3. Understand Local User Rights
You might be thinking that
granting users permissions to your server is as easy as adding the user
to the right group. Well, in part, you are correct; however, you need to
understand what truly grants users the ability to do work on the
Windows Server 2008 R2 server. Those abilities are called rights
on a server, and in turn the local rights are assigned to the user or
group. For example, when you add a user to the Backup Operators group,
that group is granted a few built-in rights. A couple of those rights
are Backup Files and Directories and Restore Files and Directories, for
example.
3.1. View the Local User Rights
To see a list of the local
rights on the server, you need to open the Local Security Policy MMC on
the system. The local security policy will allow you to look at the
local user rights and will show account policies, Windows Firewall, and
other important security settings on your server. To view the local
security policy, you need to be an administrator for the server.
In Search Programs And Files, type Local Security Policy.
Click the Local Security Policy link, and you will see a screen similar to Figure 12.
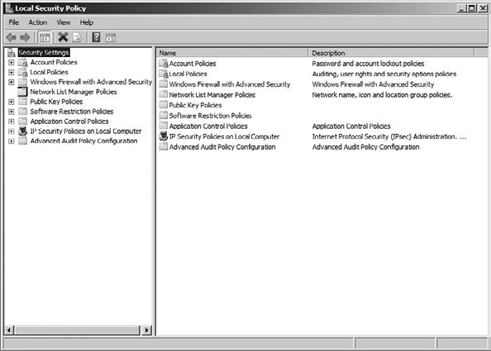
In the Local Security Policy MMC, click the + sign next to Local Policies to expand the console tree.
Click User Rights Assignment to view the currently assigned rights on the system, as shown in Figure 13.
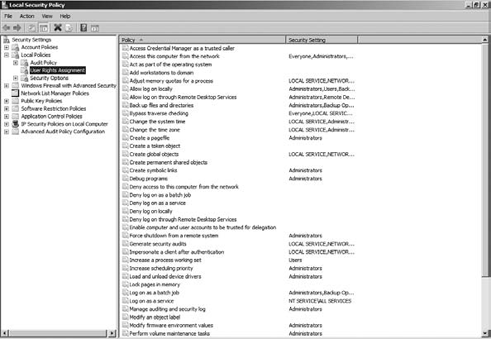
To
see the currently assigned rights for any of the local users, simply
double-click the appropriate object in the right pane. For example, if
you double-click Backup Files And Directories, you will see that by
default two local groups, Administrators and Backup Operators, have been
granted the right.
|
When you first look at the local
security policy, you will see several of the user rights already
assigned to various local built-in groups and special identities. If
you're not sure what the user right is designed to accomplish, you
should avoid making any changes to the default assignments on your
server. In general, it is OK to make additions to the assigned local
rights but not deletions to the default policies. Making the wrong
deletion could prevent your server from functioning properly and could
cause you to have to reinstall the server.
Even though you can make
changes to the user rights, try to avoid this. If you need to grant
users rights to perform actions on your server, check to see whether any
of the built-in groups can accommodate your needs.
|
|
If
you want to add any of the users or local groups you have created on
the server to a user right, simply double-click the user right to view
the properties of it.
Click
Add to go through the familiar wizard for adding users to a group. The
only difference is that during the wizard, you will see both users and
groups.
3.2. Rights or Permissions
A common area that can cause
confusion is the distinction between rights and permissions. Even though
they are similar, in a Windows Server 2008 R2 environment they are used
for different purposes. Understanding the difference will help you
maintain your systems more efficiently. This concept of rights and
permissions will follow you through all the work you do regarding secure
access to your Windows Server 2008 R2 servers, even when you work with
the Active Directory domain infrastructures.
Rights
One way you can think of rights, as you have seen from the previous
examples, is that they grant user abilities on the server. These
abilities are special and usually give your user extra access to a
server.
Permissions
These grant the user the ability to access Windows Server 2008 R2
resources, such as printers, files, and shares. Permissions will
determine your level of access to an object such as a file or whether
you can change the object or just read it, and they will be determined
by the permissions assigned to the object.
4. Work with Local Account Policies
You will need to manage the
local account policies on your servers. The local account policies on
your server are designed to protect the integrity of your users and the
passwords they use. Whether you are using a stand-alone sever or an
Active Directory domain for logon access, these local policies have the
same impact in both environments. They also help lock out the accounts
if there are too many invalid attempts to access a given user account.
Before you take a look at how to manage the account policies of your
server, you need to understand the importance of passwords and how the
account policies are there to protect you.
4.1. A Word on Passwords
As you most likely know,
there is nothing more important to the security of your environment than
the passwords used by you and your users. Keeping these passwords
protected is critical to any environment. You also want to always
enforce password complexity and length to make sure your users passwords
are hard to guess and can't be hacked.
You may have heard this phrase before:
"Passwords are like
bubble gum. They are strongest when fresh, should only be used by
individuals and not a group, and if left laying around can create a
sticky mess."
This is a fantastic way to
think of passwords. What it means in a technical sense for you as an
administrator is this: make sure you expire passwords on a regular basis
to force users to regularly change passwords. This also goes hand in
hand with password history and making sure that you keep track of users'
former passwords so they cannot revert to old passwords. If you do not
keep track of password history, what your users may do when their
passwords expire is change their password to a new password and then
change the password right back to their former password. Expiring
passwords and keeping track of passwords will help keep your passwords
fresh and secure.
If you have shared
workstations in your network and have multiple users using a
workstation, it is well worth your time to create individual accounts
for each of the users. Not only will this protect the security of your
environment, but it will also provide you with some flexibility when it
comes to administering the users on the workstation.
