5. Managing Trusts
Trust relationships make it easier to share security
information and network resources between domains. As was already
mentioned, standard transitive two-way trusts are automatically created
between the domains in a tree and between each of the trees in a
forest. Figure 1 shows an example of the default trust relationships in an Active Directory forest.
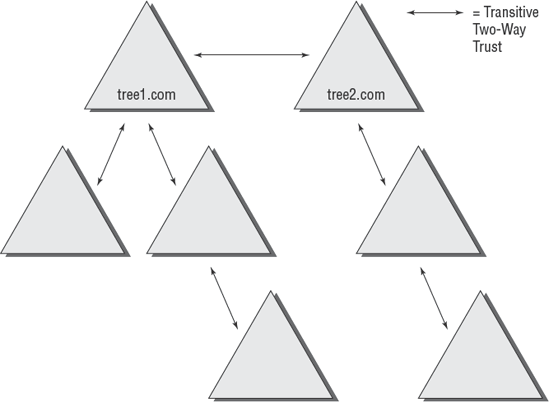
When configuring trusts, here are two main characteristics you need to consider:
Transitive trusts
By default, Active Directory trusts are transitive trusts.
The simplest way to understand transitive relationships is through an
example like the following: If Domain A trusts Domain B and Domain B
trusts Domain C, then Domain A implicitly trusts Domain C. If you need
to apply a tighter level of security, trusts can be configured as
intransitive.
One-way vs. two-way
Trusts can be configured as one-way or two-way relationships. The default operation is to create two-way trusts or bidirectional trusts.
This makes it easier to manage trust relationships by reducing the
trusts you must create. In some cases, however, you might decide
against two-way trusts. In one-way relationships, the trusting domain
allows resources to be shared with the trusted domain, but not the
other way around.
When domains are added together to form trees and
forests, an automatic transitive two-way trust is created between them.
Although the default trust relationships work well for most
organizations, there are some reasons why you might want to manage
trusts manually:
You may want to remove trusts between
domains if you are absolutely sure that you do not want resources to be
shared between domains.
Because of security concerns, you may need to keep resources isolated.
In addition to the default trust types, you can also configure the following types of special trusts:
External trusts
You use external trusts
to provide access to resources on a Windows NT 4 domain or forest that
cannot use a forest trust. Windows NT 4 domains cannot benefit from the
other trust types that are used in Windows Server 2008, so in some
cases, external trusts could be your only option. External trusts are
always nontransitive, but they can be established in a one-way or
two-way configuration.
Default SID filtering on external trusts
When you set up an external trust, remember that
it is possible for hackers to compromise a domain controller in a
trusted domain. If this trust is compromised, a hacker can use the
security identifier (SID) history attribute to associate SIDs with new
user accounts, granting themselves unauthorized rights (this is called
an elevation-of-privileges attack). To help prevent this type of
attack, Windows Server 2008 automatically enables SID filter
quarantining on all external trusts. SID filtering allows the domain
controllers in the trusting domain (the domain with the resources) to
remove all SID history attributes that are not members of the trusted
domain.
Realm trusts
Realm trusts
are similar to external trusts. You use them to connect to a
non-Windows domain that uses Kerberos authentication. Realm trusts can
be transitive or non-transitive, one-way or two-way.
Cross-forest trusts
Cross-forest trusts
are used to share resources between forests. They have been used since
Windows Server 2000 domains and cannot be intransitive, but you can
establish them in a one-way or a two-way configuration. Authentication
requests in either forest can reach the other forest in a two-way
cross-forest trust.
Selective authentication vs. forest-wide authentication
Forest-wide authentication on a forest trust
means that users of the trusted forest can access all the resources of
the trusting forest. Selective authentication means that users cannot
authenticate to a domain controller or resource server in the trusting
forest unless they are explicitly allowed to do so. Exercise 2 will show you the steps to change forest-wide authentication to selective authentication.
Shortcut trusts
In some cases, you may actually want to create
direct trusts between two domains that implicitly trust each other.
Such a trust is sometimes referred to as a shortcut trust and can improve the speed at which resources are accessed across many different domains.
|
Perhaps the most important aspect to remember regarding trusts is that creating them only allows
you to share resources between domains. The trust does not grant any
permissions between domains by itself. Once a trust has been
established, however, systems administrators can easily assign the
necessary permissions.
|
|
Exercise 2
walks you through the steps you need to take to manage trusts. In this
exercise, you will see how to assign trust relationships between
domains. In order to complete the steps in this exercise, you must have
domain administrator access permissions.
Open the Active Directory Domains And Trusts administrative tool by clicking Start => Administrative Tools => Active Directory Domains And Trusts.
Right-click the name of a domain and select Properties.
Select
the Trusts tab. You will see a list of the trusts that are currently
configured. To modify the trust properties for an existing trust,
highlight that trust and click Properties.
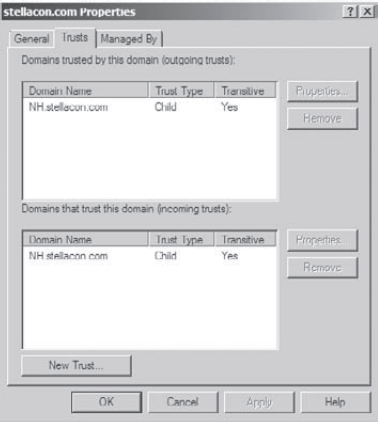
The
Properties window for the trust displays information about the trust's
direction, transitivity, and type, along with the names of the domains
involved in the relationship. Click Cancel to exit without making any
changes.
