1. Share Permissions vs. File Permissions
There are two kinds of permissions involved in any shared
folder—those on the actual share and those imposed by the underlying
file system. These permissions are subtractive.
This means that the most restrictive permission will win. Managing
permissions on both the share and the file system at the same time can
often be quite confusing, and it’s difficult to keep track of the
details of both. We generally recommend using the underlying NTFS file
permissions to control access and setting the share permissions to Full Control for everyone for most
normal shares. The NTFS file permissions give much greater granularity
and control over exactly what level of access is granted. However, in
some cases using a more restrictive share permission is useful. When
you do use a more restrictive share permission, indicate in the share
name that the share is restricted.
Whatever your choice, avoid configuring both share permissions
and NTFS permissions because the result can be
unpredictable and hard to troubleshoot.
1.1. Share Permissions
Windows SBS provides easy ways to share folders. After a
folder is shared, restrictions can be added or removed in the form
of share permissions. These permissions apply
only at the folder level—not at the file level—and are limited to
allowing or denying Full Control, Read, and Change. Table 1 summarizes the three types
of access, from most restrictive to least restrictive.
Table 1. Types of share permissions
| SHARE PERMISSION | TYPE OF ACCESS |
|---|
| Read | Allows viewing of file and subfolder names,
viewing data in files, and running programs |
| Change | Allows the access under Read, plus allows
adding files and subdirectories to the shared folder,
changing data in files, and deleting files and
subdirectories |
| Full Control | Allows all the access under Change, plus allows
changing permissions and taking ownership |
Share permissions determine the maximum access allowed
over the network. They don’t affect a user who logs on locally or a
Remote Desktop user of the computer where the shared folders are
stored.
1.2. File Permissions
File permissions are also called NTFS
permissions, and the terms are used interchangeably. File
permissions, unlike share permissions, control user access
regardless of where it originates. Local users, Terminal Services users, and network users are
all treated equally.
File permissions can be set on folders and even down to
individual files. This means that for any file, you can give
individual users different types of access. Although you
can set such detailed permissions, avoid doing
so. Always try to operate with the simplest possible permissions.
Set as few restrictions as possible. Assign permissions to groups,
not individuals. Simplify, simplify, simplify. Your life will be
easier in both the short and long term.
For many years, various smarty-pants types (including
ourselves) have been warning administrators not to do everything
using the Administrator account. Save that account for when you
need it, we said. Use a standard user account most of the time, we
implored. Of course, no one paid the slightest bit of attention,
and here’s the inevitable result: User Account Control.
User Account Control (UAC) is a security feature introduced in Windows
Vista that then became a component of the Windows Server 2008
operating system, and hence, a component of Small Business Server.
It’s based on the security theory of least privilege. The idea is
that users should have the absolute minimum privilege necessary to
perform assigned tasks. This might sound as though it contradicts
our advice to operate with the simplest possible permissions, but
in fact it does not. Shares and permissions remain the best way to
allow or restrict access to files and folders.
The goal of UAC is to reduce the exposure of the operating
system by requiring users to run in standard user mode, minimizing
the ability of users to make changes that could destabilize their
computers or expose the network to undetected virus infections on
their computers.
Prior to Windows Vista, the Windows usage model has been one
of assumed administrative rights. Software developers assumed
their programs could access and modify any file, registry key, or operating system setting.
Even when Windows NT introduced security and differentiated
between granting access to administrative and standard user
accounts, users were guided through a setup process that
encouraged them to use the built-in Administrator account or one
that was a member of the Administrators group. A second problem is
that even standard users sometimes need to perform tasks that
require administrative rights, such as installing software and
opening ports in the firewall.
The UAC solution is to require administrative rights less
frequently, enable legacy applications to run with standard user
rights, make it easier for standard users to access administrative
rights when they need them, and enable administrative users to run
as if they were standard users.
2. NTFS Permissions
The ability to assign enforceable permissions to files and
folders is part of the NTFS file system. If you assign NTFS permissions, you
need to understand how they work and how they are different for a file
and for the folder that contains the file.
2.1. What Permissions Mean
NTFS permissions affect access both locally and remotely.
Share permissions, on the other hand, apply only to network shares
and don’t restrict access on the part of any local user (or terminal
server user) of the computer on which you’ve set the share
permissions. Windows 2008 Server has a set of standard folder
permissions that are combinations of specific kinds of access. The
individual permissions are Full Control, Modify, Read & Execute,
List Folder Contents, Read, and Write. Each of these permissions
consists of a group of special permissions. Table 2 shows the special
permissions and the standard permissions to which they apply.
