Utilizing Security Templates
Security
templates are a practical and effective means to apply standardized
security policies and configurations to multiple systems in an
environment. These security templates can be customized to meet the
minimum security requirements of a particular organization, and can be
applied to client computers as well as to servers using the Security
Configuration and Analysis Microsoft Management Console (MMC) snap-in.
By
utilizing the automatic deployment of security templates to client PCs,
administrators can ensure that computers are identically configured and
utilize available security measures, even if the system is not able to
be managed by Group Policy Objects (GPOs).
Tip
Microsoft
provides several security templates based on functional roles within a
network environment. These can easily be applied to client computers
and servers alike. However, organizations often have unique needs that
are not met completely by these default templates so, as a best
practice, administrators should always customize the security template
to address particular application and access needs.
Using the Security Configuration and Analysis Tool
The
Security Configuration and Analysis tool is a utility that can apply
security templates to computers. It compares a computer’s security
configurations against an administrator-defined security template, and
reports any differences found between the two. Furthermore, when the
security configuration on the computer does not match the settings specified in the template, you can use the tool to update the system accordingly.
This
utility has two modes of operation: analysis and configuration. An
often-overlooked best practice is to analyze the system prior to making
any changes so that you have a baseline frame of reference.
To run the Security Configuration and Analysis tool and analyze a computer, perform the following steps:
1. | Start the Microsoft Management Console by selecting Start, Run, typing MMC in the Open text box, and then clicking OK.
|
2. | Select File, click Add/Remove Snap-in, and then click Add.
|
3. | In the Add Standalone Snap-in window, select Security Configuration and Analysis, click Add, and then click Close.
|
4. | On the Add/Remove Snap-in page, click OK.
|
5. | In the MMC, right-click the Security Configuration and Analysis snap-in, and select Open Database.
|
6. | Type a database name, select a location to store the database, and then click Open.
|
7. | Select
a security template from those listed. If you want to implement a
security template from another location, use the navigation tools to
change to the directory where the .inf file is located. After you have selected the appropriate .inf file, click Open.
|
8. | Back in the MMC, right-click the Security Configuration and Analysis snap-in, and choose Analyze Computer Now.
|
9. | Enter a path to store the generated log file, and click OK to continue.
|
After
the System Security Analysis has completed, the utility displays the
security settings that are configured in the template you selected, and
what is currently configured on the computer. Items for which the
computer is not in compliance with the policy appear with a red “x”
beside them, as shown in Figure 1.
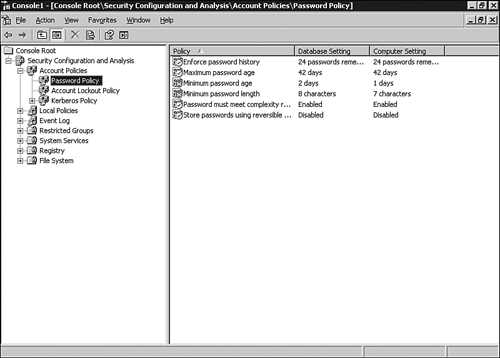
If you want to configure the system with the security settings in the template, you can do so by performing a few extra steps:
1. | In the MMC, right-click the Security Configuration and Analysis snap-in.
|
2. | Select Configure Computer Now.
|
3. | Enter a path for the error log to be written to, and then click OK.
|
Customizing Security Templates
An
administrator might want to use custom security templates for several
reasons. The organization might want a simple method of ensuring that
attached computer systems meet with defined minimum security criteria.
They might desire to ensure configured security settings that work for
a particular application can be replicated to other servers of the same
nature.
Larger organizations often have
the need for customized security templates. For example, a member of
the Internal Auditing department might need to regularly connect to
employee hard drives, whereas the receptionist is only allowed basic
Internet access. By applying different security settings to each of
these machines, you can help the company ensure people have access to
the data they need, and not to the resources they don’t.
Tip
You
can download and implement security templates provided by Microsoft,
the National Security Agency (NSA), or the National Institute of
Standards and Technology (NIST). These templates can be used as
baselines, and can be customized to meet the needs of your particular
environment. After being customized, you can distribute them to
appropriate systems in your organization with minimal effort.
Windows
Server 2003, Windows Vista, and Windows XP Professional are equipped
with the Security Templates MMC snap-in that enables administrators to
quickly and easily customize settings on individual systems. Loading
this tool is similar to the Security Configuration and Analysis tool
discussed previously. To add the snap-in, follow these steps:
1. | Start the Microsoft Management Console by selecting Start, Run, typing MMC in the Open text box, and then clicking OK.
|
2. | Select File, click Add/Remove Snap-in, and then click Add.
|
3. | In the Add Standalone Snap-in window, select Security Templates, click Add, and then click Close.
|
4. | On the Add/Remove Snap-in page, click OK.
|
When
the Security Templates snap-in is expanded, it displays the default
search path to where the built-in security templates are stored. By
default, this is the c:\windows\security\templates directory.
Other paths can be opened to display other security templates that
might reside on the system. Expand the default directory to see the
available templates. Rather than editing these default templates, it is
recommended that you select the one you are going to use as a baseline,
right-click it, and save it as a new template.
After
you have created the new template, expand it to display all of the
modifiable security settings. From here, you can configure the template
to apply the security settings you want.
After
you have completed customizing the template, it is an easy process to
save the file to an accessible network share, and then use the Security
Configuration and Analysis tool to apply it to the appropriate systems.