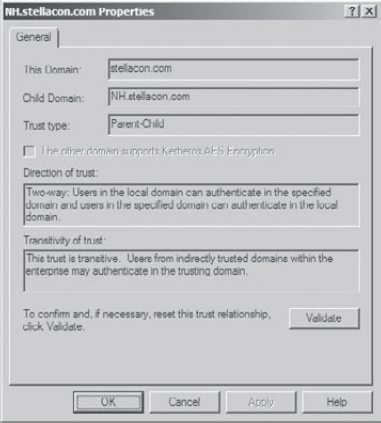
To
create a new trust relationship, click the New Trust button on the
Trusts tab. The New Trust Wizard appears. Click Next to proceed with
the wizard.
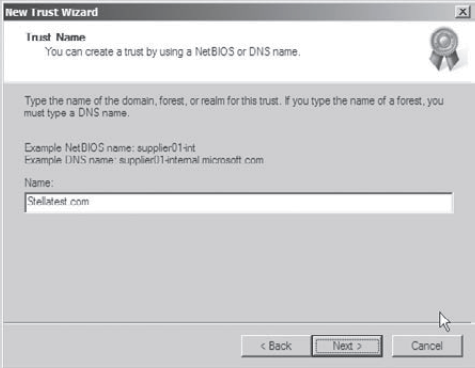
On
the Trust Name page, you are prompted for the name of the domain with
which the trust should be created. Enter the name of the domain and
click Next.
On
the Trust Type page, you would normally choose the Trust With A Windows
Domain option if you know that the other domain uses a Windows domain
controller. In order to continue with this exercise (without requiring
access to another domain), it is important to choose the Realm Trust
option. This selection allows you to walk through the process of
creating a trust relationship without needing an untrusted domain in
the Active Directory environment. Click Next when you are done.
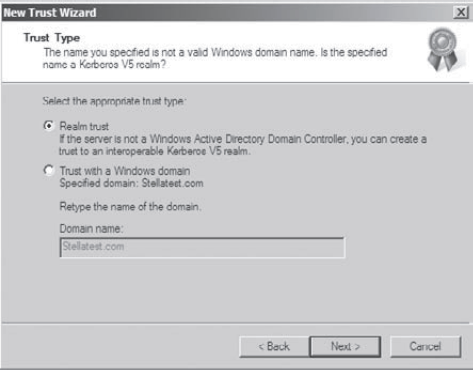
On
the Transitivity Of Trust page, you choose whether the trust is
transitive or intransitive. Choose the Nontransitive option and click
Next to continue.
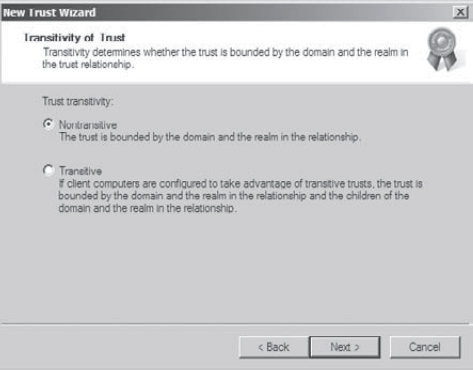
On
the Direction Of Trust page, you select the direction of the trust. If
you want both domains to trust each other, you select the two-way
option. Otherwise you select either One-Way: Incoming or One-Way:
Outgoing, depending on where the affected users are located. For the
sake of this exercise, choose One-Way: Incoming and then click Next.
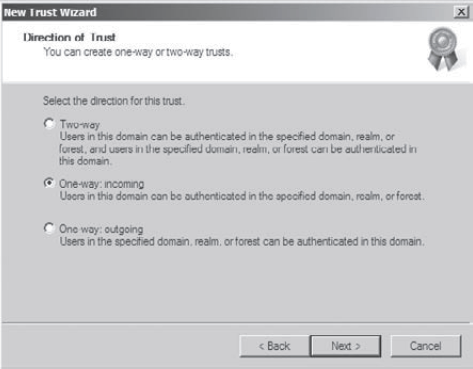
On the Trust Password page, you need to specify a password that should be used to administer the trust. Type P@ssw0rd
and confirm it. Note that if there is an existing trust relationship
between the domains, the passwords must match. Click Next to continue.
Now
you see the Trust Selections Complete page that recaps the selections
you have made. Because this is an exercise, you don't actually want to
establish this trust. Click Cancel to cancel the wizard without saving
the changes.
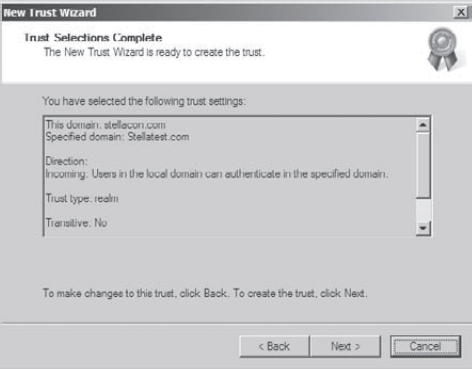
Exit the trust properties for the domain by clicking Cancel.
To Enable Selective Authentication
In the console tree, right-click the name of a domain and select Properties.
Select
the Trusts tab. Under either Domains Trusted By This Domain (Outgoing
Trusts) or Domains That Trust This Domain (Incoming Trusts), click the
forest trust that you want to administer, and then click Properties.
On the Authentication tab, click Selective Authentication, and then click OK.