Administration of the
Director role in Lync Server can be performed through a combination of
the Lync Server Control Panel and the Lync Server Management Shell. This
section discusses management of Director services and possible uses for
the web services included in a Director installation.
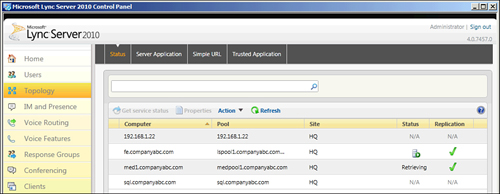
Topology Status
A relatively easy method of
checking the health status of a Director server or pool exists through
the Lync Server Control Panel. To check the status of a Director pool,
perform the following steps:
1. | Open the Lync Server Control Panel.
|
2. | Click Topology.
|
3. | Highlight the server in question, and click the Get service status button.
|
4. | Double-click
the server to drill down further and check the status of individual
services such as the Registrar or web services. Figure 1 shows what the Lync Server Control Panel looks like.
|
Services Management
Managing the Lync Server
services is the extent of administration involved with a Director after
it is installed and configured. Administrators can start, stop, or drain
the Director servers either from the Lync Server Control Panel or the
Lync Server Management Shell. Stopping the services ends all user
sessions, but draining the services enables existing connections to
continue, but stop accepting new connections. This enables an
administrator to prepare a server for maintenance without immediately
impacting users.
To manage the Lync Server services, perform the following steps:
1. | Open the Lync Server Control Panel.
|
2. | Highlight the server to be modified.
|
3. | Click Action and either select Start all services, Stop all services, or Prevent new connections for all services.
|
4. | Alternatively, double-click the server to drill down further and manage the individual services.
|
Load-Balancer Drain
Draining a hardware
load-balancer’s connections to a pool server is a task that should be
done in conjunction with the Prevent new connections for all services
option in the Lync Server Control Panel. The Lync Server services have
no method of managing a hardware load balancer, so if one is used for
the web services traffic, it must be started, stopped, and drained
independently.
Client Version Filter
One
potential use for a Director is to control the client versions
connecting to the Lync Server infrastructure. Because the Director is an
initial sign-in point for any client, perform a filter check at the
sign-in point. To manage which types of clients can connect to a
Director, perform the following steps:
1. | Open the Lync Server Control Panel.
|
2. | Click Clients.
|
3. | Ensure Client Version Policy is highlighted, click New, and select Pool policy.
Note
If a policy is edited at the
Pool level, such as in the previous example, it only applies to the
selected service and pool. The example only enforces the client version
filter at the Director, meaning that an endpoint could sign in to a
front end pool directly without a client check. Edit the global policy
if the client filtering is performed on all pools.
|
4. | Highlight the Director pool name, and click OK.
|
5. | Highlight a client application, such as Office Communicator, and click Modify.
|
6. | Note the Action
at the end of the screen. This can be modified to block or allow with
the option to present a URL to the user, or even upgrade the application
at sign-in. Click OK to save any changes.
|
7. | Add, modify, or remove any specific client applications and versions that the Director pool should check and click Commit.
|
8. | Click the Client Version Configuration menu option.
|
9. | Highlight the Global Policy, click Edit and then Modify.
|
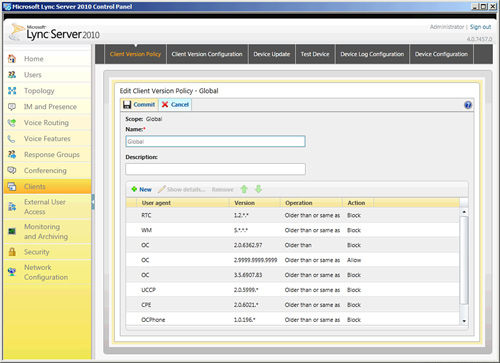
10. | The
default action applies to any client application not listed within the
Client Version Policy. By default, any client application not listed in
the Client Version Policy will be allowed to sign in. Figure 2 shows a sample configuration where all Office Communicator versions will be allowed, but told an upgrade is available.
|
Authentication Methods
A Director has the capability to
use Kerberos, NTLM, or a combination of both to authenticate user
traffic. Kerberos or NTLM can be used for authenticating users
internally, but only the NTLM authentication protocol can be used to
authenticate remote or external users. In the event of an Active
Directory failure, clients can use a certificate issued by Lync Server
to authenticate to servers.
Note
A certificate is neither
issued by nor used by a public key infrastructure. The only purpose for
the certificate is in relation to authenticating Lync Server endpoints.
To configure the setting, open the Lync Server Control Panel and perform the following steps:
1. | Open the Lync Server Control Panel.
|
2. | Click Security.
|
3. | Click Registrar.
|
4. | Click New and select the Director Registrar service.
|
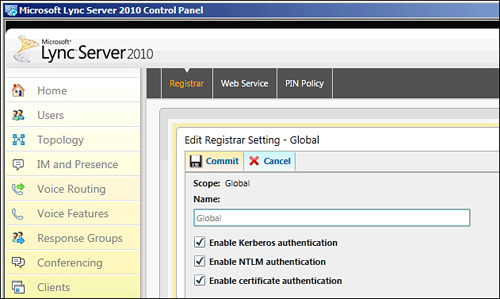
5. | Select the appropriate checkboxes to enable Kerberos, NTLM, or certificate authentication, and click Commit. An example of editing the Global policy that applies to all servers is shown in Figure 3.
 |