3. Set Up the Windows Firewall
A
firewall is a layer of protection that permits or denies network
communication based on a predefined set of rules. These rules restrict
communication so that only certain applications are permitted to use
your network connection. This effectively closes some backdoors to your
computer that otherwise might be exploited by hackers, certain types of
viruses, and other malicious applications.
For
the most part, you can leave Windows Firewall alone and never touch it.
Unlike the early firewall debacle that came with Windows XP, the one in
Vista is not booby-trapped to prevent file sharing or the Internet time
feature. In fact, it's pretty unobtrusive, bothering you only if it
detects a program it hasn't seen before.
The
biggest problem with Windows Firewall is that it doesn't protect your
PC nearly as much as people think it does, nor does it offer the same
kind of protection as a router or hardware-based firewall. While it's
better than having no firewall, Windows Firewall can provide a false
sense of security. |
|
One
of the main reasons a router is so effective is that it provides a
layer of abstraction between your network and the outside world.
Consider a single packet of incoming data: if your PC is connected
directly to the source of the threat (no router), all that packet has to
do is sneak in through one of Windows Firewall's many exceptions
(explained later), and it's home free.
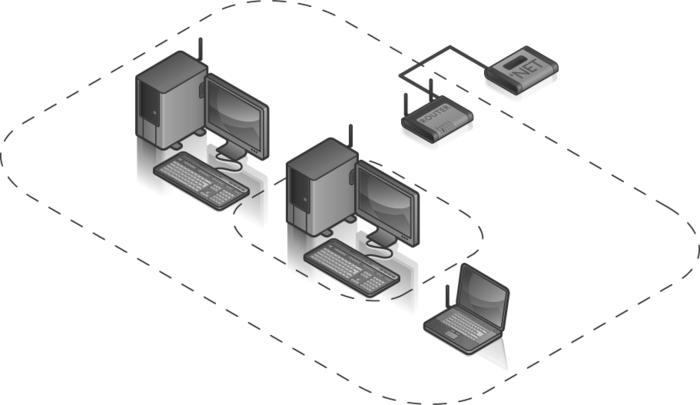
To
illustrate the another difference between the security offered by the
Windows Firewall versus that afforded by a router, consider Figure 2.
The larger dotted rectangle shows what's protected by your router's
firewall, and the smaller rectangle shows what's protected by Windows.
In addition to the larger scope of the router's protection, it's also
much less likely to be compromised than a software-based solution like
the Windows Firewall.
Now,
assuming you've bought the previous argument, you might think that more
firewall is better—that using Windows Firewall along with a router will
protect your system better than a router alone. The problem with this
approach is that, again referring to Figure 7-29,
Windows Firewall somewhat isolates your PC from the other computers in
your workgroup. This can be good, in that viruses and other spyware on
other PCs on your network will have a harder time infecting your PC (a
particularly useful feature when you're surfing on a public network), or
it can be bad, in that the Windows Firewall can break features you use
every day.
If
you're on the road, and not behind the protective veil of your router's
firewall, you should always use Windows Firewall or some other
software-based firewall to help protect your PC from other PCs lurking
on any public networks you might use. |
|
By
default, Windows Firewall is enabled for all network connections on
your PC; you can turn it off or on in the main Windows Firewall page in
Control Panel. To turn it on or off for a specific network connection,
open the Windows Firewall Settings window, choose the Advanced tab, and remove the checkmarks next to the connections you don't want to protect.
3.1. Poke holes in the firewall
On
a day-to-day basis, the Windows Firewall creates new rules on the fly
as it needs them. When it detects that a program it hasn't seen before
wants to open a port, it'll ask your permission. Whether you choose to
grant or deny the request, Windows Firewall makes a new rule, and that
rule remains in effect indefinitely, or until you change it.
