Regardless of the number of domains you have in your
environment, you always have a tree and a forest. This might surprise
those of you who generally think of domain trees and forests as
belonging only to Active Directory environments that consist of
multiple domains. However, recall that when you install the first
domain in an Active Directory environment, that domain automatically
creates a new forest and a new tree.
In the following sections, you will learn
how to plan trees and forests as well as see how to promote domain
controllers to establish a tree and forest environment.
1. Planning Trees and Forests
You have already seen several reasons why you might
want to have multiple domains within a single company. What you haven't
yet seen is how multiple domains can be related to each other and how
their relationships can translate into domain forests and trees.
A fundamental commonality between the various
domains that exist in trees and forests is that they all share the same
Active Directory Global Catalog (GC) This means that if you modify the
Active Directory schema, these changes must be propagated to all of the
domain controllers in all of the domains. This is an important point
because adding and modifying the structure of information in the GC can
have widespread effects on replication and network traffic. Also, you
need to ensure that any system you use in the GC role can handle it—you
might need to size up the system's hardware requirements. This is
especially true if there are multiple domains.
Every domain within an Active Directory
configuration has its own unique name. For example, even though you
might have a sales domain in two different trees, the complete names
for each domain will be different (such as sales.stellacon1.com and sales.stellacon2.com).
In the following sections, you'll look at how you can organize multiple Active Directory domains based on business requirements.
1.1. Using a Single Tree
The concept of domain trees was created to preserve
the relationship between multiple domains that share a common
contiguous namespace. For example, you might have the following DNS
domains (based on Internet names):
Note that all of these domains fit within a single
contiguous namespace. That is, they are all direct or indirect children
of the mycompany.com domain. In this case, mycompany.com is called the root domain. All of the direct children (such as sales.mycompany.com and engineering.mycompany.com) are called child domains. Finally, parent domains are the domains that are directly above one domain. For example, sales.mycompany.com is the parent domain of europe.sales.mycompany.com. Figure 1 provides an example of a domain tree.
In order to establish a domain tree, you must create
the root domain for the tree first. Then you can add child domains off
this root. These child domains can then serve as parents for further
subdomains. Each domain must have at least one domain controller, and
domain controllers can participate in only one domain at a time.
However, you can move a domain controller from one domain to another.
To do this, you must first demote a domain controller to a member
server and then promote it to a domain controller in another domain.
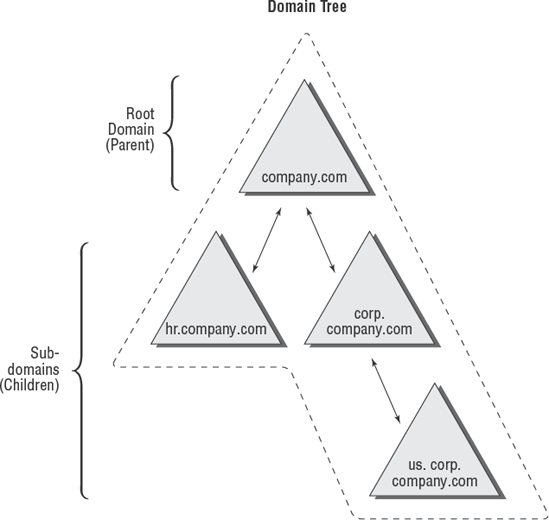
Domains are designed to be security boundaries. The
domains within a tree are, by default, automatically bound together
using a two-way transitive trust relationship, which allows resources
to be shared among domains through the use of the appropriate user and
group assignments. Because trust relationships are transitive, all of
the domains within the tree trust each other. Note, however, that a
trust by itself does not automatically grant any security permissions
to users or objects between domains. Trusts are designed only to allow
resources to be shared; you must still go through the process of
sharing and managing them. Administrators must explicitly assign
security settings to resources before users can access resources
between domains.
Using a single tree makes sense when your
organization maintains only a single contiguous namespace. Regardless
of the number of domains that exist within this environment and how
different their security settings are, they are related by a common
name. Although domain trees make sense for many organizations, in some
cases, the network namespace may be considerably more complicated.