Lastly, you may have seen or
heard about users using sticky notes with the passwords written on them
stuck to the monitor of their workstation. As you can imagine, this
potentially opens your environment up to having users' passwords stolen.
It is worth your time to occasionally patrol the hallways of your
business to make sure this is not happening.
While on patrol, you may
also notice unlocked desktops, which is another open avenue for you to
be attacked. One way you can prevent this is with group policies and
setting screensaver policies to lock the desktop after a predetermined
amount of idle time. Another, more nefarious way is that you can provide your users with a
teachable moment when you find an unlocked desktop—send the user an
email from themselves. Now, this method is more than likely prohibited
by your employer, and I do not recommend this. It's just something to
get you thinking about the potential danger of unlocked desktops in your
organization. Now, you do not need to send the message to anyone other
than the user who left their desktop unlocked. It would look something
like this:
From: Unlocked User
To: Unlocked User
Subject: Lock Your Desktop
Message: Just think this message could have gone to your boss. So please, lock your desktop in the future.
Sincerely,
Your friendly neighborhood administrator
4.2. A Look at Account Policies
Your local account
policies are also located in the local security policy for your server.
The account polices are broken into two areas. One is for the password
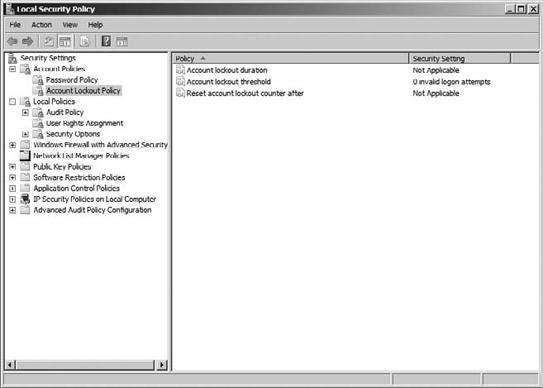
policy, as shown in Figure 14, and the other is your account lockout policy, as shown in Figure 15.
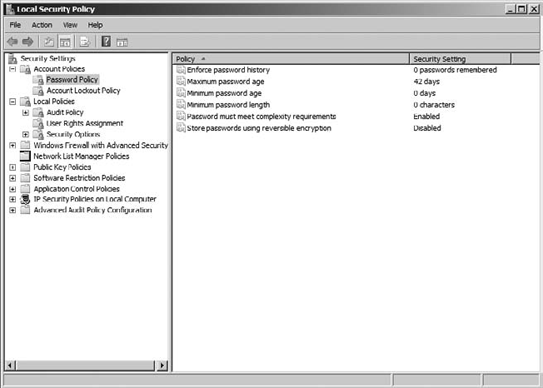
Working with your password policy allows you to control settings regarding password settings. Table 3
describes those settings and the default values. To change any of the
settings on your server, you can use Group Policy or modify the settings
by double-clicking them when you're viewing them in the Local Security
Policy MMC.
Table 3. Password Policies
| Policy | Description | Default Setting |
|---|
| Enforce Password History | This
determines the amount of unique new passwords associated with the users
on the system and can be set to 0–24. This allows your users to keep
their passwords fresh. | 0 for stand-alone servers 24 for domain controller |
| Maximum Password Age | Determines
how many days a password can remain unchanged on a system and can be
1–999. If the setting is set to 0, then the passwords will never expire. | 42 days until passwords expire |
| Minimum Password Age | Determines
how many days a password has to be used before the user can change it
and can be set to 0–998. You should change this value on your
stand-alone servers. If the value is set to 0, your user can change the
password immediately after a change. | 0 days for stand-alone server 1 day for domain controllers |
| Minimum Password Length | Determines the minimum amount of characters a password has to be on the system. | 0 for stand-alone servers 7 for domain controller |
| Password Must Meet Complexity Requirements | This
determines whether the password has to meet the complexity
requirements. If the minimum password length is set to 0, the complexity
requirement of six characters will supersede the minimum password
length setting; otherwise, the minimum password length setting will win. | Enabled |
| Store Passwords Using Reversible Encryption | This
determines whether the passwords will be stored in a reversible
encryption algorithm. This is akin to storing your passwords in plain
text and should never be enabled unless you have an application or
system requirement for this to be enabled. | Disabled |
Working with account
lockout policies allows basic control over failed logon attempts to your
server. When an account is locked out, it effectively becomes disabled
and cannot be used until the account is unlocked by an administrator or a
preset amount of time has passed. All of those settings can be changed
with Group Policy, or you can modify the settings by double-clicking
them when you're viewing them in the Local Security Policy MMC. Table 4 describes the Account Lockout Policy settings and the default values.
Table 4. Account Lockout Policy
| Policy | Description | Default Setting |
|---|
| Account Lockout Duration | Determines
the amount of time the account will remain locked out until unlocking
automatically. It can be from 0 to 99,999 minutes. If the policy is set
to 0, then the account will remain locked out until an administrator
explicitly unlocks the account. The setting has no pertinence until the
Account Lockout Threshold policy is set. | None |
| Account Lockout Threshold | Determines
the number of failed logon attempts before the account is locked out
and can be set to 0–999 attempts. If it is set to 0, the account will
never be locked out. Failed attempts include main logon at the
Ctrl+Alt+Del, locked desktop logon, and password-protected screensavers. | 0 invalid logon attempts |
| Reset Account Lockout Counter After | Each
failed attempt to log on counts against the threshold counter. However,
you can set a period of time when the counter is reset when a set
amount of time passes. The setting can be a period of time from 0–99,999
minutes. The setting has no pertinence until the Account Lockout
Threshold policy is set. If the threshold policy is set, this setting
needs to be less than or equal to the Account Lockout Duration setting. | None |