For the most part, domain controllers
handle the replication processes automatically. However, systems
administrators still need to monitor the performance of Active
Directory replication, since failed network links and incorrect
configurations can sometimes prevent the synchronization of information
between domain controllers.
You can monitor the behavior of Active Directory replication and troubleshoot the process if problems occur.
1. About System Monitor
The Windows Server 2008 System Monitor
administrative tool was designed so that you can monitor many
performance statistics associated with using Active Directory. Included
within the various performance statistics that you may monitor are
counters related to Active Directory replication.
2. Troubleshooting Replication
A common symptom of replication problems is that
information is not updated on some or all domain controllers. For
example, a systems administrator creates a User account on one domain
controller, but the changes are not propagated to other domain
controllers. In most environments, this is a potentially serious
problem because it affects network security and can prevent authorized
users from accessing the resources they require.
You can take several steps to troubleshoot Active Directory replication; each of these is discussed in the following sections.
2.1. Verifying Network Connectivity
In order for replication to work properly in
distributed environments, you must have network connectivity. Although
ideally all domain controllers would be connected by high-speed LAN
links, this is rarely the case for larger organizations. In the real
world, dial-up connections and slow connections are common. If you have
verified that your replication topology is set up properly, you should
confirm that your servers are able to communicate. Problems such as a
failed dial-up connection attempt can prevent important Active
Directory information from being replicated.
2.2. Verifying Router and Firewall Configurations
Firewalls are used to restrict the types of traffic
that can be transferred between networks. They are mainly used to
increase security by preventing unauthorized users from transferring
information. In some cases, company firewalls may block the types of
network access that must be available in order for Active Directory
replication to occur. For example, if a specific router or firewall
prevents data from being transferred using SMTP, replication that uses
this protocol will fail.
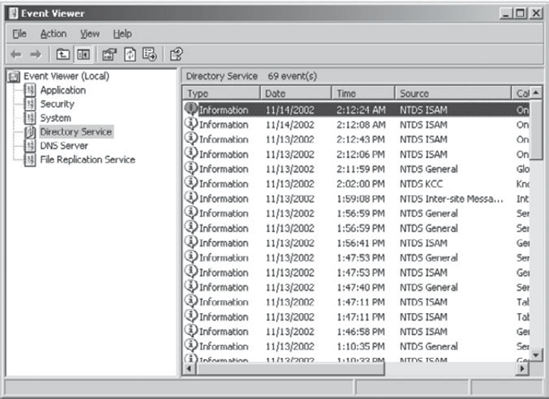
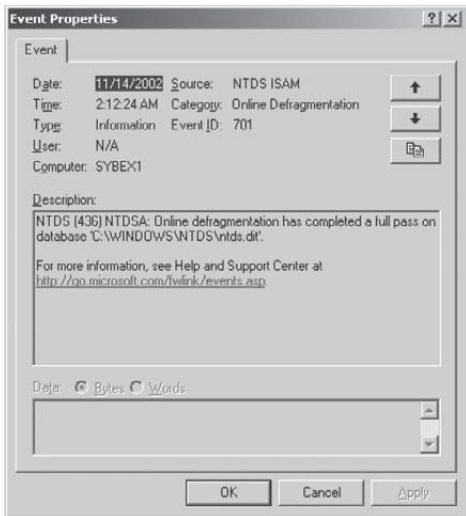
2.3. Examining the Event Logs
Whenever an error in the replication configuration
occurs, the computer writes events to the Directory Service and File
Replication Service event logs. By using the Event Viewer
administrative tool, you can quickly and easily view the details
associated with any problems in replication. For example, if one domain
controller is not able to communicate with another to transfer changes,
a log entry is created. Figure 1 shows an example of the types of events you will see in the Directory Service log, and Figure 2 shows a specific example of a configuration error.
2.4. Verifying That Information Is Synchronized
It's often easy to forget to perform manual checks
regarding the replication of Active Directory information. One of the
reasons for this is that Active Directory domain controllers have their
own read/write copies of the Active Directory database. Therefore, if
connectivity does not exist, you will not encounter failures while
creating new objects.
It is important to periodically verify that objects
have been synchronized between domain controllers. This process might
be as simple as logging on to a different domain controller and looking
at the objects within a specific OU. This manual check, although it
might be tedious, can prevent inconsistencies in the information stored
on domain controllers, which, over time, can become an administration
and security nightmare.
2.5. Verifying Authentication Scenarios
A common replication configuration issue occurs when
clients are forced to authenticate across slow network connections. The
primary symptom of the problem is that users complain about the amount
of time it takes them to log on to Active Directory (especially during
times of high volume of authentications, such as at the beginning of
the workday).
Usually, you can alleviate this problem by using
additional domain controllers or reconfiguring the site topology. A
good way to test this is to consider the possible scenarios for the
various clients that you support. Often, walking through a
configuration, such as, "A client in Domain1 is trying to authenticate
using a domain controller in Domain2, which is located across a slow
WAN connection," can be helpful in pinpointing potential problem areas.
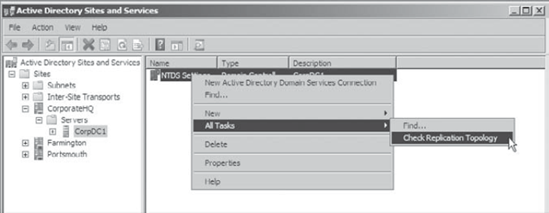
2.6. Verifying the Replication Topology
The Active Directory Sites And Services tool allows
you to verify that a replication topology is logically consistent. You
can quickly and easily perform this task by right-clicking the NTDS
Settings within a Server object and choosing All Tasks => Check Replication Topology (see Figure 3). If any errors are present, a dialog box alerts you to the problem.