1. Understanding netsh
The Net Shell (netsh)
command is a rich command-line scripting tool that enables you to
display and modify the network configuration of local and remote
computers. You can run netsh commands from the netsh prompt, from the command prompt, or from a batch file.
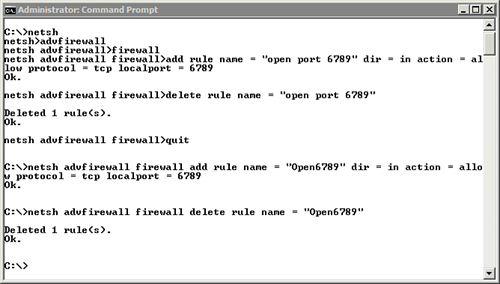
For example, the following table shows different
ways you can create a rule to open port 6789 on the firewall, and how
to delete the rule.
| Methods of Using netsh | Comments |
|---|
C:\>netsh
netsh>advfirewall
netsh advfirewall>firewall
netsh advfirewall firewall>add rule name
= "open port 6789" dir = in action =
allow protocol = tcp localport = 6789
Ok.
netsh advfirewall firewall>delete rule
name = "open port 6789"
Deleted 1 rule(s).
Ok.
| You can enter the netsh shell and enter the commands. The benefit of doing it this way is that after you enter context, you can type help or ? to get a list of possible commands and contexts.
First, type netsh to access the shell. Next, enter advfirewall to enter the advfirewall context. You can then create the rule with the add rule statement.
You can delete rules using the delete rule statement and the name of the rule. |
C:\>netsh advfirewall firewall add rule
name = "Open6789" dir = in action = allow
protocol = tcp localport = 6789
Ok.
C:\>netsh advfirewall firewall delete
rule name = "Open6789"
Deleted 1 rule(s).
Ok.
| You
can enter the entire line from the command line (or put it into a batch
file). You are entering the same data but instead of entering it one
command at a time to reach the netsh advfirewall firewall context, you enter all the data at the same time.
Similarly, you can delete the rule with a single-line entry. |
Figure 1 shows how these commands look when entered at the command prompt. When using the netsh command, you can see how the context changes as commands are entered.
2. Understanding netsh Contexts
The netsh command
has multiple command contexts. Each time you enter a context, you have
a different set of commands you can use. For example, if you are in the
netsh interface context, the following commands are available to you.
| Context | Description |
|---|
| netsh interface>? or help | Displays a list of commands. |
| netsh interface>6to4 | Changes to the ‘netsh interface 6to4’ context. |
| netsh interface>ipv4 | Changes to the ‘netsh interface ipv4’ context. |
| netsh interface>ipv6 | Changes to the ‘netsh interface ipv6’ context. |
| netsh interface>tcp | Changes to the ‘netsh interface tcp’ context. |
| netsh interface>teredo | Changes to the ‘netsh interface teredo’ context. |
| netsh interface>httpstunnel | Changes to the ‘netsh interface httpstunnel’ context. |
| netsh interface>portproxy | Changes to the ‘netsh interface portproxy’ context. |
| netsh interface>set | Sets configuration information. |
| netsh interface>show | Displays information. |
| netsh interface>dump | Displays a configuration script. |
If you instead enter the advfirewall
command, you have access to a different set of commands associated with
the advfirewall context. You can view the available commands by
entering help or ? at any context command.
Some of the contexts you might use with Windows Server 2008 are listed in the following table.
| Context | Description |
|---|
Interface (IPv4 and IPv6)netsh>interface ipv4
netsh interface ipv4>
netsh>interface ipv6
netsh interface ipv6>
| You
can display and configure IPv4 and IPv6 information for network
interfaces from the ipv4 and ipv6 shell contexts.
|
Windows firewall with advanced security
netsh>advfirewall
netsh advfirewall>show
allprofiles
| You can use netsh advfirewall
commands to work with the Windows Firewall with Advanced Security.
These commands help with the creation, administration, and monitoring
of Windows Firewall and IPsec and can be useful when configuring
Windows Firewall with Advanced Security settings to a large number of
computers. You can embed the commands in a batch file to automate the
configuration of the systems. |
| Windows firewall
netsh>firewall | This command displays and configures firewall settings.
