You can implement ConfigMgr in either mixed
mode or native mode. Native mode, the more secure of the two, requires
several certificates from the PKI (Public Key Infrastructure) for it to
handle operations such as IBCM. A PKI is an implementation of
certificate technology that allows binding a public key with some
identity via a Certificate Authority (CA). ConfigMgr leverages the PKI
to encrypt the transmission of data between the management point (MP)
and the client itself, and authentication of the client to the MP. For
ConfigMgr, these identities are machine accounts. The certificate is
bound via a registration process and then carried out by Active
Directory group policy objects (GPOs) and the CA auto-enrollment
process. You can also implement the certificates manually, depending on
your environment and deployment processes. ConfigMgr does not perform
any of the certificate deployment or management for the PKI or itself;
the PKI’s Registration Authority ensures the certificates are correctly
bound. Each account, identity, public key, binding, and validity
condition allow the CA to generate and issue certificates that cannot
be duplicated.
Note: ConfigMgr PKI Requirements
ConfigMgr
2007 can only leverage template-based certificates issued by an
enterprise Certificate Authority running on the Enterprise edition or
Datacenter edition of Windows Server 2003 or Windows Server 2008.
Running a PKI on the Standard edition of Windows Server 2003 or 2008
does not give administrators the ability to modify the templates per
ConfigMgr’s requirements.
1. Cryptography Basics
Cryptography
is the practice of hiding information, commonly used in security
scenarios such as ATM cards and passwords. Two cryptographic functions
are supported:
Symmetrical encryption
Asymmetrical encryption
Encryption is the process of transforming information (referred to as plain text) using an algorithm (a cipher) to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information (referred to as cipher text in cryptography). In many contexts, the word encryption
also implicitly refers to the reverse process, decryption (such that
“encryption software” will also perform decryption), that is, to make
the encrypted information readable again by making it unencrypted.
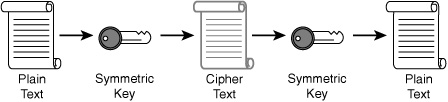
Symmetrical
encryption uses a single key for encryption, which both the sender and
receiver will leverage to decrypt the transmissions. When data is
encrypted with a symmetric algorithm, the sender generates a random
symmetric key. The algorithm and the application determine the
bit-length of the key. Figure 1 illustrates the symmetrical encryption process.
Asymmetric encryption uses a key pair. The keys that make up the key pair are mathematically related and referred to as the public and private
keys. Public keys are distributed freely. You can publish them to
Active Directory (AD) and install them via auto-enrollment. The use of this key
pair ensures that only the recipient has access to the necessary
private key to decrypt the data. Figure 2 illustrates the asymmetrical encryption process.
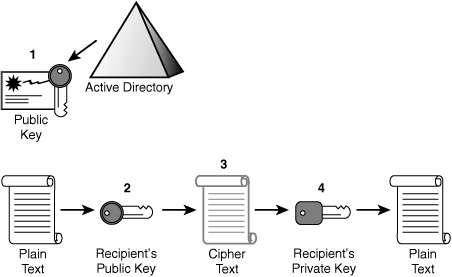
The following points define the process illustrated in Figure 2:
1. | The sender obtains the recipient’s public key.
|
2. | Data
is passed an asymmetrical encryption algorithm. It is encrypted with
the recipient’s public key, producing encrypted cipher text.
|
3. | Cipher text is sent to the recipient, who already has the private key.
|
4. | The recipient decrypts the cipher text with his or her private key back into the original format.
|
Note: Using Symmetric and Asymmetric Encryption
Applications
will generally use both encryption algorithms to encrypt data by first
encrypting the data with a symmetric algorithm and then encrypting the
symmetric encryption key using an asymmetric algorithm.
Two inputs are required when encrypting data:
The algorithm defines how to convert the data to the cipher text, and the key is used to input the data into the algorithm. Figure 3 illustrates the asymmetrical signing process.
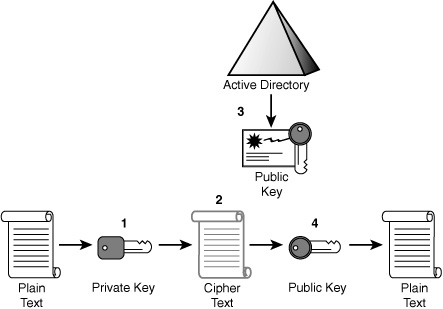
The following steps demonstrate how in Figure 3 you can validate the sender’s identity and that the data was not altered:
1. | The data passes though an asymmetrical encryption algorithm, using the private key as the encryption key.
|
2. | Cipher text is sent to the recipient.
|
3. | The recipient obtains the sender’s public key.
|
4. | The recipient decrypts cipher text with the sender’s public key back to original format.
|
This
encryption process protects the data, or payload, from being
intercepted and read, viewed, or altered. If it were intercepted, the
decryption process would fail, thus letting the recipient know there
was a breach.
Digital signing is used to
prove the source and integrity of the data. Using a hash algorithm,
digitally signed data can be trusted to be the original content. Hash
algorithms such as MD5 (Message Digest 5) and SHA1 (Secure Hash
Algorithm 1) apply a mathematical formula to an object, resulting in
output known as a hash value, message digest, or just digest. Hashes cannot be reversed, making them very useful in verifying data integrity.