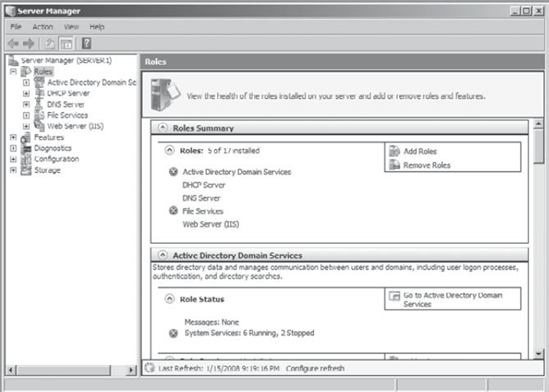
1. Understanding Server Manager
Windows Server 2008 combines many of these tools in a new Microsoft Management Console (MMC) snap-in called Server Manager.
With Server Manager, an administrator can view the server configuration
and installed roles. Server Manager also includes links for adding and
removing features and roles (see Figure 1).
Server Manager is your one-stop shopping MMC
snap-in. By that, I mean that you can take care of all your server
management needs in one easy interface.
Active Directory Certificate Services
Active Directory Domain Services
Active Directory Federation Services
Active Directory Lightweight Directory Services
Active Directory Rights Management Services

2. Configuring Active Directory Certificate Services
Using Active Directory Certificate Services (AD CS),
administrators configure public key certificate services. AD CS
security allows a private key to be combined with objects (such as
users and computers), devices (such as routers), or services. The
public-key infrastructure greatly increases data security.
In Windows Server 2008, AD CS provides services for
creating and managing public key certificates used in software security
systems that employ public key technologies. Organizations can use AD
CS to enhance security by binding the identity of a user, device, or
service to a corresponding private key. AD CS also includes features
that allow you to manage certificate enrollment and revocation in a
variety of environments.
Think of a digital certificate as a carrying case
for a public key. A certificate contains the public key and a set of
attributes, like the key holder's name and email address. These
attributes specify something about the holder: their identity, what
they're allowed to do with the certificate, and so on. The attributes
and the public key are bound together because the certificate is
digitally signed by the entity that issued it. Anyone who wants to
verify the certificate's contents can verify the issuer's signature.
Certificates are one part of what security experts call a public-key infrastructure (PKI). A PKI has several different components that you can mix and match to achieve the desired results.
Applications supported by AD CS include
Secure/Multipurpose Internet Mail Extensions (S/MIME), secure wireless
networks, Virtual Private Networks (VPN), IP security (IPsec),
Encrypting File System (EFS), smart card logon, Secure Socket
Layer/Transport Layer Security (SSL/TLS), and digital signatures.
The following are some of the AD CS components:
Cert Publishers group
Certificates are used to increase security by
allowing for strong authentication methods. User accounts are placed
within the Cert Publishers group if they need to be able to publish
security certificates. Generally, these accounts are used by Active
Directory security services.
PKI-savvy applications
These applications allow you and your users to
do useful things with certificates, like encrypt email or network
connections. Ideally, the user shouldn't have to know (or even
necessarily be aware) of what the application is doing—everything
should work seamlessly and automatically. The best-known examples of
PKI-savvy applications are web browsers like Internet Explorer and
Firefox and email applications like Outlook and Outlook Express.
Certificate templates
Certificate templates act like rubber stamps: By
specifying a particular template as the model you want to use for a
newly issued certificate, you're actually telling the CA which optional
attributes to add to the certificate, as well as implicitly telling it
how to fill in some of the mandatory attributes. Templates greatly
simplify the process of issuing certificates because they keep you from
having to memorize the names of all the attributes you might
potentially want to put in a certificate. In Windows Server 2008,
multiple templates are available and you also have the ability to
secure templates using template permissions.
Online Responder service
Some applications—including S/MIME, SSL, EFS,
and smart cards—need to validate the status of certificates. The Online
Responder service authoritatively responds to such requests.
Certification practice statement
A Certification practice statement (CPS) is a
statement that is issued by a certificate creator. It represents the
creator's practices for issuing and validating certificates. The CPS
represents the technical, procedural, and personnel policies and
practices of the issuing certification authority (CA) organization.
Enrollment agents
Enrollment agents are administrators who have
the ability to enroll users into the certificate services program.
Enrollment agents can issue and manage certificate requests.