You'll look at how forests address these situations next.
1.2. Using a Forest
Active Directory forests are designed to accommodate
multiple noncontiguous namespaces. That is, they can combine domain
trees together into logical units. An example might be the following
tree and domain structure:
Tree: Organization1.com
Sales.Organization1.com
Marketing.Organization1.com
Engineering.Organization1.com
NorthAmerica.Engineering.Organization1.com
Tree: Organization2.com
Figure 2
provides an example of how multiple trees can fit into a single forest.
Such a situation might occur in the acquisition and merger of companies
or if a company is logically divided into two or more completely
separate and autonomous business units.
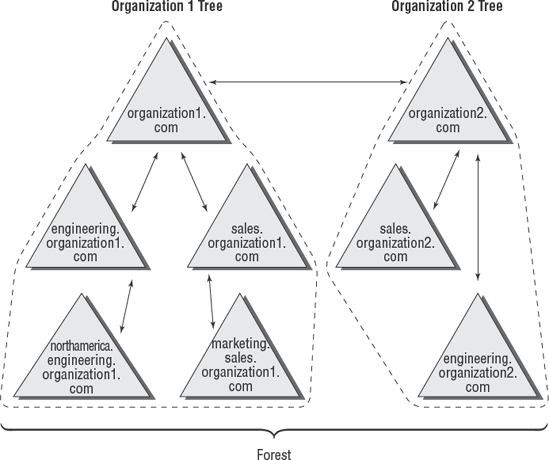
All of the trees within a forest are related through
a single forest root domain. This is the first domain that was created
in the Active Directory environment. The root domain in each tree
creates a transitive trust with the forest root domain. The result is a
configuration in which all of the trees within a domain and all of the
domains within each tree trust each other. Again, as with domain trees,
the presence of a trust relationship does not automatically signify
that users have permissions to access resources across domains. It only
allows objects and resources to be shared. Authorized network
administrators must set up specific permissions.
All of the domains within a single Active Directory forest have the following features in common:
Schema
The schema is the Active Directory structure
that defines how the information within the data store is structured.
For the information stored on various domain controllers to remain
compatible, all of the domain controllers within the entire Active
Directory environment must share the same schema. For example, if you
add a field for an employee's benefits plan number, all domain
controllers throughout the environment need to recognize this
information before you can share information among them.
Global Catalog (GC)
One of the problems associated with working in
large network environments is that sharing information across multiple
domains can be costly in terms of network and server resources.
Fortunately, Active Directory uses the GC, which serves as a repository
for information about a subset of all objects within all
Active Directory domains in a forest. Systems administrators can
determine what types of information should be added to the defaults in
the GC. Generally, they decide to store commonly used information, such
as a list of all of the printers, users, groups, and computers. In
addition, they can configure specific domain controllers to carry a
copy of the GC. Now, if you have a question about, for example, where
to find all the color printers in the company, all you need to do is to
contact the nearest GC server.
Configuration information
Some roles and functions must be managed for the
entire forest. When you are dealing with multiple domains, this means
that you must configure certain domain controllers to perform functions
for the entire Active Directory environment.
The main purpose of allowing multiple
domains to exist together is to allow them to share information and
other resources. Now that you've seen the basics of domain trees and
forests, take a look at how domains are actually created.
2. The Promotion Process
A domain tree is created when a new domain is added
as the child of an existing domain. This relationship is established
during the promotion of a Windows Server 2008 computer to a domain
controller. Although the underlying relationships can be quite
complicated in larger organizations, the Active Directory Installation Wizard (DCPROMO) makes it easy to create forests and trees.
Using the Active Directory Installation
Wizard, you can quickly and easily create new domains by promoting a
Windows Server 2008 stand-alone server or a member server to a domain
controller. When you install a new domain controller, you can choose to
make it part of an existing domain, or you can choose to make it the
first domain controller in a new domain. In the following sections and
exercises, you'll become familiar with the exact steps you need to take
to create a domain tree and a domain forest when you promote a server
to a domain controller.