Network Access Protection is a ConfigMgr process in
which NAP-capable clients evaluate their compliance with predefined
policies and send this data in as a client Statement of Health (SoH) to
the System Health Validator point (SHV) site system. This evaluation consists
of comparing the updates specified in the NAP policy with what is
installed on the client. ConfigMgr administrators can choose actions to
perform when clients are found to be out of compliance; this process is
known as remediation. Remediation uses existing software update packages to update the client with the software updates feature.
The
systems responsible for the policies, health evaluation, and
remediation are often confused due to ConfigMgr relying on Windows
Server 2008’s Network Policy Server (NPS). ConfigMgr by itself does not
enforce compliance with NAP; it provides a mechanism by which ConfigMgr
clients can produce an SoH with a noncompliant status if they lack
software updates required by the ConfigMgr NAP policies you configure.
A ConfigMgr SHV confirms the health state of the computer as compliant
or noncompliant, and passes this information to the NPS. Policies on
the NPS then determine whether noncompliant computers will be
remediated and, additionally, whether they will have restricted network
access until they are compliant.
NAP is only supported on the following operating systems:
Here are 10 things you should know about ConfigMgr NAP:
The technologies required for NAP are built in to Windows Server 2008 and Windows Vista.
Deploying
NAP does not require additional licenses (check with your Microsoft
representative for current information on licensing).
The NAP agent is really a service running on the box and can be managed via group policy.
The agent for XP shipped as part of Service Pack 3 for XP in April of 2008.
NAP is not a security solution; it is a network health solution.
There
is no NAP agent for Windows Server 2003; Microsoft is not developing an
NAP agent for any platform older than Windows XP Service Pack 3.
NAP interoperates with Cisco’s Network Admission Control framework.
NAP interoperates with practically every switch/access point in the market and uses industry-standard protocols.
NAP is currently deployed to thousands of desktops inside and outside of Microsoft.
The NAP Statement of Health protocol has been accepted as a TNC/TCG standard.
NPS Overview in Windows Server 2008
Network
Policy Server is Microsoft’s replacement technology in Windows Server
2008 for Internet Authentication Service (IAS) in Windows Server 2003.
IAS only provided a subset of NPS’s capabilities. Both IAS and NPS
allow administrators to route traffic authentication against AD for remote access and enforcement of network access. Both technologies offer these capabilities:
VPN services
Dial-up services
802.11 protected access
Routing and Remote Access (RRAS)
Authentication through AD
Control of network access with policies (GPOs)
NPS
now lets administrators centrally configure and manage network policies
with the following three features: RADIUS (Remote Authentication
Dial-In User Service) server, RADIUS proxy, and NAP policy server. NPS
also allows centralized connection authentication, authorization, and
accounting for many types of network access, including wireless and
virtual private network (VPN) connections.
NPS’s full suite on functionality and capabilities includes the following:
Microsoft’s implementation of the RADIUS protocol.
Configurable as a RADIUS server.
Configurable as a RADIUS proxy that forwards connection requests to other RADIUS servers for processing.
A required component of NAP. When you deploy NAP, NPS functions as an NAP health policy server.
Configurable to perform all three functions (RADIUS server, RADIUS proxy, NAP health policy server) at the same time.
Compatible with user account databases in Active Directory Domain Services (AD DS).
NPS is available on all Windows Server 2008 editions except Microsoft’s Web Server 2008.
ConfigMgr NAP Policies
NAP
policies in ConfigMgr evaluate clients and verify if they have the
required updates. ConfigMgr then sends the NPS the SoH from the client
and a list of remediation servers. NPS then determines whether the
client will be granted full network access or restricted network
access, and whether the computer can be remediated if found to be out
of compliance. NPS supports the following policies for NAP clients:
NAP-capable clients that are compliant have full network access.
NAP-capable clients that are noncompliant have restricted network access until remediated.
NAP-capable clients that are noncompliant have full network access for a limited time and are immediately remediated.
NAP-ineligible clients have full network access.
NAP-ineligible clients have restricted network access but are not remediated.
All
error conditions, by default, result in computers having restricted
access (with remediation if supported by the client), but they can be
configured for full network access.
Caution: ConfigMgr NAP Remediation Requirement
If
health policies are not enforced in the network policy on the NPS, NAP
in Configuration Manager cannot remediate noncompliant computers.
Compliance in this case can be achieved through the defined
Configuration Manager Software Updates functionality. If health
policies are enforced in the network policy on the NPS, NAP in
Configuration Manager always attempts to remediate noncompliant
computers, even if the option to auto-remediate noncompliant computers
is not enabled in the network policy.
