5. Editing the Registry
After researching a software problem, you might find that the solution involves a "registry hack," also known as editing the registry.
This is serious business with little margin for error. Never attempt to
fix a problem by guessing at a registry hack. When you do get specific
instructions on making a registry change, make sure you make exactly
the change indicated in the message. Even the slightest typographical
error can cause a world of problems. If you're not a technical person
and don't want to risk creating a really big mess you can't rectify,
consider hiring a professional to resolve the problem.
Before you launch into registry hacking, you need to
understand what you're doing. First, be aware that the registry is a
database where Windows and other programs store data that they need to
operate properly on your computer. The average computer user typically
doesn't need to know that the registry exists. In fact, I'm sure most do
not. There is absolutely nothing that's "user friendly" about the
registry. In fact, it's probably just about as "user hostile" as you can
get. Microsoft provides the Registry Editor described in this chapter
because programmers and other IT professionals occasionally need to view
or modify registry entries.
|
The registry is not a safe place to mess around. Pay attention to all cautions in this chapter!
|
|
5.1. How Registry Data is Organized
The Windows registry comprises several hives, each of which holds specific types of data. Within each hive, the registry uses keys and subkeys to organize data. Just as a folder can contain subfolders, a key can contain subkeys.
The registry doesn't store files or documents, however. Rather, it stores values.
Some of these values make sense to the average user, but some do not.
For example, if you have Microsoft Office installed, there is a value in
the registry that stores the path to the Office installation folder,
and the value is typically C:\Program Files\Microsoft Office\Office 12\. That's easy to understand. However, you'll also find a lot of values in the registry that look something like {89820200-ECBD-11cf-8B85-00AA005B4383}!8,0,7100,0,
and it's highly unlikely that this value will mean anything to you. But
whether or not the value of a given registry entry makes sense to you,
they make sense to the application that is using the value, and that
value must be entered exactly as required.
5.1.1. Hives, keys, and subkeys
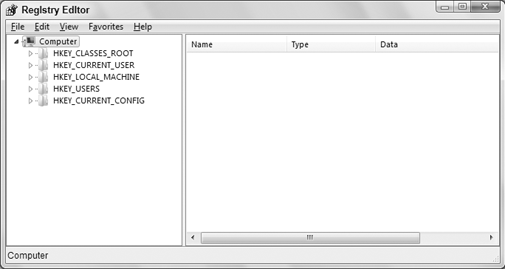
I get into the specifics of editing the registry in a moment. But first, Figure 1 shows an example of the Registry Editor as it might look when you first open it. The names listed down the left column are hives.
As defined by Microsoft, a hive is a logical group of keys, subkeys,
and values in the registry that has a set of supporting files containing
backups of its data. So, each hive contains keys, subkeys, and data.
Each hive stores a particular type of information, as summarized in Table 1. Note that most keys have a standard abbreviation, such as HKCU for HKEY_CURRENT_USER.
|
To open Registry Editor, click Start, type regedit, and press Enter.
|
|
When you click the white triangle next to a hive, it
expands to display its key. Most of the keys have subkeys, and those
subkeys might also have subkeys of their own. In that case, the subkey
itself will have a white triangle too, which you can click to see
another level of subkeys. For example, in Figure 2, I've expanded the HKEY_CLASSES_ROOT
key to reveal its subkeys. Each subkey represents a particular file
type in that case. I've also expanded a few subkeys in that example.
You'll often see a reference to a specific subkey
expressed as a path, in much the way that you might see a file's
location and name expressed as a path. For example, the path to a file
might be expressed as C:\Users\jboyce\Pictures\Summit01.jpg. The path tells Windows exactly where to find the file Summit01.jpg in my Pictures folder.
A registry path is the same idea, and even uses
backslashes to separate the key and subkey names. For example, the
highlighted subkey in Figure 2 is at Computer\HKEY_CLASSES_ROOT\.3g2\OpenWithProgIds.
