The way you protect user data in Vista has
changed from previous versions. In past versions of Windows,
administrators protected user data through two key features:
Home Directory:
This feature was a network share that would be provided to end users to
store information on the network. Information in this share was
protected through server backups
Roaming Profile:
This feature captures an entire user's profile and stores it on the
network. When users log onto a PC, the entire profile is downloaded
from the network. When users log off, the updated profile is copied
back to the network share. Roaming profiles are monolithic; that is,
the entire profile is copied back and forth. If a user has a 10MB
document on the desktop, the document will be moved back and forth.
Because of this, users with large profiles can experience unexpected
delays at log on and log off.
Although
both technologies are still available with Windows Vista, they are
considered legacy technologies because of their monolithic nature. With
the introduction of Windows XP and Windows Server 2003, Microsoft
introduced a new concept for profile protection: folder redirection.
Folder
redirection is controlled through Group Policy and serves to
automatically redirect key user folders to network shares. The process
is completely transparent to users. When folders are redirected, they
automatically benefit from offline caching and are therefore available
to users even when the network connection is no longer available. When
the network connection returns, the contents of the local cache is
automatically re-synchronized with the contents from the network share.
In addition, folders can be discretely selected within Group Policy.
This
makes folder redirection not only ideal for networked users, but also
for mobile users because they have the ability to take data with them.
When they reconnect to the network, their work is protected through
synchronization, and, because the data resides on the network, it is
backed up on a regular basis.
In Windows
XP, folder redirection provided protection for four key folders. In
Vista, this has been expanded to ten folders, which makes folder
redirection more granular. By enabling folder redirection in Group
Policy, you enable the system to create a centralized folder based on
the user's name — much like the old home directory process. This folder
is secured so that only the user will have access to it by default.
Subfolders are created within the main folder for each of the folders
you've elected to redirect. In addition, the folder on the user's
desktop is automatically redirected to the newly created networked
folders.
Synchronization of the data
between the local PC and the network share begins as soon as the
process is activated. If the user folder already exists, the user's
data is moved from the PC to the network share. The data is cached back
onto the PC. That is when the synchronization process begins. When a
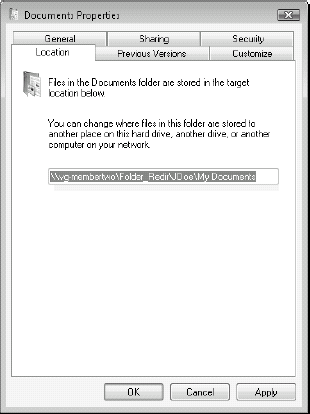
folder is redirected, its location changes to the network share, as
shown in Figure 1.
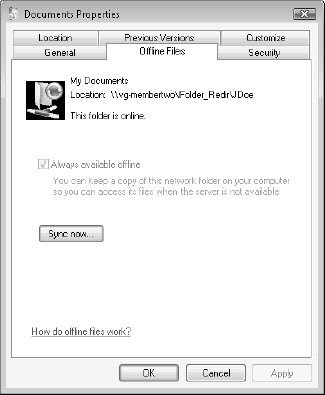
From then on, the local cache is managed through the Vista Sync Center.
Users can choose the properties of a folder to ensure that it is
synchronized and up to date, as shown in Figure 2.
1. Completing a data protection strategy
Folder
redirection provides extensive protection for ten key user folders, but
unfortunately, this does not provide complete profile protection
because it leaves key profile content unprotected. For example, folder
redirection cannot protect the NTUser.DAT file that holds
in-memory profile content because it is always locked when in use and
therefore cannot be synchronized. In addition, the data located in the
Local and LocalLow folders is not protected by folder redirection.
Therefore, you must supplement folder redirection with additional
profile protection.
The
additional profile protection is done by combining folder redirection
with roaming profiles. This can give you the best of both worlds:
You
rely on folder redirection to protect and synchronize data folders, and
you rely on the roaming profile to protect the rest of the user content.
Roaming profiles are smaller because you exclude the content that is protected by folder redirection from the roaming profile.
Data is available in real time because of folder redirection.
Logon
and logoff times are faster because the content protected by roaming
profiles is significantly less than through traditional roaming
profiles.
You protect only the content you need to protect.
But,
this means a change in the way you provide user data protection. When
organizations relied on home directories, they provided a minimal
amount of space on central servers for users to store information. Now,
with the combination of folder redirection and roaming profiles, you
will need to allocate more storage space to each user. Ideally, 2GB of
space per user would be adequate. If you are using Windows Server 2003
R2 or Windows Server 2008, then you can manage this space allocation
through their quota management features and therefore make sure users
do not exceed it.
You should implement
this protection mechanism whether or not your users roam from PC to PC.
Storage space is less expensive today than it has ever been before, so
allocating appropriate space on a per-user level is easy. Storing
profile information in a central location allows you to back it up as
well as make it available to users from any computer. In addition,
should anything untoward happen to the user's PC, you don't have to
worry about trying to protect key data because it is not stored
locally. When problems arise on PCs, you know you can flash their OS
installation at any time because you no longer have to worry about user
data.
NOTE
You
can also rely on the combination of folder redirection with roaming
profiles to migrate user data from Windows XP to Windows Vista. That's
because both technologies work in each version of the Windows client
OS. When users move from an XP computer to a Vista computer, the data
is automatically transferred from one format to the other. Vista
profiles are considered version 2 profiles and because of this, new
profile folders with a .V2 extension will be created on the server.