The ultimate goal of
implementing least privilege is reducing the permissions of user and
service accounts to the absolute minimum required. Doing this can be
difficult and requires considerable planning. This section focuses on
this goal from four perspectives:
Separating Windows and database administrator privileges
Reducing the permissions of the SQL Server service accounts
Using proxies and credentials to limit the effective permissions of SQL Server Agent jobs
Using role-based security to simplify and tighten permissions management
Let's begin with a contentious issue: separating and limiting the permissions of DBAs and Windows administrators.
1. Windows and DBA privilege separation
Removing the local admin group membership from a
DBA is almost always likely to provoke a strong response. Most DBAs
take it as a personal insult, akin to not being trusted with basic
tasks. When questioned about whether Windows administrators should be
SQL Server sysadmins, the response is typically as passionate, with the
DBAs usually unaware of their own contradiction!
In most cases, DBAs don't need to be local
administrators to do their job. Not only that, they shouldn't be.
Equally true, Windows administrators shouldn't be SQL Server sysadmins.
Separation of powers in this manner is a basic
security concept, but probably the most commonly abused one. The reasons
for this are many and varied. First, in previous versions of SQL Server
(2005 and earlier) the BUILTIN\Administrators group is automatically
added to the SQL Server sysadmins server role, making Windows
administrators effectively DBAs by default. Second, DBAs are often
tasked (particularly in smaller environments) with being the Windows
administrator as well as the DBA. And third, to avoid dealing with
Windows administrators to get things done, some DBAs will come up with
various reasons why they should be local administrators, often
bamboozling management into submission.
|
If all of the Windows logins and/or groups that
are in the sysadmin server role be accidentally (or deliberately)
removed and the SA password is unknown, system administrators can be
effectively locked out from performing SQL Server sysadmin tasks. In
such an event, the instance can be started in single-user mode using the
-m or -f options by a user with membership in the
local administrators group (rather than reinstalling SQL Server and
reattaching databases). When started in this manner, the user connecting
to SQL Server will connect as part of the sysadmin role and can add the
necessary logins and/or groups back to the sysadmin role. Be careful
when using this method to ensure the SQL Agent service is stopped so
that it doesn't connect first and prevent further connections.
|
Why separate permissions? Well, a Windows
administrator with very little DBA experience could accidentally delete
critical data or entire databases without realizing it. Or a DBA, after
accessing sensitive data, could cover his or her tracks by deleting
audit files from the operating system.
There are obviously many more examples, all of
which require separation of powers to protect against both deliberate
and accidental destructive actions.
Continuing the theme of least privilege, the SQL Server service accounts shouldn't be members of the local administrators group.
2. SQL Server service account permissions
A common SQL Server myth is that the accounts
used by the SQL Server services need to be members of the local
administrators group. They don't, and in fact shouldn't be. During
installation, SQL Server will assign the necessary file, registry, and
system permissions to the accounts nominated for the services.
The need to avoid using local administrator
accounts (or the localsystem account) is based on the possibility of the
server being compromised and used to run OS-level commands using tools
such as xp_cmdshell, which is disabled by default. While other
protections should be in place to prevent such attacks, locking down all
possible avenues of attack is best practice, and using nonprivileged
service accounts is an important part of this process.
Separate accounts should be used for each SQL Server service to enable
the most granular security permissions. Finally, should the security
account be changed postinstallation, the SQL Server Configuration
Manager tool should be used, rather than a direct assignment using the
Control Panel services applet. When you use the Configuration Manager
tool, SQL Server will assign the new account the necessary permissions
as per the initial installation.
Like all items in this section, configuring
nonadministrator accounts for SQL Server services is about assigning the
minimal set of privileges possible. This is an important security
concept not only for service accounts but for all aspects of SQL Server,
including SQL Server Agent jobs.
3. SQL Server Agent job permissions
A common requirement for SQL Server deployments is for SQL Server Agent jobs
to access resources outside of SQL Server. Among other tasks, such jobs
are typically used for executing batch files and Integration Services
packages.
To enable the minimum set of permissions to be
in place, SQL Server Agent enables job steps to run under the security
context of a proxy. One or more proxies are created as required, each of which uses a stored credential.
The combination of credentials and proxies enables job steps to run
using a Windows account whose permissions can be tailored (minimized)
for the needs of the Agent job step.
