Collections
Collections are
logical groupings of computer systems, users, or groups. They identify
objects for a variety of purposes, such as the following:
Pushing software
Viewing inventory
Viewing the result of a query
Providing remote support via remote control and remote tools
Grouping of systems with a common piece of hardware or software
You can populate
collections using a direct membership or query membership rule. Both
these methods allow the administrator to populate a collection.
Collections can have
subcollections. This is useful for organizational reasons as well as for
software distribution, due to the ability to advertise a package to a
collection or its subcollections.
Collection
security gives Configuration Manager administrators the ability to
manage which administrators will have varying levels of access to
specific collections. Configuration Manager 2007 uses an implementation
of WBEM (Web-Based Enterprise Management) security, a standard created
by the DMTF (Distributed Management Task Force).The WBEM security model leverages a class/instance model and is
extremely granular. Most ConfigMgr objects have specific rights, which
you can grant unique to an object.
Discovery
ConfigMgr
discovers resources in a networked environment using a variety of
built-in discovery methods. These discoveries create DDRs, which you can
display in collections and queries. ConfigMgr has six types of
discovery methods:
Active Directory System Group Discovery
Active Directory Security Group Discovery
Active Directory System Discovery
Active Directory User Discovery
Heartbeat Discovery
Network Discovery
The Active Directory
discovery methods have the ability to specify LDAP paths for which you
want to discover objects. Although some discovered objects such as users
and groups are not capable of management, they are useful for reporting
and using in query criteria to populate collections for application
distribution.
Each discovery method has its own schedule, allowing configuration on a recurring interval and at non-peak times.information on discovery methods.
Software Metering
Software metering in
ConfigMgr is passive, collecting data for a specified amount of time
about the usage frequency of applications. Software metering gives
administrators the ability to monitor specific application usage across
the entire enterprise. Unlike in earlier versions,
administrators no longer need to define most commonly used applications
because ConfigMgr creates these rules automatically if an
administrator-specified percentage of the environment is using an
application.
Packages
ConfigMgr uses
packages to distribute software and changes to clients. Think of a
package as a change in a client’s configuration. Historically,
administrators have only thought of packages as software installs.
Packages can be the silent uninstallation of an application, a
remediation package from a desired configuration baseline that has been
strayed from, a change to a Registry key, the startup behavior of a
service, and so on.
Packages are distributed
to DPs where they reside for clients to access. This distributed copy
of the package architecture allows efficient use of bandwidth-sensitive
links and minimizes the impact to the network infrastructure. Clients
can download packages into their local cache and execute them later,
mitigating the scenario where hundreds of clients all run an
installation off a server at the same time.
Once distributed,
packages are advertised to collections, which contain computer, user, or
group resources. This process allows the package command line to
execute according to a strict schedule and set of parameters that
determines how the package will run and how the client operating system
behaves, not only while the package is installing but also after it
completes.
Advertisements
Advertisements
are policies that ConfigMgr clients download and execute on a schedule.
Advertisements define when clients can execute the program in a package
and whether to run it from a distribution point or copy it to their
local cache and run it locally.
By definition,
advertisements require a user to initiate launching the package command.
Mandatory advertisements do not require any user input and are actually
a push-install, opposed to the pull-install used with advertisements in
their default mode. You can use features such as Wake On LAN (WOL) in
conjunction with mandatory advertisements to minimize impact to the
end-user community.
Tip: Using Mandatory Advertisements with WOL
With mandatory
advertisements, the ConfigMgr administrator can keep his enterprise
patched to the level desired, without any user impact or interaction.
Users can shut their computer down when they leave for the day to help
with the company’s green (energy-saving) initiative. An administrator
can push a package out with a mandatory advertisement configured to shut
down the computer on completion of the installation. When the user
arrives the next day and turns on the machine, the startup completes the
reboot cycle needed to complete the patch installation.
Distribution Points
ConfigMgr
administrators can create DPs throughout an enterprise having a large
number of client systems, thus minimizing network traffic over the WAN
and slower links. Distribution points can utilize BITS, but not for
throttling package traffic from the site server to the DP. BITS also
allows checkpoint restarting. In other words, if there was an
interruption to a download at 60% completion, using BITS allows the
download to resume at that point instead of starting over again from the
beginning, which is what happens when clients connect to DPs using
Server Message Block (SMB) traffic. Distribution points can be installed
on a system as either a package share or a server share.
Senders
Senders are located on
primary and secondary sites. Senders define how ConfigMgr sites use
existing network connectivity to manage the connection, ensure the
integrity of transferred data, recover from errors, and close the
connection if no longer needed.
Sender types include the following:
Standard sender
Courier sender
Asynchronous RAS sender
ISDN RAS sender
X25 RAS sender
SNA RAS sender
The most common
sender used is the standard sender, which is the only type required when
there is basic network connectivity across a LAN or WAN. Microsoft
designed the courier sender for sending excessively large packages
across a network with slow links. The purpose of the courier sender is
to create a parcel, which is a collection of files from a package, and
ship the parcel on tape or CD to the remote site location where the
administrator can then load the package into the site.
Addresses
Addresses define a site
code and the security account used to communicate with a remote site.
Addresses also give ConfigMgr administrators the ability to schedule
when traffic can flow between the two sites by priority of the traffic,
as well as the percentage of bandwidth the sites may use during
communications. All communication between ConfigMgr sites use SMB and
travels on TCP port 445. By default, ConfigMgr secures site-to-site
communication by secure key exchange, which only needs to be defined per
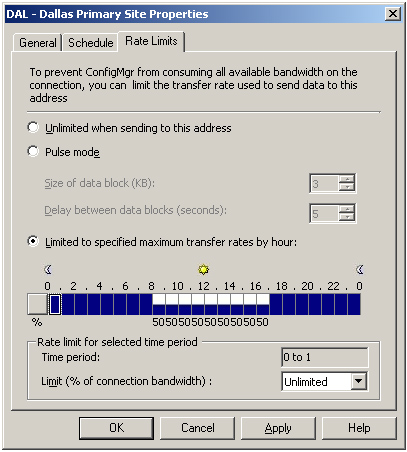
parent/child connection. Figure 5 displays the Rate Limits tab for the Dallas site, limiting the transfer rate used to send data to that site.
BITS
BITS is a
subcomponent of IIS, a component of Windows. Using BITS allows
administrators to prioritize and throttle asynchronous file transfer
between two Windows systems. BITS uses available network bandwidth to
handle transfers, making them transparent to the end user’s experience.
BITS monitors network traffic on the local network interface and
throttles itself accordingly. BITS also provides the ability to continue
transferring data when network connectivity is intermittent or
unreliable by leveraging checkpoint restarting.
Task Sequences
Task sequences are new in
ConfigMgr 2007. Task sequences consist of a series of customizable tasks
or sequentially performed steps running in an unattended fashion on a
system. Task sequences often are only thought of in the context of
operating system deployments. Because you can advertise task sequences
directly to client systems, you can use them for a multitude of things,
including chaining a series of actions together. Task sequences allow
each action in the sequence to be independent of the other, let you
change the order of tasks, and allow each action to have its behavior
individually defined if errors occur. Task sequences consist of actions,
custom and built-in actions, conditions, and steps. Task sequences also
support grouping of actions for organizational purposes.