Network device enrollment service (NDES)
Network devices such as routers do not have
accounts in the Active Directory Domain. The NDES allows such network
devices to obtain certificates.
Web enrollment
With web enrollment, users can easily request
certificates and retrieve certificate revocation lists (CRLs) through a
web browser.
2.1. Installing Active Directory Certificate Services
When you are installing AD CS, the installation
wizard will walk you through the installation process, and you will
need to answer some configuration questions. If at any time during
installation you do not know how to configure an option, you can click
on the help link for explanations. Here are some of the AD CS options
that you can configure during the installation:
Certificate authorities (CAs)
Certificate authorities issue, revoke, and
publish certificates for their clients; big CAs like Thawte and
VeriSign may do this for millions of users. You can also set up your
own CA for each department or workgroup in your organization if you
want.
Each CA is responsible for choosing what attributes
it will include in a certificate and what mechanism it will use to
verify those attributes before it issues the certificate.
There are three types of CA:
Enterprise Root CAs (automatically
integrated with Active Directory) are the most trusted CAs of the
hierarchy. They hold the certificates that you issue to the users
within your organization.
Stand-Alone Root CAs hold the CAs that you issue to Internet users.
Subordinate
CAs are below the Enterprise and Stand Alone Root CAs in the hierarchy.
The Enterprise or Stand Alone Root CAs give certificates to the
Subordinate CAs, which in turn issue certificates to objects and
services.
Cryptographic service provider (CSP)
The CSP is the mechanism that is responsible for
authentication, encoding, and encryption services that Windows-based
applications access through the Microsoft Cryptography application
programming interface (CryptoAPI). Every CSP offers a unique
implementation of the CryptoAPI. Some CSPs offer a strong cryptographic
algorithm, while others use hardware components, such as smart cards.
Hash algorithm
An algorithm that produces a hash value of some piece of data, such as a message or session key, is called a hash algorithm.
If you use a well-designed hash algorithm, the hash value changes when
the data changes. Due to this characteristic, hash values are useful
when you are trying to detect whether any modifications have been made
to data (such as a message). Also, a well-designed hash algorithm makes
it almost impossible for two independent inputs that have the same hash
value.
Exercise 1 will show you the steps you need to follow to install the AD CS server.
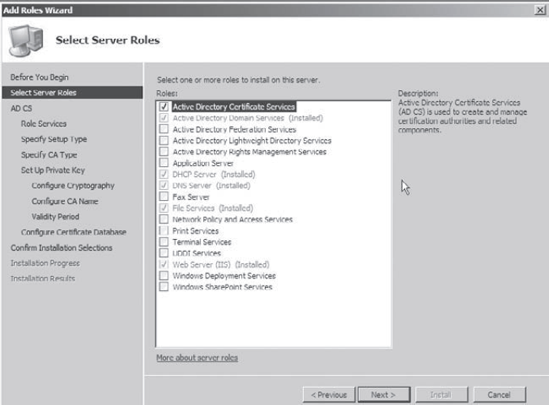
Open the Server Manager MMC by selecting Start => Administrative Tools => Server Manager. Under Roles Summary, click the link labeled Add Role. On the Select Server Roles screen, check the box next to Active Directory Certificate Services and click Next to continue.
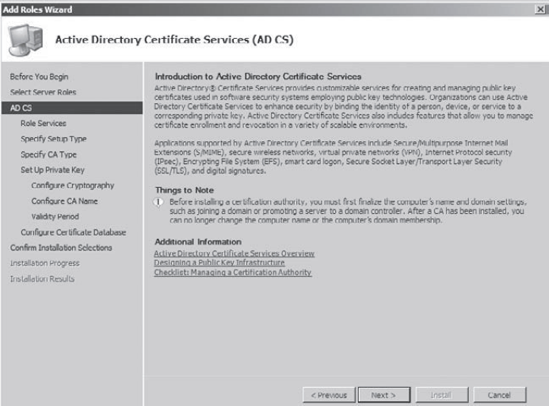
At the Active Directory Certificate Services (AD CS) screen, read the explanation of AD CS, then click Next.
