The Lync Edge Server in Lync Server 2013 is
made up of four separate services: Access Edge Server, Web Conferencing
Edge Server, A/V Edge Server, and the XMPP Gateway. Each service
provides slightly different functionality, and depending on the
organization’s requirements, it might not be necessary to use all
services. With Lync Server 2013, all services are deployed together on
every edge server. Lync Server 2013 introduces the capability to deploy
the XMPP Gateway Service directly on the Edge Server as opposed to a
separate server role in previous product versions.
Unlike many of the internal roles, the Edge
Server does not require database or file shares because it does not
store data other than the Local Configuration Store replica from the
Central Management Store. Because the Edge Server is designed to be
deployed in a perimeter or DMZ network, it runs a
limited set of services to make it as secure as possible. Edge Servers
are also typically not joined to the internal Active Directory domain,
but can be if necessary. The different Edge Server roles provide unique
features, as shown in Figure 1.
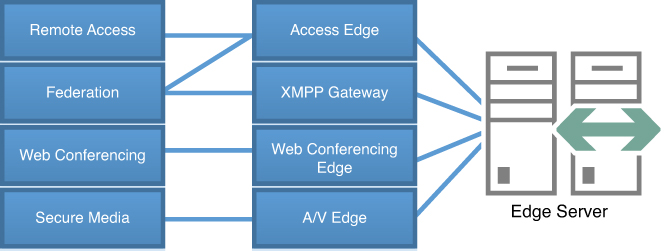
Figure 1. Edge Server Services.
In addition to the Lync Edge Server
Services, a reverse proxy solution is required to publish web services,
including Mobility.
Access Edge Service
The Access Edge Service acts as a secure
proxy for all remote Lync signaling traffic. Without the Access Edge
Service deployed, all other edge roles would not be able to function.
The Access Edge Service provides Remote Access, Federation, and Public
Provider connectivity in Lync Server 2013.
Remote Access
One function of the Access Edge Server is to
provide remote access capabilities to a Lync Server infrastructure.
After an internal deployment of pools is complete, an Access Edge
Server can be provisioned to enable users to sign in and use their
endpoints across the Internet.
As long as the appropriate SRV records exist
in DNS or the client is manually configured correctly, a user can
travel in and out of the office without ever making a change to an
endpoint. This enables users to have full access to their internal
features regardless of location.
Note
Because 443 is a standard, well-known port, it is used for Remote Access by the Access Edge Service.
Federation
The Access Edge Server also provides the
capability to federate with other organizations that have deployed Lync
Server, meaning the two organizations can communicate with each other
as if it were a single deployment.
Users have different feature sets available
when using federation, depending on the version of Lync Server a
partner has deployed. The feature set is the lowest common denominator
between the two organizations. For example, if a partner runs Live
Communications Server 2005, only IM and presence will be available.
However, if a partner organization is running Office Communications
Server 2007 R2, A/V and Desktop Sharing features can be used through
federation. The largest feature set is available if both organizations
are running Lync Server 2013.
Access Edge Servers use certificates and
Mutual TLS (MTLS) to secure the SIP signaling used across the Internet
with each other. This ensures that instant messaging and presence
traffic is completely secure and is never transmitted in plain text.
Note
Organizations most often procure a
certificate from a public certificate authority so that partners trust
their server by default. However, it is possible to exchange
certificate chains with a partner to support additional certificate
authorities.