How Do I Know if a Wireless Network Is Secure?
There is no way to guarantee complete security on a
wireless network. However, you can take some precautions to help
minimize security risks when you use a wireless network.
Whenever possible, connect only to wireless
networks that require a network security key or password or have some
other form of security, such as a certificate. The information sent over
these networks is encrypted, which can help protect your computer from
unauthorized access. When you view available wireless networks on the
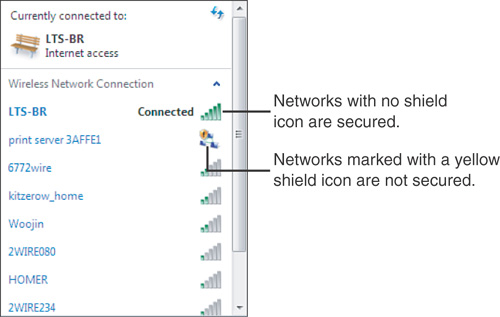
Connect to a Network window, wireless networks that have not enabled
security will be identified with a yellow icon (see Figure 1).
Before you connect to a network provided by a
wireless Internet service provider (ISP), such as a public network in a
coffee shop or an airport, read the privacy statement carefully and make
sure that you understand which files, if any, are saved to your
computer and what type of information the network provider collects from
your computer.
Your best guarantee of
privacy, however, is to be vigilant about what’s allowed to enter your
computer. Remember the oft-repeated warnings about not opening email
from any source you don’t recognize, and be extra careful about
responding to any request for personal information, including entering a
user ID and password upon logging in. If the yellow icon has appeared
for the network you’re logging in to, at least you’ll know that you are
on a public network, and you can take appropriate precautions. Make sure
your antispam and anti-malware software is up-to-date when logging on
to coffee shop and other public networks.
What Makes a Home or Work Network Safe to Connect To?
Not all home or work networks are safe. One or
more of the other users of your home network may, for instance, have
accidentally downloaded a keylogger while playing an online game or
downloading some clip art.
To help ensure that a home or work network is safe to connect to, make sure that it has the following:
For wireless networks, a wireless
connection encrypted with Wi-Fi Protected Access (WPA or WPA2). (WPA2 is
preferred because it is more secure than WPA.)
For
all networks, a firewall or other device with network address
translation (NAT), which is connected between your computer or wireless
access point and your cable or DSL modem (see Figure 2).
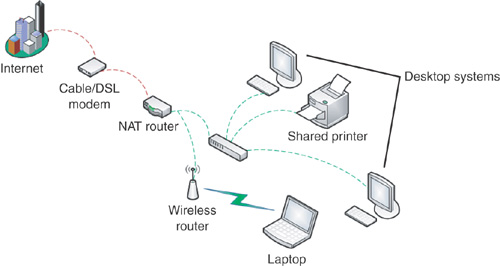
Many modern cable and DSL modems include both NAT
and wireless capabilities, built in. Wireless routers, in addition, are
also often capable of acting as NAT devices. Our recommendation is that,
if you have a broadband connection, you have some form of NAT
capability between the modem and your computer—either directly (built in
to the cable/DSL modem) or as a standalone device.
In Figure 10.4, you can see an example where the NAT device and the wireless router are separate from the cable/DSL modem.
How Windows Firewall Affects Network Locations
One
difference between your home or work networks and a public network is
how this affects the protection levels on your computer. At home, or on a
work network, you should be able to count on a hardware firewall, such
as a NAT router, protecting your computer from prying eyes. When you are
on a public network, however, you don’t have that option and you are
forced to rely on a software firewall to protect your computer.
So, when you are on your home or work networks,
you are generally more willing to allow various programs to run and
access the Internet. Why? Because you are already protected from
unauthorized access.
The public network location blocks certain
programs and services from running to help protect your computer from
unauthorized access while you’re connected to a network in a public
place. If you’re connected to a public network and Windows Firewall is
turned on, some programs or services might ask you to allow them to
communicate through the firewall so that they will work properly.
When you allow a program to communicate through
the firewall, it’s allowed for every network with the same location as
the network you’re currently
connected to. For example, if you connect to a network in a coffee shop
and choose Public network as the location and then you unblock an
instant message program, that program will be unblocked for all public
networks that you connect to.
If you plan to unblock
multiple programs while you’re connected to a public network, consider
changing the network location to home network or work network. It might
be safer to change this one network than affect every public network you
connect to from that point on. But remember that if you make that
change, your computer will be visible to others on the network, and this
can be a substantial security risk.