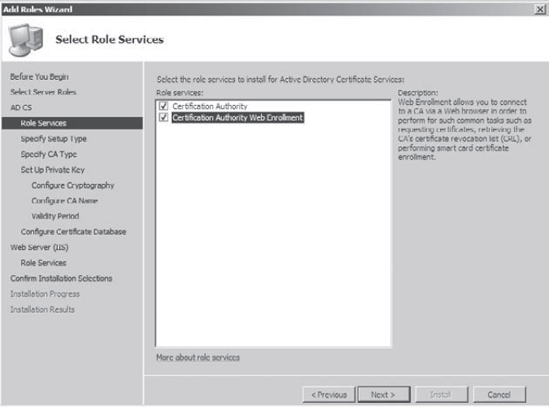
At
the Select Role Services screen, make sure the Certificate Authority
and Certificate Authority Web Enrollment boxes are both checked.
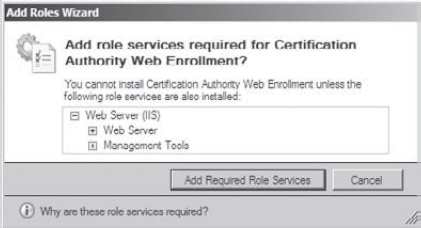
When
you check the Certificate Authority Web Enrollment box, the Add Roles
Wizard may appear, stating that you need to install supporting
services. If you see this wizard, click the Add Required Role Services
button. Otherwise go on to step 7.
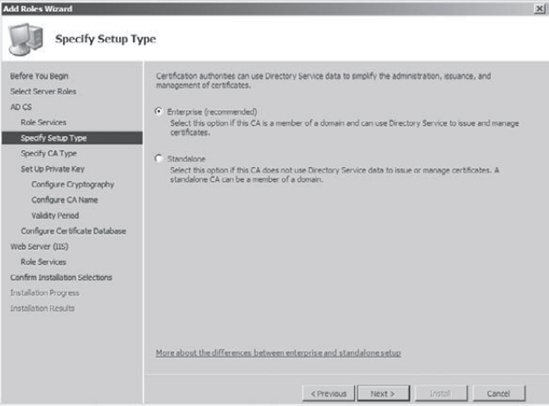
Once both check boxes are checked on the Select Role Services screen, click Next. At the Specify Setup Type screen, choose Enterprise (Recommended) and click Next.
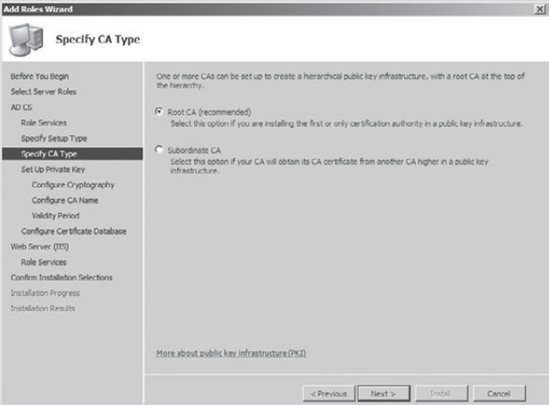
The
Specify CA Type screen appears. This is where you decide what type of
CA you will use. If you have only one CA or this is the first CA,
choose Root CA (Recommended). If you are going to receive your
certificates from a higher CA (either your own root or a third-party
company) choose Subordinate CA. Click Next.
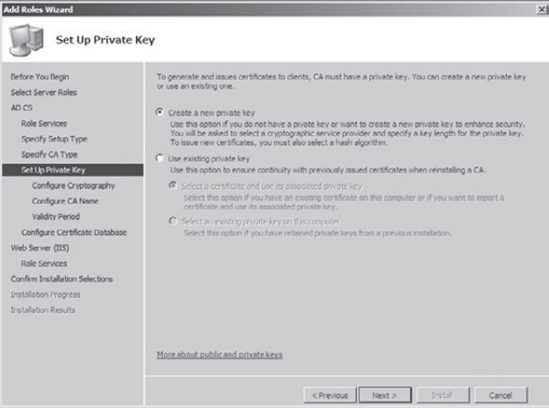
At the Set Up Private Key screen, choose Create A New Private Key, then click Next. This
option allows you to create a new key for our certificate server. You
would choose Use Existing Private Key if you were reinstalling or using
previously issued keys.