Note
This context has been deprecated in favor of the advfirewall firewall
context. It modifies only firewall rules for the domain and private
profiles.
|
Wired local area network (lan)netsh>lan
netsh lan>show profiles
| You can use the netsh local area network (lan)
context to configure and manage 802.3 wired Ethernet connectivity. If
you have computers that connect IEEE 802.1x servers for authentication,
you can configure the security settings here. You can also display
information about network adapter drivers, network profiles, and more.
As an example, the show profiles command shows any existing wired profiles on the system.
Note
This context needs the Wired AutoConfig Service (dot3svc) to be running.
|
Wireless Local Area Network (wlan)netsh>wlan
netsh wlan>show profiles
netsh wlan>show alltt
| You can use the netsh wireless local area network (wlan) context to configure and manage 802.11 wireless connectivity and security settings. Additionally, the netsh wlan commands can display information about 802.11 wireless adapter drivers, wireless network profiles, and more.
As an example, the show profiles command shows a list of any existing profiles, wireless adapters, and networks.
Note
This context needs the Wireless AutoConfig Service (wlansvc) to be running.
|
Windows Hypertext Transfer Protocol (winhttp)netsh>winhttp
netsh winhttp>show proxy
| You can use the winhttp
context to configure proxy and tracing settings for Windows HTTP. For
example, if you want to view current proxy settings, you can use show proxy.
Tip
A result of “Direct access (no proxy server)” indicates a proxy server hasn’t been configured.
|
No matter which context you enter, you have several
core commands available to you. Some of these commands are shown in the
following table.
| Command | Description |
|---|
| Moves the context up one level. |
alias
netsh>alias nic "local
area connection"
netsh>alias
nic local area connection
| Creates an alias that can be used within the netsh session. An alias is one string of characters that can take the place of another string of characters.
The example shows how to create an alias named nic to represent “local area connection”.
When entered by itself, it lists all known aliases just like show alias. |
unalias alias-name
netsh>unalias nic
| You can delete an existing alias with the unaliasnetsh.
command. The alias is also deleted if you exit Tip
The existing alias name must be entered with the exact case (uppercase and lowercase). In other words, unalias NIC does not work in this example.
|
bye, exit, or quit
netsh>bye
C:\>
| Exits netsh. |
dump
netsh>dump
netsh>dump > c:\data\
config.txt
| Displays all of the current netsh
context configuration data. You can execute this from the command
prompt to redirect the output to a text file. The text file can then be
used to reconfigure the system with the exec command. |
exec scriptfile
netsh>exec c:\data\
config.txt
| Executes
a script file. This can be used to reconfigure a computer using the
settings in the script file. You can create the script file with the dump command. |
| Displays help. Help information includes commands that can be listed in any context and the current context. |
set file [open | append
| close] file
netsh>set file open
c:\data\netsh.txt
netsh>set file append
c:\data\netsh.txt
netsh>set file close
| Copies all data from the netsh session to a file. You can use the set file command to capture all the activity in your session. The open command creates a new file. appendclose command stops sending the data to the file. Note that you don’t enter the name of the file in the close command.
|
set machine
set machine [name
=] computer [user =
DomainName\UserName]
[pwd = ][Password | *]
netsh>set machine name
= dc1 user = pearson\
administrator pwd =
P@ssw0rd
[dc1] netsh>
| You can use the set machine
command to connect to a remote system and perform the tasks on it. The
default is the local system. For example, if you want to use netsh
to administer a server named DC1 in the Pearson domain, you can use the
Pearson\Administrator account with the administrator’s password
(P@ssw0rd in the example). The prompt changes to include the remote
computer’s name. |
set mode [ online |
offline ]
netsh>set mode online
netsh>set mode offline
| You can set the mode to online or offline. In online mode, netsh commands are run immediately after you type them and press Enter. In offline mode, netsh commands are saved and can be run with the commit command or aborted with the abort command. |
| The abort command discards any changes made in offline mode. It does not have any effect if executed in online mode. |
| The commit command commits any changes made in the offline mode. It does not have any effect in online mode. |
show
netsh>show alias
netsh>show helper
netsh>show mode
| You can view alias, helper, and mode information with the show
command. Aliases aren’t created by default but many default helper DLLs
are available by default to provide help in different contexts. |