic tunnel that is created based on
the IPv4 address of the device. The automatic tunnel can be leveraged
only on devices that are properly configured to
use both IPv6 and the IPv4. Configured tunnels, although these can be
created on local windows hosts, can also be configured on designated
routers to bridge the gap between IPv6-only devices on different
networks separated by IPv4 networks.
The ISATAP Tunneling Protocol
The Intra-Site Automatic Tunnel Addressing
Protocol (ISATAP) is an IPv6 transition technology used to allow
administrators to deploy IPv6 nodes on IPv4 networks. For ISATAP to be
used, an ISATAP router must be deployed and have a DNS record on the
local network. ISATAP is not intended for use across the Internet
(hence the user of intra-site as part of its name), but ISATAP traffic
must traverse an ISATAP router to allow an IPv6-only host to
communicate with IPv4 devices. The two main requirements for an ISATAP
network to function are an ISATAP router and, of course, ISATAP hosts:
• ISATAP router—An
ISATAP router advertises subnet prefixes assigned to the ISATAP
network, to ISATAP hosts, and the router forwards packets between the
IPv4 and IPv6 network.
• ISATAP hosts—ISATAP
hosts can communicate directly with ISATAP and IPv6 hosts on the local
network and with IPv4 hosts through the ISATAP router.
ISATAP addresses are automatically assigned
or created on ISATAP hosts, but before that occurs an ISATAP router
must be detected by a potential host. A router is detected when a host
can resolve the name ISATAP with a DNS lookup within their primary DNS
suffix, or through another form of short-name resolution. When an
ISATAP router is detected, an address is constructed based on the
address prefix provided by the ISATAP router, concatenated with the
local IP address of the ISATAP host. The ISATAP address is constructed
of the 64-bit IPv6 prefix already defined for the IPv6 network followed
by a 32-bit ISATAP designation and then by the 32-bit IPv4 address. For
example, with an IPv6 prefix of 2001:0dba:1234:5678::/64 for a host with an IPv4 address in a private network range, the address is as follows:
2001:0dba:1234:5678:0:5efe:w.x.y.z, where the w.x.y.z represents the IPv4 address
The 6to4 Tunneling Protocol
The 6to4 tunneling protocol provides
automatic address assignment and tunneling of IPv6 traffic across the
IPv4 Internet. This is mainly used when the host or client is connected
directly and assigned a public IPv4 Internet address, but can also be
used when a host has an IPv4 private address assigned. The 6to4 address
format uses an IPv6 global prefix because it is an IPv6 prefix that is
okay to route across the Internet. Figure 4 shows the 6to4 address format.
Figure 4. 6to4 IPv6 address format.
A 6to4 global address prefix is in the format
of 2002:WWXX:YYZZ::/48, where WWXX:YYZZ is the hexadecimal
representation of the public IP address. Each of the two letters
represents one of the 32-bit IPv4 octets. As an example of a 6to4
address converted, a public IP address of 72.34.113.11 is converted to
2002:4822:710b::/48.
The 6to4 network can include the following components:
• 6to4 host—A host that has both IPv4 and IPv6 and is configured with a 6to4 address in the IPv6 global address range of 2002::/16.
• 6to4 router—An IPv6/IPv4 forwards traffic between 6to4 hosts on the local network to other 6to4 routers and to 6to4 relay routers.
• 6to4 relay—Forwards 6to4 traffic between the IPv4 Internet and IPv6-only devices directly connected to the Internet.
The Teredo Tunneling Protocol
The Teredo IPv6 transition technology is
commonly used when the client system is assigned a private IP address
and a 6to4 network is not enabled or preferred. One of the biggest
advantages of Teredo over 6to4 is that 6to4 is not so NAT friendly when
traversing the Internet and each endpoint needs to have a public IPv4
address. Also, 6to4 traffic has a reasonably high failure rate because
the packets are encapsulated and marked with protocol field 41, which
is unknown to many firewalls, and unknown protocols are usually blocked
by default. Also, using the public Internet, end users cannot control how
many NAT traversals (NAT-T) the packets must go through from the
sources to the destination, making 6to4 not so resilient to support
routing through NATs. This is where Teredo (IPv6 NAT-T) becomes the
preferred tunneling protocol. RFC 4380 describes the Teredo tunneling
protocol. Teredo makes its way around the NAT challenge by changing the
way the IPv6 packet is encapsulated. With the ISATAP and 6to4 tunneling
protocols, the IPv6 packet is encapsulated within an IPv4 packet, and
the header IP protocol field is set to a value of 41 to identify
tunnelled traffic. Teredo tunnels Ipv6 over Ipv4 differently as the
IPv6 packet are encapsulated and sent within an IPv4 User Datagram
Protocol (UDP) packet that easily gets through NAT traversals. But, the
Teredo protocol is considered the protocol of last resort, mainly
because of the high overhead associated with the encapsulation
mechanism, but also because of security concerns. Teredo basically
allows hosts to directly traverse NATs to communicate across the
Internet with other Teredo hosts using what is referred to as
open-ended tunnels. Because of the way the Teredo protocol encapsulates
Ipv6 traffic within Ipv4 UDP packets, it can essentially bypass some of
the strict traffic inspection performed by network firewalls and
intrusion prevention system (IPS). This leaves the burden of validating
the Ipv6 traffic to the Teredo host receiving the data. This might not
be the most secure or ideal scenario and in cases where Teredo must be
used, network administrators should fully understand Teredo security
risks and how to mitigate them.
Until a true IPv6 Internet is configured,
there will be security and functionality challenges to make IPv6 work
on both the internal network and across the Internet. In some ways,
having the transition technologies in place slows down the larger ISPs’
adoption of an Ipv6 Internet.