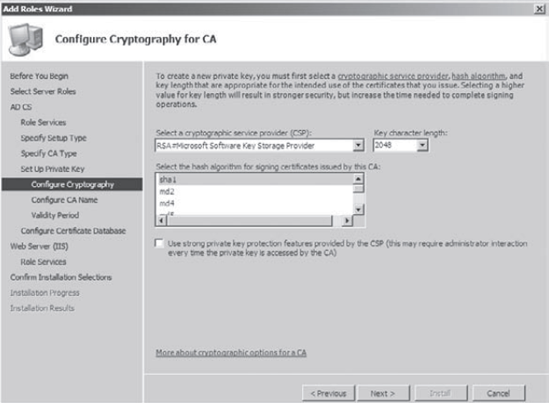
When
the Configure Cryptography For CA screen appears, you must select a
CSP. Choose RSA#Microsoft Software Key Storage Provider. Make sure that
the Key Character Length is 2048 and choose sha1 for the hash
algorithm. Click Next.
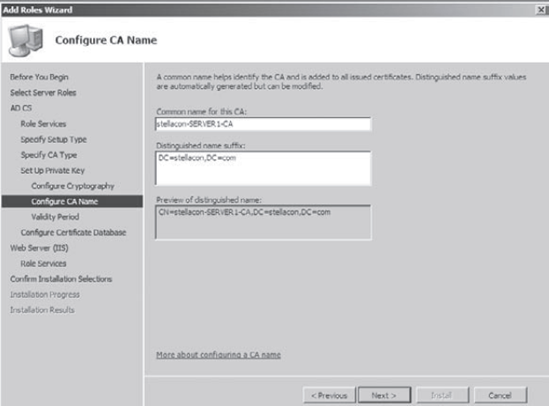
At
the Configure CA Name screen, accept the defaults and click Next. The
common name is the general name that is used to help identify the CA
and the common name is also added to all issued certificates.
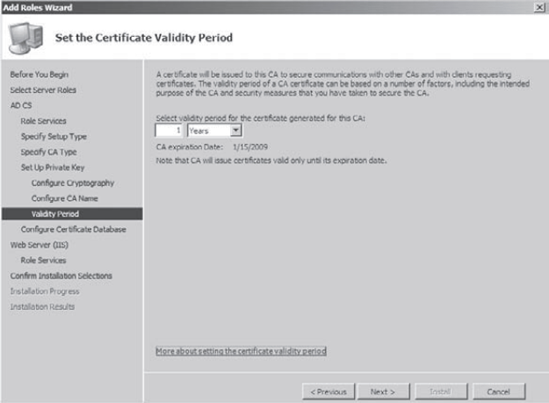
At the Set The Certificate Validity Period screen, change the default to 1 Years and click Next.
The
Configure Certificate Database screen will prompt you to enter the
storage location for your database files. Accept the defaults and click
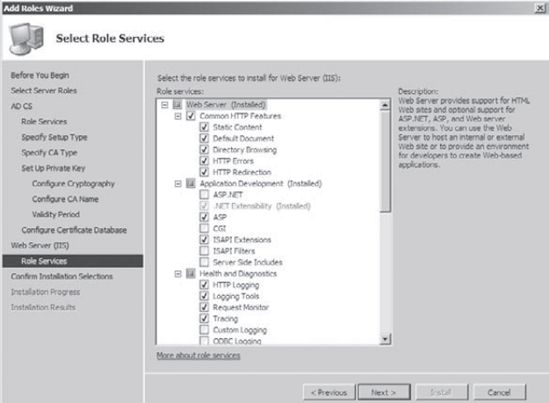
Next. The Web Server IIS screen appears. This is an informational screen. Click Next. At
the Select Role Services screen, click Next. These are all the services
you need to install IIS so it works with the certificate server.
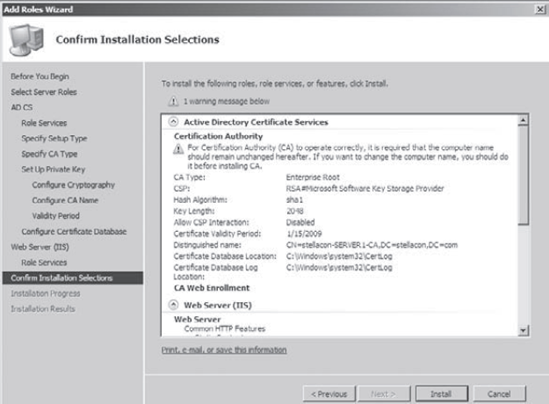
At
the Confirm Installation Selections screen, you will see a warning
message stating that the name of this server must remain unchanged for
the certificate server to continue to run properly. Click Install.
At
the Installation Results screen, you will see the status of the
installation. You should see an Installation Succeeded message. Click
Close and exit the Server Manager.
|