|
Security is a very real
concern for any computer connected to a network or the Internet. There
are three main categories of security threats:
A deliberate, targeted attack through your Internet connection
Ironically, this is the type
of attack most people fear, but realistically, it's the least likely to
occur, at least where home and small-office networks are concerned.
It's possible for a so-called hacker to obtain access to your computer,
either through your Internet connection or from another computer on your
local network; it's just not terribly likely that such a hacker will
bother.
An automated invasion by a virus, worm, Trojan horse, or robot
A virus
is simply a computer program that is designed to duplicate itself with
the purpose of infecting as many computers as possible. If your computer
is infected by a virus, it may use your network connection to infect
other computers; likewise, if another computer on your network is
infected, your computer is vulnerable to infection. The same goes for
Internet connections, although the method of transport in this case is
typically an infected email message. There also exist so-called robots,
programs that are designed to scan large groups of IP addresses,
looking for vulnerabilities. The motive for such a program can be
anything from exploitation of credit card numbers or other sensitive
information to the creation of a "zombie," a PC that has been hijacked
for the purpose of distributing spam, viruses, or extreme right-wing
propaganda. Finally, a Trojan horse
is a program that works somewhat like a virus, except that its specific
purpose is to create vulnerabilities in your computer that can
subsequently be exploited by a hacker or robot. For example, a program
might open a port on your computer and then communicate with a remote system to announce its presence.
A deliberate attack by a person sitting at your computer
A person who sits down at
your computer can easily gain access to sensitive information, including
your documents, email, and even various passwords stored by your web
browser. An intruder can be anyone, from the jerk who has just stolen
your laptop, to a coworker casually walking by your unattended desk, to
your eight-year-old niece. Naturally, it's up to you to determine the
actual likelihood of such a threat and to take the appropriate measures
(such as password-protecting your screen saver, or hiding your keyboard
in the closet).
Defending your computer (and your network) against these attacks essentially involves fixing the vulnerabilities they exploit. 1. Close Vista's BackdoorsWindows
Vista includes several features that will enable you to implement a
reasonable level of security without purchasing additional software or
hardware. Unfortunately, few of these features are in effect by default. The following steps will help you close some of these "backdoors":
Sharing Wizard bad.
One of the main reasons to
set up a workgroup is to share files and printers with other computers.
But it's wise to share only those folders that need to be shared, and
disable sharing for all others. A feature called Simple File Sharing,
which might allow anyone, anywhere, to access your personal files
without your knowledge, is turned on by default. In Control Panel, open
Folder Options, choose the View tab, and turn off the Use Sharing Wizard (Recommended) option.
UPnP bad.
Another feature, called
Universal Plug-and-Play (UPnP), can open additional vulnerabilities on
your system. UPnP could more aptly be called Network Plug and Play,
since it only deals with network devices. UPnP is a collection of
standards that allow such devices to announce their presence to UPnP
servers on your network, much in the same way as your PnP sound card
announces its presence to Windows when you boot your system. Windows
supports UPnP out of the box, which, on the surface, sounds like a good
idea. However, UPnP is a service that most users don't need, and unless
you specifically need to connect to a UPnP device on your network, you
should disable UPnP on your system immediately. Leaving a service like UPnP running unnecessarily exposes your system to several security threats. To disable UPnP, open the Services window (services.msc). Find the SSDP Discovery Service in the list and double-click it. Click Stop to stop the service and change the Startup type to Disabled to prevent it from loading the next time Windows starts. Click OK and then do the same for the UPnP Device Host. Close the Services window when you're done.
Remote Desktop good, but only when you need it.
The Remote Desktop feature, is enabled by default in the Windows Vista
Business and Ultimate editions. Unless you specifically need this
feature, it should be disabled. In Control Panel, open System and then
click the Remote settings link on the left. In the Remote tab of the System Properties window, turn off the Allow Remote Assistance connections to this computer option, and select the Don't allow connections to this computer option, beneath it.
Passwords good.
Make sure each and every
user account on your system has a unique password. Even though you may
not be concerned about security among users, unprotected accounts can be
exploited by an attack over a network.
Firewall good, sometimes.
Set up a firewall, as
described in the next section, to further protect your computer by
strictly controlling network traffic into and out of your computer.
Open ports bad.