In highlighting how proxies and credentials are
used, let's walk through a simple example of setting minimal permissions
for a SQL Agent job that executes an Integration Services package.
We'll begin this process by creating a credential.
Credentials
When you create a SQL Agent proxy, one of the
steps is to specify which credential the proxy will use. We'll see that
shortly. It follows that before creating the proxy, the credential
should be created. Figure 1
shows an example of the creation of a credential in SQL Server
Management Studio. You access this dialog by right-clicking Credentials
under Security and choosing New Credential.
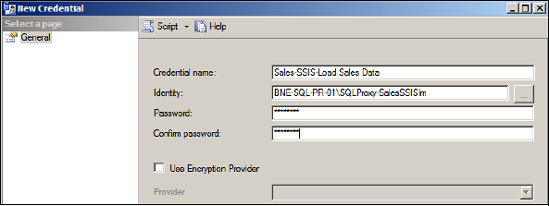
In figure 1, we've specified the SQL Proxy-SalesSSISIm account, whose permissions
have been reduced to the minimum required for executing our Integration
Services package. For example, we've granted the account read
permissions to a directory containing files to import into the database.
In addition to setting permissions at a domain/server level, we'd add
this credential as a SQL login with the appropriate database
permissions.
After creating the credential, we can now create the proxy.
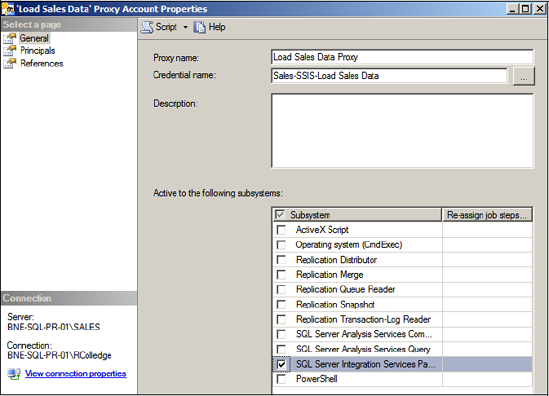
Proxies
You create a SQL Agent proxy in SQL Server
Management Studio by right-clicking Proxies under SQL Server Agent and
choosing New Proxy. The resulting screen, as shown in figure 2,
allows you to specify the details of the proxy, including the name, the
credential to use, and which subsystems the proxy can access. In our
case, we'll use the credential we created earlier, and grant the proxy
access to the SQL Server Integration Services (SSIS) Package subsystem.
Members of the sysadmin group have access to all
proxies. The Principals page enables non-sysadmin logins or server
roles to be granted access to the proxy, thereby enabling such users to
create and execute SQL Agent jobs in the context of the proxy's
credential.
With the proxy created, we can now create a SQL Agent job that uses it.
SQL
Agent job steps
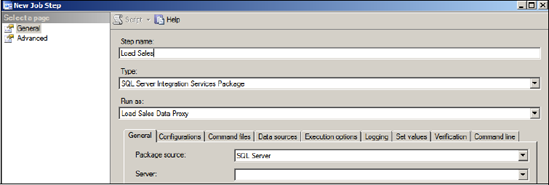
When you create a SQL Server Agent job, one of
the selections available for each job step is choosing its execution
context, or Run As mode. For job steps that perform actions at the
operating system level, you have two options for the Run As mode: SQL
Agent Service Account or Proxy. As shown in figure 3, we've created a SQL Agent job with a job step called Load Sales that uses the Load Sales Data Proxy that we created earlier.
The end result of such a configuration is that
the effective permissions of the Load Sales job step are those of the
proxy's credential, which is restricted to the requirements of the SSIS
package and nothing more, and therefore meets the least privilege
objective. Additional SQL Agent jobs and their associated steps can use
the Load Sales Data proxy, or have specific proxies created for their
unique permission requirements, all without needing to alter the
permissions of the service account used for SQL Server Agent.
It's important to note that T-SQL job steps
continue to run in the context of the SQL Agent job owner. The
proxy/credential process I've described is specific to job steps
accessing resources outside of SQL Server.
The ability to create multiple proxies for
specific job types and with individual credentials and permissions
allows you to implement a powerful and flexible permissions
structure—one that conforms to the principles of least privilege.
In finalizing our
coverage of least privilege, let's turn our attention to how user's
permissions are secured within a server and database using role-based
security.