Debugging Kerberos
One of the hardest things
to debug in the organization is security, especially when the security
is passed through several middle-tier applications and the system
administrator does not have access to intercept the request in the
middle.
However, the most
common problems users experience is that the front application will
load, but there may be some areas that may be missing data. For example,
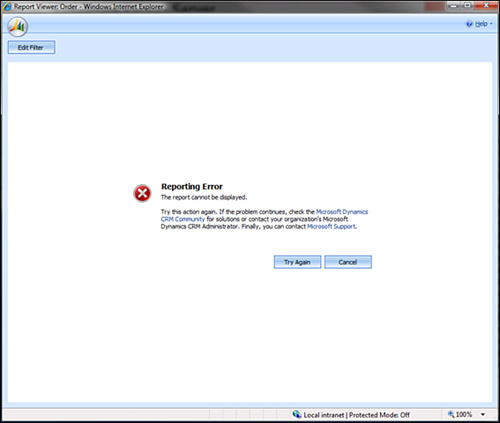
when users open the Microsoft CRM Dynamics application and click the
Reports section, they will be able to view the list of the reports. When
they click it, they will be allowed to choose the filter criteria. When
they try to run the report, however, they will get a CRM authentication
failure (as shown in Figure 14).
To debug Kerberos, you
have to start debugging on the server side first and then move to the
client. Microsoft has created a variety of tools to help facilitate
this. Here is a list of some server-side tools (further details in the
next section):
IIS utilities
Windows Resource Kit
Kerberos logging
To complete the investigation/debugging, here are some client-side tools (detailed later):
IIS Utilities (Installed on the Server)
You can find the IIS utility Authentication and Access Control Diagnostics 1.0 (x86) at http://www.microsoft.com/downloads/details.aspx?FamilyId=E90FE-4A21-4066-BD22-B931F7572E9A&displaylang=en.
This utility must be
installed on the web server. You can save the output as an XML file and
review it for configuration problems (as shown in Figure 15).
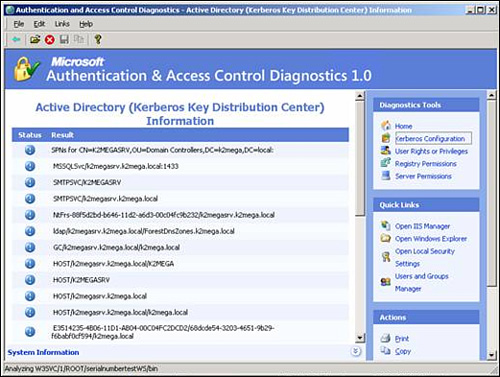
This tool helps highlight misconfigured SPNs quickly.
Windows Resource Kit
The Resource Kit
contains a couple of very useful utilities to debug Kerberos. In this
section, we demonstrate the KerbTray and the kList tools specifically.
You can download the Windows Resource Kit from the Microsoft website at http://www.microsoft.com/windows2000/techinfo/reskit/tools/existing/kerbtray-o.asp.
KerbTray (client-side tool)
This tool runs in the system tray and displays the active tickets issued to the client computer and user.
kList
This
tool lets you view the tickets in a command-line console. You can also
purge specific tickets to debug reenrollment of tickets.
You can also view the ticket-granting service (TGS).
The following code sample shows via kList the ticket-granting authority to which the user is connected):
C:\Program Files\Windows Resource Kits\Tools>klist tgt
Cached TGT:
ServiceName: krbtgt
TargetName: krbtgt
FullServiceName: rbhaiya
DomainName: Domain.Local
TargetDomainName: Domain.Local
AltTargetDomainName: Domain.Local
TicketFlags: 0x40e00000
KeyExpirationTime: 0/40/4 0:00:10776
StartTime: 10/8/2008 16:57:52
EndTime: 10/9/2008 2:57:52
RenewUntil: 10/15/2008 16:57:52
TimeSkew: 10/15/2008 16:57:52
The next code sample shows via kList the tickets owned by the user:
C:\Program Files\Windows Resource Kits\Tools>klist tickets
Cached Tickets: (2)
Server: krbtgt/[email protected]
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
End Time: 10/9/2008 2:57:52
Renew Time: 10/15/2008 16:57:52
Server: HTTP/[email protected]
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
End Time: 10/9/2008 2:57:52
Renew Time: 10/15/2008 16:57:52
Kerberos Logging
To enable Kerberos event logging, change the following Registry value and restart the computer:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters
Registry Value: LogLevel
Value Type: REG_DWORD
Value Data: 0x1
This will give verbose logging in the event logs.