2. The Security Center and the FirewallThe Windows Security Center, shown in Figure 1,
is a central page in Control Panel used to keep tabs on the Windows
Firewall, Windows Defender, User Account Control, and automatic
updating. It also monitors your antivirus software, but for purely political and marketing reasons, Windows Vista includes no antivirus functionality of its own. 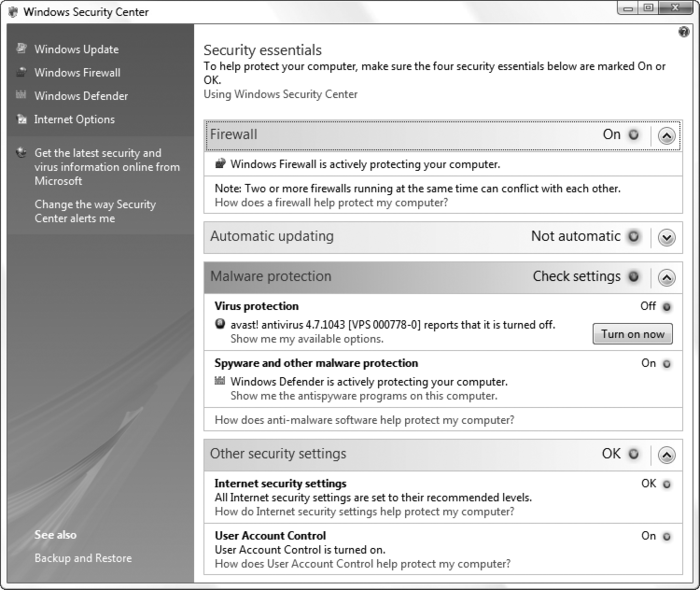
There
are two problems with the Windows Security Center. First, its alerts
can be particularly repetitive and annoying (this is intentional).
Second, it doesn't actually do that much to protect your PC
(unfortunately, this is also intentional). Above
all, the Security Center is a monitoring tool. If it sees that a
particular feature is turned on (whether or not it's doing its job), the
Security Center is happy, and you won't see any options in that
section. Otherwise, you'll have the option of fixing the "problem" by
clicking a big, friendly button (e.g., Turn on now). Or, to stop monitoring a specific feature, click the Show me my available options link. Click the Change the way Security Center alerts me
link to the left to choose what happens when the Security Center finds a
problem. To effectively turn off the Windows Security Center (or more
accurately, take away its only power), click Don't notify me and don't display the icon here. Or, if you feel that's too severe, click Don't notify me, but display the icon; that way, you'll know if there's a problem, but Security Center won't interrupt you to tell you. See the "Disable the Security Center" sidebar, next, for another solution. |
|
If
you find that the Security Center is hassling you with unnecessary
scans and warning messages, despite the fact that you've asked it not
to, your only resort may be to disable it completely. Here's how to do
it: Open the Services window (services.msc). Locate Security Center in the list, double-click it, and change the Startup type to Disabled. Click OK and close the Services window when you're done.
Note
that this doesn't actually disable the firewall, antivirus, or
automatic update features you may have employed, only the "monitoring"
effects of the Windows Security Center. |
Click the colored ribbons to expand or collapse each section:
Firewall
You can't actually change any firewall settings here; click the Windows Firewall link on the left to configure Windows' built-in firewall feature, discussed in the next section.
Automatic updating
The Automatic Updates
feature is responsible for periodically contacting Microsoft to see
whether new updates to Windows (and optionally, other installed
Microsoft products) are available. Open Windows Update in Control Panel
to change this setting. In
its most automated mode (Microsoft's recommended setting), Windows
downloads and installs so-called "high priority" updates automatically.
Malware protection
This section actually monitors two areas: Virus protection, which is the only feature not included with Windows Vista, and Spyware and other malware protection, which is handled by Windows Defender (and turned on by default). The
Security Center has been known to initiate virus scans unnecessarily,
including—for some users—every time Windows starts. Even if you already
have Security Center-aware antivirus software installed, you may wish to
disable monitoring for this reason. Click the Show me my available options link and then click I have an antivirus program that I'll monitor myself, and the antivirus status will change to Not monitored. |
|
Other security settings
This section also includes two entries: Internet security settings (despite the name, these only apply to Internet Explorer; click the Internet Options link on the left to change them) and User Account Control.
Now,
if you're the forgetful type, it's best to leave all of the alerts and
warnings in the Windows Security Center intact. But if you're annoyed by
all the messages, and have taken the time to secure your PC yourself,
then you may feel safe scaling back the Security Center's reach.
|