Administrators use Group Policy to
administer and manage users and computers within a domain. There are
literally thousands of Group Policy settings. The goal isn’t to know
them all but instead to understand a few key Group Policy settings, how
they’re created, and how they apply. The following sections cover a few
Group Policy settings.
Enabling Auditing Through Group Policy
You can configure audit policy settings to ensure that certain activities in your organization are tracked.
Figure 1 shows the Audit Policy in the Default Domain Policy open, and the following table explains these audit policy settings.
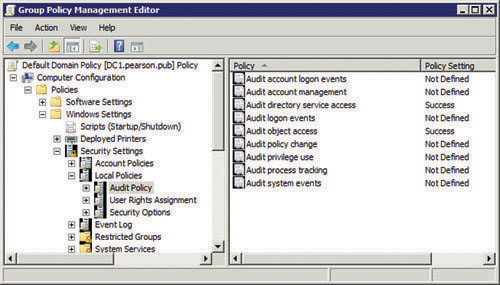
| Audit Policy Settings | Comments |
|---|
| Audit account logon events. | Account
logon events are generated when a domain user account is authenticated
on a domain controller and the event is logged in the domain
controller’s security log. Account logoff events are not generated. |
| Audit account management. | Account
management events include when a user account or group is created,
changed, or deleted; a user account is renamed, disabled, or enabled;
or a password is set or changed. |
| Audit directory service access. | Enables
security logging for any Active Directory object (such as users,
groups, and OUs) access in Active Directory that have security logging
enabled. This setting is enabled by default for domain controllers.
Note
This setting only applies to domain controllers. It has no meaning for workstations and servers.
|
| Audit logon events. | Logon
events are generated when a local user is authenticated on a local
computer. The event is logged in the local security log. |
| Audit object access. | Enables
security logging for any object (such as files, folders, and printers)
access in the domain that has security logging enabled. It is not
enabled by default.
Tip Enabling
object access auditing is a two-step process. You must first enable the
auditing through Group Policy. Then you must enable auditing for the
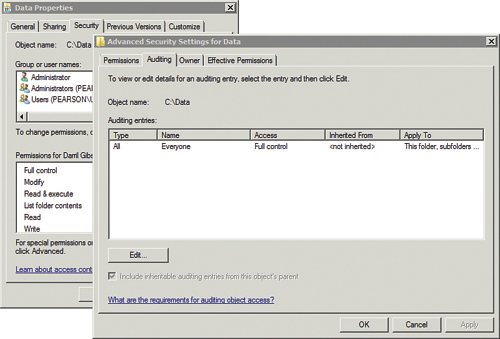
individual object. For example, Figure 2 shows the Auditing tab of the Advanced Security Settings of a folder named Data.
|
| Audit policy change. | Generates security log entries in response to changes in user rights assignment policies, audit policies, or trust policies. |
| Audit privilege user. | The
use of elevated privileges generates a log in the security log. For
example, if a user takes ownership of a file, it generates a log entry. |
| Audit process tracking. | Process
tracking logs entries for events such as program activation, process
exit, handle duplication, and indirect object access. |
| Audit system events. | System
events include when a user restarts or shuts down the computer or when
an event occurs that affects either the system security or the security
log. |
Note
Both success and failure events can be logged for
each of these Audit Policy settings. A success event occurs when the
user succeeds in the action. A failure event occurs when the user
attempts the action but is unsuccessful, such as when the user doesn’t
have permissions or rights to take the action.