NAP
in ConfigMgr 2007 builds on the capabilities and automation routines
offered natively in NPS. The integration of NPS in ConfigMgr creates
some very sophisticated possibilities for administrators to secure
their network environment. The value of NAP increases exponentially as
the number of mobile systems in an environment increase.
ConfigMgr NAP Evaluation
ConfigMgr
NAP is a feature that allows administrators the ability to enforce
compliance of software updates, or restrict access, on client computers
to help protect the integrity of the network. NAP is managed via
policies that the clients download. Administrators define their
requirements for connectivity to the environment. The client checks its
configuration against that which is defined, and generates a client
Statement of Health. This SoH is sent to the SHV, a ConfigMgr role. The
SHV evaluates what is required if the client is out of compliance and
offers options defined by the administrator for remediation. The
remediation process may be user interactive or completely silent,
depending on the administrative desires for the specific deviation from
compliance. If the client does not have current NAP policies, the agent
will kick off a machine policy refresh, which includes the latest NAP
policies, and then reevaluate its health and send a more current SoH.
Caution: NAP SoH Time Validation
Although
NAP SoH time validation can be set as wide as every 7 days, the default
is every 26 hours, which could lead to poor user experience due to
clients being restricted from the network after long weekends or
holidays. Finding an acceptable threshold for your environment will
require a balance between user acceptance and security risk mitigation.
A good starting point is 4 or 5 days.
NAP’s
success hinges on software update management (SUM). If SUM is not
working correctly, clients can be accidently quarantined without the
capability of remediation. Do not NAP-enforce software updates without
approving and distributing those updates, because clients will
otherwise be unable to remediate. An exception to this is for those
highly critical patches, where the risk of infection is greater than
network access by the non-compliant user or system.
NAP Health State
ConfigMgr
clients generate an SoH when the NAP agent requests it from the
ConfigMgr client. The ConfigMgr client sends the SoH to the ConfigMgr
SHV for verification. The SHV then sends a Statement of Health Response
(SoHR) containing the client health state to the NPS. The NPS then
sends the client heath state back to the client as an SoHR. The SoH
always contains the following items:
All
NAP-capable clients generate an SoH with a compliant status, even when
the site is not NAP enabled. Once NAP is enabled on the site, clients
will evaluate their SoH against the NAP policies defined on the NPS.
Caution: Forcing Fresh Scans for NAP Evaluations
Perform
thorough testing when using the Force a fresh scan for each evaluation
option on the NAP agent within ConfigMgr. This feature will generate
excessively long authentication times and may lead to an unfavorable
boot-up/logon experience.
This is another
setting to use with caution, but it may be of value in situations where
a specific patch is required. Experiment with these enforcement
settings in a lab environment, so the end user experience is clearly
understood.
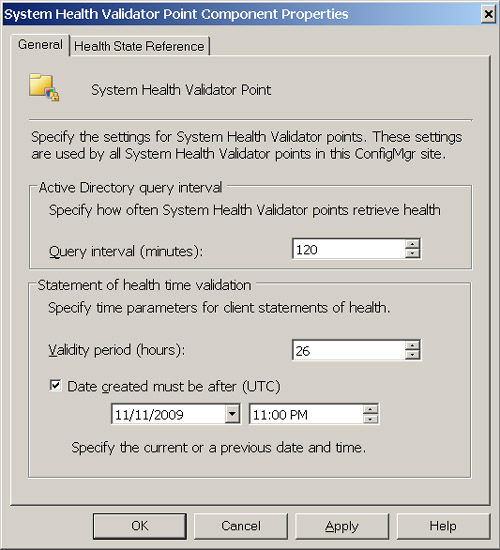
The SHV will
accept a cached statement of health from clients if it is within the
configured validity period and it does not conflict with the optional
Date setting specified on the General tab of System Health Validator
Point Component Properties. SoH messages may also contain failures when
a client cannot determine its own health status. Figure 1 illustrates the System Health Validator Point Component configuration within the ConfigMgr console.
When
clients generate an unknown response state failure, the NPS may not be
able to auto-remediate the client. ConfigMgr clients may return a
compliant SoH when they actually are noncompliant, and the SHV will
send a noncompliant SoH to the NPS. This can occur when the client has
not downloaded the new policies for compliance and is sending a cached
SoH. When a client’s SoH is sent to the SHV/NPS with a noncompliant
status and it is remediated, the client will generate another SoH and
re-send it, with a list of the client’s MP, DP, and SUP, to the SHV,
where it will be reevaluated and eventually granted access to the
network.