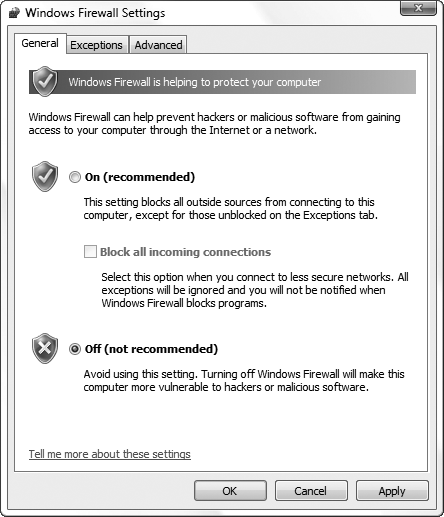
But
there are times when the firewall blocks connections without asking,
mostly because of its default settings. If you suspect that Windows
Firewall is preventing an application from working, open the Windows
Firewall window in Control Panel, click the Turn Windows Firewall on or off link on the left, select Off (Figure 3), and click OK. If the program starts working, then Windows Firewall is the culprit; otherwise, the problem lies elsewhere.
If
it turns out that Windows Firewall is to blame, all you need to do is
create a new rule to permit your application to do what it needs to do.
Don't
head to the Windows Firewall window in Control Panel; that tool is
extremely limited, in that it only lets you create simple exceptions
(rules) that either give a single application free reign, or open a
port that any application can use (never both at the same time).
Instead, use the Windows Firewall with Advanced Security tool, described
next. |
|
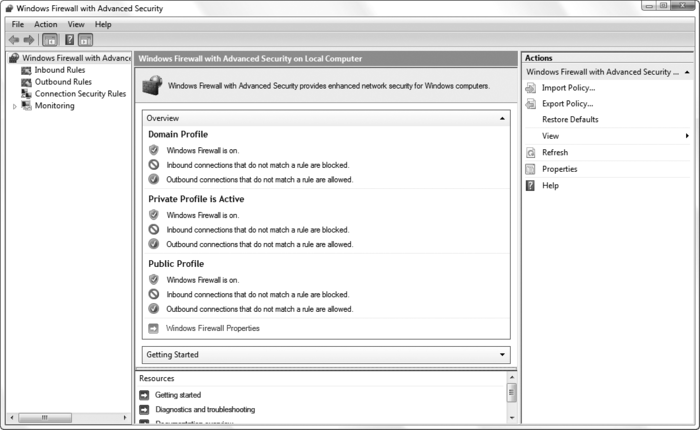
Open the Start menu, type wf.msc in the Search box and press Enter to open the Windows Firewall with Advanced Security window, shown in Figure 4.
Click the Inbound Rules category in the left pane, and then click New Rule in the right pane to show the New Inbound Rule Wizard (Figure 5).
For the Rule Type, choose one of the following:
Program
Use this to give a
specific application free reign over your Internet connection. This is
the easiest way to fix an application that has been broken by Windows
Firewall's restrictions, but it can be risky if you're not exactly sure
how that application will use its new freedom.
Port
This option exposes a TCP/IP port that can be used (read exploited) by any application.
Predefined
Choose this if you want
to create a rule for a built-in Windows service. Note that this
selection doesn't start or stop the service, it only instructs Windows
Firewall to permit or block it; use the Services window (services.msc) to enable or disable Windows services.
Custom
Use Custom
if you want to make a rule that involves both a specific application
and a specific port simultaneously, something you can't do with the
Windows Firewall window in Control Panel.
Click Next when you're done; what happens next depends on the type of rule you're creating.
If you chose Program or Custom in step 3, the subsequent Program step lets you associate the rule with all programs, or a specific .exe file.
If you chose Port or Custom in step 3, the subsequent Protocol and Ports step asks you to specify a port number. Most of the time, you'll want to select TCP from the Protocol type list and Specific Ports from the Local port list.
Next, the Scope
step gives you the opportunity to fine-tune the rule by providing the
IP addresses of the PCs involved in the connection. The local IP address
(the top box) is basically your PC, so in most cases, you'll want to
leave the Any IP address default selected. But below, you can select These IP addresses
and then add the addresses of specific remote PCs; that way, you can be
extra careful and, say, open a port only when a trusted PC wants to
connect.