Table 1. Standard Root Keys
| Name | Abbreviation | Description |
|---|
| HKEY_CLASSES_ROOT | HKCR | Stores
information about document types and extensions, registered programs
that can open each file type, the default program for each file type,
and options that appear when you right-click an icon. |
| HKEY_CURRENT_USER | HKCU | Stores
information about the person who is currently using the computer, based
on which user account that person is logged in to, and settings that
particular user chose within his or her account. |
| HKEY_LOCAL_MACHINE | HKLM | Stores
information about all the hardware that's available to the computer,
including devices that might not be plugged in at the moment. |
| HKEY_USERS | HKU | Stores information about all users, based on user accounts you've defined via Control Panel. |
| HKEY_CURRENT_CONFIG | <none> | Similar
to HKEY_LOCAL_MACHINE, this key stores information about hardware
available to the computer. However, this key limits its storage to
hardware that's connected and functioning currently. |
Sometimes you'll see instructions telling you the path to a key or subkey, like HKEY_CURRENT_ USER\Control Panel\Appearance\Schemes. You have to manually expand each folder down the path to get to the subkey. Figure 3
shows the result of following that sample path. The values in the Data
column for that key are mostly binary numbers; a good example of just
how user unfriendly the registry can be!
5.1.2. Key values
The data stored in a subkey is called a value.
The value is a specific piece of information that can be stored as a
string (text) or a number. However, the terms "string" and "number"
don't tell the whole story, because those types can be further broken
down into the specific data types listed in Table 2.
In the vast majority of situations, you'll be working
with strings, DWORDs, or QWORDs when you create or modify registry
entries. Entering a string in the registry is just like entering a
string in a text box. When you enter DWORD and QWORD values, however,
you enter those either as a decimal or a hexadecimal value. I won't go
into detail about the differences here, and if you want a clearer
understanding of hexadecimal numbering, a quick search on the Web will
turn up lots of explanations and examples. Just keep in mind that when
you edit a DWORD or QWORD value, you need to choose the option that
matches the value you are entering. Figure 4 shows an example of a value entered as a decimal number.
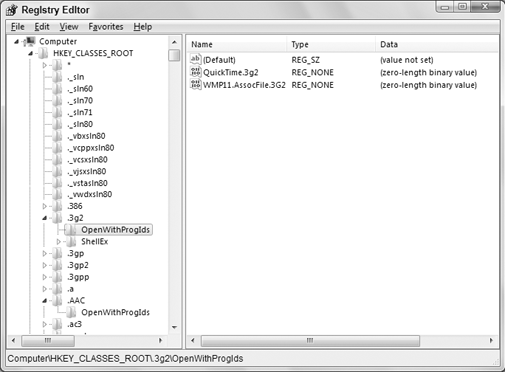
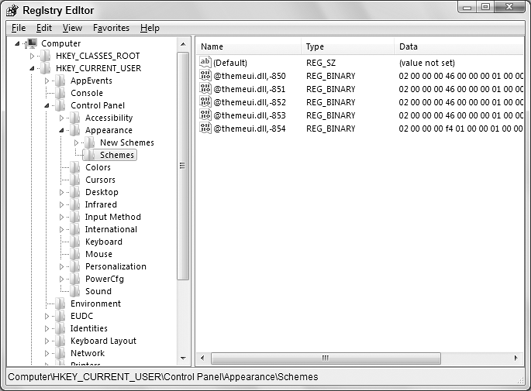
Table 2. Registry Value Data Types
| Name | Data type | Description |
|---|
| Binary Value | REG_BINARY | Raw binary data used mostly by hardware components. Often displayed in hexadecimal format. |
| DWORD Value | REG_DWORD | An integer often used to store parameters for device drivers and services. Subtypes include related types such as DWORD_LITTLE_ENDIAN and REG_DWORD_BIG_ENDIAN with the least significant bit at the lowest/highest address, respectively. |
| Expandable String Value | REG_EXPAND_SZ | A variable-length string often used to store data for application programs and services. |
| Multi-String Value | REG_MULTI_SZ | A string that actually consists of multiple substrings separated by spaces, commas, or other special characters. |
| String Value | REG_SZ | A simple fixed-length text string. |
| Binary Value | REG_RESOURCE_LIST | A series of nested arrays (lists) often used by hardware and device drivers. Usually displayed in hexadecimal. |
| Binary Value | REG_RESOURCE_REQUIREMENTS_LIST | A series of nested arrays (lists) containing a device driver's hardware resources, displayed in hexadecimal. |
| Binary Value | REG_FULL_RESOURCE_DESCRIPTOR | A series of nested lists of actual hardware device capabilities, usually displayed in hexadecimal. |
| None | REG_NONE | Data with no particular type that's displayed as a Binary Value in hexadecimal. |
| Link | REG_LINK | A string naming a symbolic link. |
| QWORD Value | REG_QWORD | A 64-bit number displayed as a binary value. |
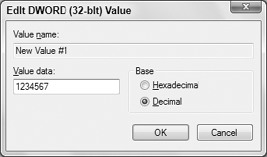
If the troubleshooting steps that you are using
direct you to enter a decimal value, click the Decimal option and then
type the value specified. If you need to enter a hexadecimal value,
click the Hexadecimal option before you type the value.
