AD was first introduced with the release of
Windows 2000 Server. Most of the core functionalities have remained the
same through Windows Server 2003, Windows Server 2008, and now Windows
Server 2008 R2. However, with each release, Microsoft has made some
performance improvements and added new features. In this section, we
will take a look at some of the new AD features in Windows Server 2008
R2.
1. Active Directory Recycle Bin
AD now includes an undelete option known as the
Recycle Bin. The AD Recycle Bin acts a lot like the Windows recycle bin
we are all very familiar with. The AD Recycle Bin stores objects for
180 days (by default) after they
are deleted from AD. This allows for easy full fidelity recovery of
deleted AD objects using PowerShell commands. The one main requirement
to use this feature is that your AD forest is in Windows Server 2008 R2
native mode, and all domain controllers (DCs) in the domain need to be
running Windows Server 2008 R2. Let us take a closer look at the AD
Recycle Bin.
|
Never test new features in production
Never try out new features in a production environment. You should always
test them in a lab environment and fully understand them before using
them in your production environment. Just because a new feature exists,
it does not mean it should or can be used in your specific deployment.
Do your homework and try it out in a lab first.
|
1. | First verify that the AD forest is in Windows Server 2008 R2 Native mode. You can verify this by opening Active Directory Domains and Trusts from Start | Administrative Tools.
|
2. | To verify the forest functional level, right-click the root node in the management console and choose the option Raise Forest Functional Level (see Figure 1).
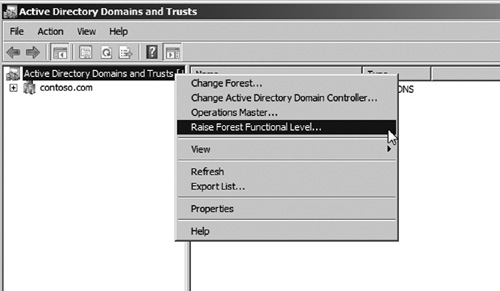
|
3. | The Raise Forest Functional Level window will pop up. The window will display the current forest functional level as seen in Figure 2.
If the forest is not in Windows Server 2008 R2 native mode, it will
need to be raised prior to attempting to use the AD Recycle Bin.
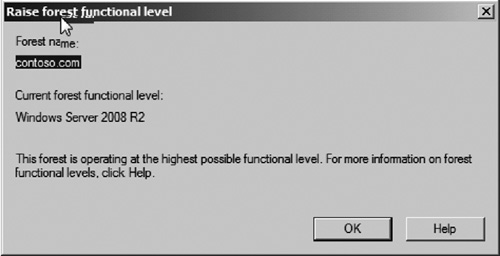
|
4. | After
verifying that your forest is in Windows Server 2008 R2 native mode,
you will need to enable the recycle bin. This is done by running a
PowerShell cmdlet.
|
5. | AD PowerShell can be accessed from Start | Administrative Tools | Active Directory Module for PowerShell.
|
6. | Enter the following command to enable the recycle bin (see Figure 3): enable-adoptionalfeature "Recycle Bin Feature" –Scope ForestorConfigurationSet –Target contoso.com
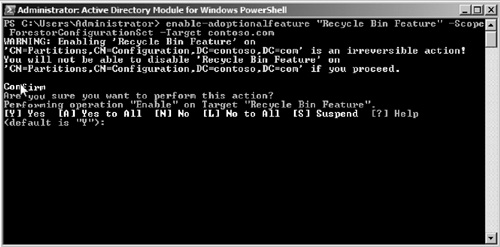
|
7. | When prompted, choose [Y] Yes to enable the recycle bin on the Target.
|
8. | Now
that the recycle bin is enabled, we will test the recycle bin by
deleting an organizational unit (OU) named My User OU. To do this, open
Active Directory Users and Computers (ADUC). Create a new OU named My User OU. When creating the OU, be sure to uncheck the box saying Protect Container from Accidental Deletion.
|
9. | After creating the OU, delete it by right-clicking on the My User OU and choosing Delete. Click Yes to verify you do indeed want to delete this object (see Figure 4).
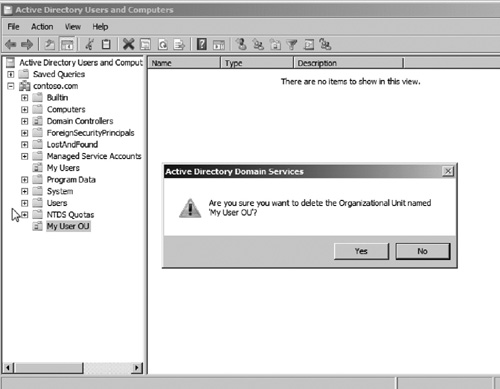
|
10. | Now that we have deleted the OU, let us restore it from the AD Recycle Bin. Return to PowerShell with AD cmdlets loaded.
|
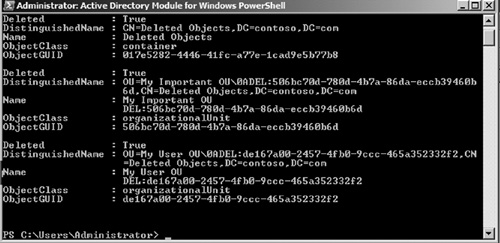
11. | At the PowerShell, promptly enter the command: Get–ADObject –SearchBase "CN=Deleted Objects,DC=test,DC=local" –ldapFilter "(objectClass=*)" –includeDeletedObjects.
|
12. | This will list the contents of the recycle bin. Notice the ObjectGUID on each of the objects (see Figure 5).
You will want to note the GUID of the object you want to restore. In
our example, we will restore the My User OU with an objectGUID of
de167a00–2457–4fb0–9ccc-465a3523332f2.
|
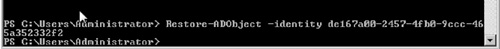
13. | To restore the object, enter the command Restore–ADObject –identity de167a00–2457–4fb0–9ccc–465a3523332f2 (see Figure 6).
|
14. | You can refresh your view of ADUC, and the My User OU will instantly reappear.
|
We used a simple example of how you can
quickly recover a deleted object. It is important to understand that
this tool could be used to easily restore
accidental deletion of not only simple OUs but also entire OU
structures that could contain thousands of users, groups, or computers.