The Action
step is more or less self-explanatory. By default, Windows Firewall
blocks all inbound data except when a rule instructs it to let the data
through, so typically you'll want to choose Allow the connection here.
The Profile step lets you choose when this rule is in effect; this is covered in more detail shortly.
Finally, use the Name and Description fields to label your new rule so you can find it easily in the list later on.
Click Finish when you're done.
The
new exception will take effect immediately, at which point you can test
the new exception. You may have to experiment with different firewall
rules until your software or service works properly.
In
most of the pages in the Windows Firewall with Advanced Security
window, settings are divided into three "profiles," used at different
times depending on the type of network Windows thinks you're using at
the moment:
Private Profile
The settings in this profile are automatically put into effect when you choose Home or Work
when Windows asks you to select a network location. This is typical of a
home or small-office network, protected by a router, and with folder
and printer sharing .
Public Profile
This is the profile used when you choose Public location, such as when you connect wirelessly to a public hotspot.
Domain Profile
This firewall profile is active when your PC is part of a corporate network with a domain controller.
By
default, the general settings in each of these profiles is more or less
the same, but the inbound and outbound rules are typically different.
To change the settings shown on the summary page in Figure 4, click the Windows Firewall Properties link, and choose the tab corresponding to the profile you want to configure, as shown in Figure 6.
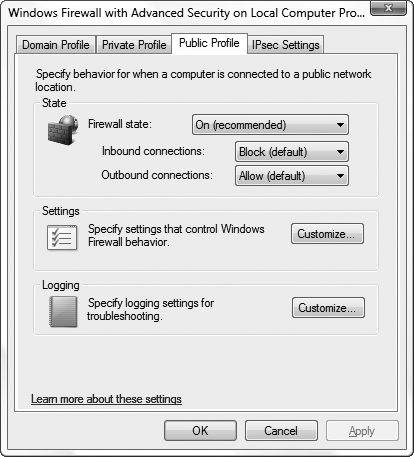
Here, you can make a pretty substantive change: from the Outbound connections list, select Block
to give Windows Firewall control over data flowing in both directions
(rather than just inbound data). This option won't necessarily be
trouble-free until you take the time to customize the outbound rules in
the main window. But it can, for instance, let you contain a virus
outbreak on a PC without completely severing the network connection you
may need in order to make repairs.
Click the Customize button in the Logging
section to have Windows Firewall keep a log of data it blocks in a text
file you choose. Although logging enables you to see exactly what the
firewall is doing behind the scenes, the real value is in
troubleshooting. For instance, if you know Windows Firewall is
interfering with a specific application, but you want to know exactly
what the application is trying to do before you grant it permission,
check the log.
3.2. Alternatives to Windows Firewall
Windows
Firewall that comes with Vista is much better than the XP version, but
it still may not provide the ease-of-use or flexibility of a third-party
program. Here are some alternative solutions:
Be
careful, however, when installing and configuring a third-party
firewall solution, including the ones discussed here. Overly strict
firewall rules may break some software on your system. Worse yet, overly
lenient rules may not protect your computer adequately and only give
you a false sense of security. Check out the PC Flank Leaktest at http://www.pcflank.com/ if you want to test your firewall. |
|
If
all you need to do is block a specific program, you can use Windows
Defender. Just open Windows Defender in Control Panel, click the Tools button at the top of the window, and then click the Software Explorer link. From the Category list, choose Network Connected Programs,
and then select the application you want to block in the list (it must
be currently running and making use of the connection). Then, click
either End Process or Block Incoming Connections,
depending on what you want to do. (Strangely, it won't let you block
Microsoft programs, but I suppose every company is entitled to a little
vanity.)
No matter which
firewall solution you choose, however, you'll most likely still need to
take the time to configure custom rules using a similar procedure to the
one described earlier in this section.