Table 2. Special permissions for folders
| SPECIAL PERMISSION | FULL CONTROL | MODIFY | READ & EXECUTE | LIST FOLDER CONTENTS | READ | WRITE |
|---|
| Traverse Folder/Execute File | Yes | Yes | Yes | Yes | No | No |
| List Folder/Read Data | Yes | Yes | Yes | Yes | Yes | No |
| Read Attributes | Yes | Yes | Yes | Yes | Yes | No |
| Read Extended Attributes | Yes | Yes | Yes | Yes | Yes | No |
| Create Files/Write Data | Yes | Yes | No | No | No | Yes |
| Create Folders/Append Data | Yes | Yes | No | No | No | Yes |
| Write Attributes | Yes | Yes | No | No | No | Yes |
| Write Extended Attributes | Yes | Yes | No | No | No | Yes |
| Delete Subfolders and Files | Yes | No | No | No | No | No |
| Delete | Yes | No | No | No | No | No |
| Read Permissions | Yes | Yes | Yes | Yes | Yes | Yes |
| Change Permissions | Yes | No | No | No | No | No |
| Take Ownership | Yes | No | No | No | No | No |
File permissions include Full Control,
Modify, Read & Execute, Read, and Write. As with folders, each
of these permissions controls a group of special permissions. Table 3 shows the special
permissions associated with each standard permission.
Table 3. Special permissions for files
| SPECIAL PERMISSION | FULL CONTROL | MODIFY | READ & EXECUTE | READ | WRITE |
|---|
| Traverse Folder/Execute File | Yes | Yes | Yes | No | No |
| List Folder/Read Data | Yes | Yes | Yes | Yes | No |
| Read Attributes | Yes | Yes | Yes | Yes | No |
| Read Extended Attributes | Yes | Yes | Yes | Yes | No |
| Create Files/Write Data | Yes | Yes | No | No | Yes |
| Create Folders/Append Data | Yes | Yes | No | No | Yes |
| Write Attributes | Yes | Yes | No | No | Yes |
| Write Extended Attributes | Yes | Yes | No | No | Yes |
| Delete Subfolders and Files | Yes | No | No | No | No |
| Delete | Yes | Yes | No | No | No |
| Read Permissions | Yes | Yes | Yes | Yes | Yes |
| Change Permissions | Yes | No | No | No | No |
| Take Ownership | Yes | No | No | No | No |
Warning:
IMPORTANT Groups or users
granted Full Control on a folder can delete any files and
subfolders, no matter what the permissions are on the individual
files or subfolders. Any user or group assigned Take Ownership can
become the owner of the file or folder and then change permissions and
delete files or even entire subfolder trees, no matter what the
permissions were before that user or group became the
owner.
2.2. How Permissions Work
If you take no action at all, the files and folders inside a
shared folder have the same permissions as the share. Permissions
for both directories and files can be assigned to the
following:
Groups and individual users on this domain
Global groups, universal groups, and individual users from
domains that this domain trusts
Special identities, such as Everyone and Authenticated
Users
The important rules for permissions can be summarized as
follows:
By default, a folder inherits permissions from its parent
folder. Files inherit their permissions from the folder in which
they reside.
Users can access a folder or file only when they are granted permission to do
so or they belong to a group that has been granted
permission.
Permissions are cumulative, but the Deny permission trumps
all others. For example, if the Sales group has Read access to a folder and the Finance group has
the Modify permission for the same folder, and Wally
is a member of both groups, Wally has the higher level of
permission, which is Modify. However, if the Sales group
permission is changed to explicitly Deny, Wally is unable to use
the folder, despite his membership—and ostensibly higher level
of access—in the Finance group.
Explicit permissions take precedence over inherited permissions. Inherited Deny will not
prevent access if an object has an explicit Allow
permission.
The user who creates a file or folder owns the object and can set
permissions to control access.
An administrator can take ownership of any file or folder.
2.3. Considering Inheritance
Just to complicate matters a bit more, there are two types of
permissions: explicit and inherited. Explicit
permissions are the ones you set on files or folders you create.
Inherited permissions are those that flow from
a parent object to a child object. By default, when you create a
file or a subfolder, it inherits the permissions of
the parent folder. If the Allow and Deny boxes are shaded when you
view the permissions for an object, the permissions are
inherited.
If you don’t want the child objects to inherit the permissions
of the parent, you can block inheritance at the parent level or
child level. Where you block inheritance is
important. If you block at the parent level, no subfolders will
inherit permissions. If you block selectively at the child level,
some folders will inherit permissions and others will not.
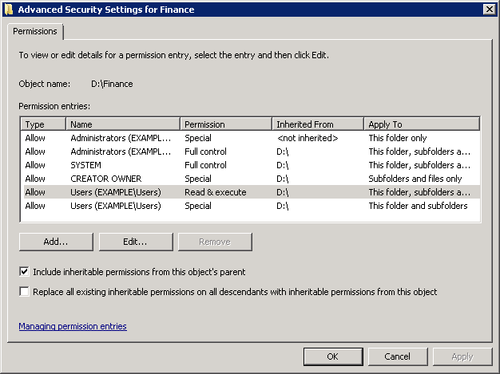
To make changes to inherited permissions, follow these
steps:
Right-click the folder and select Properties.
Click the Security tab and then click Advanced.
On the Permissions tab of the Advanced Security Settings
For dialog box, highlight the permission you want to change and
click Edit.
Clear the check box for Include Inheritable Permissions
From This Object’s Parent. (See Figure 1.)
You’ll be given the option to copy existing permissions to the
object or to remove all inherited permissions. The object will no
longer inherit permissions from the parent object, and you can
change permissions or remove users and groups from the Permissions
list.
You can also change inherited permissions by changing the permissions of the parent
folder or by explicitly selecting the opposite permission—Allow or
Deny—to override the inherited permission.