Understanding the Lync Server Certificate
Viewing the certificate issued
for Lync Server will help one understand what certificates are and how
they get used. The easiest way to look at locally installed certificates
is with the Certificates MMC.
1. | From the Run line, type MMC. Press Enter.
|
2. | From the File menu, choose Add/Remove Snap-In.
|
3. | From the available snap-ins, add Certificates.
|
4. | When prompted, select Computer Account, and then click Finish.
|
5. | Choose Local Computer. Click Finish.
|
6. | Click OK.
|
7. | Expand Certificates (Local Computer).
|
8. | Expand Personal.
|
9. | Click Certificates.
|
10. | Double-click the certificate to be viewed.
|
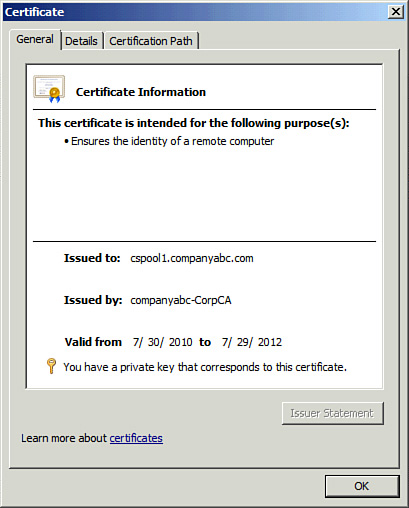
This view shows some
basic information about the certificate. At the top, the certificate
explains its intended purposes. Certificates are often used to ensure
the identity of a remote system and the Lync Server certificate is no
different. The certificate shows who it was issued to and who it was
issued by. This is how other systems can trust a system using this
certificate. They can check to see whether the name they asked for is
listed in the certificate and whether the certificate was issued by a
hierarchy that they trust.
The certificate also lists
its validity period. This is important to realize as the certificate
eventually expires. When it does, no other systems trust the
certificate. Figure 10
shows that the system holds the private key that corresponds to this
certificate. This gives one the potential to export the certificate and
the associated public and private keys so that the same certificate can
be used on other systems. This is common in situations where the
certificate is used on load-balanced systems.
Note
By listing the load-balanced
name in the certificate, clients connecting to any member of the
load-balanced group trust the certificate, connect properly, and
establish an encrypted session.
The Details tab on the certificate offers much more information, as follows:
Version— This is the type of template used to generate the certificate. Higher version numbers offer more customization of the template.
Serial number— This is a unique value used to identify a certificate.
Signature algorithm— This is the algorithm used to sign the certificate.
Signature hash algorithm— This is the algorithm used to create the signature hash.
Issuer— This is the canonical name of the CA that issued the certificate.
Valid from, Valid to— These values establish the lifespan of the certificate.
Subject—
This is a canonical representation of the name of the certificate,
including location information. It is important that the full name be
unique if you are replacing another certificate that is still valid.
Caution
Most providers revoke an existing
certificate if a new one is generated with the same subject name. This
can cause an outage if you do not plan for it. Typically, a certificate
provider allows you to register multiple OU values for naming
constraints to avoid a perfect match to the subject name.
Public Key— This is the value remote systems use to encrypt data destined for the holder of the private key.
Certificate Template Name— This is the name of the template the CA uses to issue the certificate.
Enhanced Key Usage—
This maps to a standard set of OIDs that define what a key can be used
for. In the case of the Lync Server certificate, the value is
1.3.6.1.5.5.7.3.1, which means server authentication.
Subject Key Identifier— Path validation software uses this value by helping to identify certificates that contain a particular public key.
Subject Alternative Name— This is the field that lists the names to which the certificate can correctly match.
Authority Key Identifier— Path validation software uses this value to help identify the next certificate up in a certificate chain.
CRL Distribution Points— This field tells a system where to check for Certificate Revocation Lists (CRLs).
Caution
At least one of these
paths needs to be reachable by a system that needs to trust the
certificate. If a CRL can’t be found, the client is not able to verify
that a certificate hasn’t been revoked and won’t trust it.
Authority Information Access— This value provides the network location for the issuing CA’s certificate.
Key Usage— This field defines what the keys can be used for.
Thumbprint algorithm— The algorithm used to generate the thumbprint of the certificate.
Thumbprint— A unique value identifying the certificate. Most applications that use certificates identify them by the thumbprint.
Friendly name—
This is a name given to the certificate by the requestor to more easily
identify a certificate. Administrators quickly realize that it’s much
easier to spot a certificate by its friendly name than it is to use its
thumbprint.
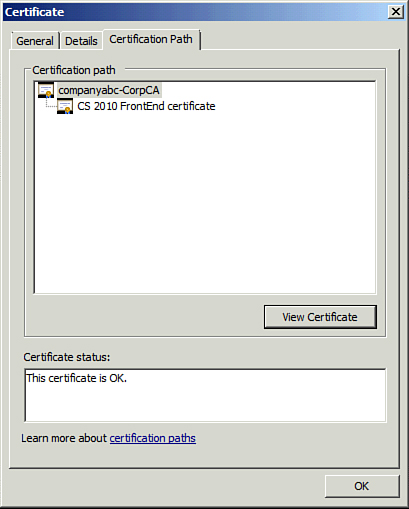
The last tab on the certificate is the Certification Path as shown in Figure 11.
This is the quick-and-easy way to ensure a certificate is valid. Not
only is there a simple statement of the certificate’s status, but if
that status is invalid, you can quickly look at the chain to see where
the problem is. You can even look at upstream certificates from the
chain and view the same level of details on those. This makes it easier
to troubleshoot issues such as expired intermediate CAs or inaccessible
CRLs.