5.2. Backing up the registry
Every time you start your computer, Windows
automatically creates the registry based on the hardware and software
available to it. Then, it makes a backup copy of that registry. When you
plan to manually change the registry, you should also make a backup
copy of the registry just before you make your change. Because when it
comes to editing the registry, there is no margin for error and even a
tiny typographical error can have far-reaching, unpleasant consequences.
You need administrative privileges to edit the
registry. The program you use is named regedit. You can start it using
either of these methods:
Tap  , type regedit, and click regedit.exe on the Start menu.
, type regedit, and click regedit.exe on the Start menu.
Click the Start button, choose Run, type regedit, and press Enter.
NOTE
If you don't have a Run option on your Start
menu, you can add it. Right-click the Start button and choose
Properties. Then click Customize, check Run Command in the list of
programs, and click OK in each open dialog box.
The Registry Editor opens. You always want to make a backup of the registry before you change anything. It's easy to do:
Choose File => Export from the menu bar in the Registry Editor.
Choose a folder and enter a filename of your own choosing.
To export the entire registry, choose All under the Export Range heading.
That's it. In the event of a disaster, you can choose File => Import from the Registry Editor's menu bar to restore all the entries you copied in the preceding steps.
5.3. Making the registry change
You can change any value in the registry. First you
need to get to the appropriate subkey. For example, let's say that
you've found the solution to some problem via Microsoft's Web site. Part
of that solution involves changing a value in the following subkey:
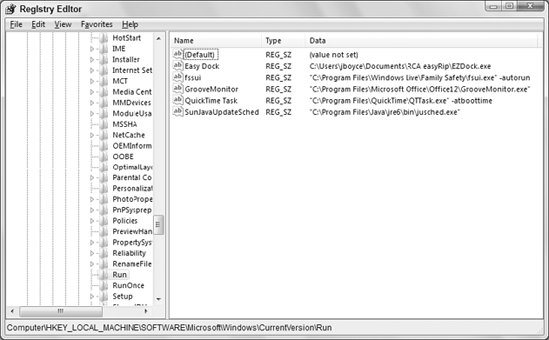
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
The first step is to get to the subkey by expanding
the HKEY_LOCAL_MACHINE, SOFTWARE, Microsoft, Windows, and CurrentVersion
node. Then click Run. The pane to the right shows values in the subkey.
The status bar shows the complete path name as in Figure 5.
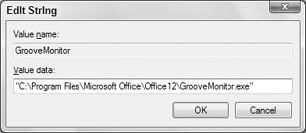
To change a subkey's value, double-click that value. A
dialog box will open allowing you to make a change. The appearance of
the dialog box depends on the type of value you're editing. Figure 6 shows a general example.
|
Make sure you get to the correct key, and make exactly the change your instructions tell you to. Even the slightest mistake here could cause big problems down the road.
|
|
The Value Data box contains the value you can edit.
Make your change there and click OK. Then close the Registry Editor. You
have finished making your registry change.
Whether or not you see any change on the screen
depends on the value you changed. Many registry hacks will have no
effect until you close the Registry Editor, close all open program
windows, and restart the computer.
If it turns out you created more problems than you
solved, you can restore your registry from the backup you make. Open the
Registry Editor and choose File => Import to import the backed-up file. Otherwise, if all seems well, you can delete the backed-up registry file.