Windows Vista includes many new and improved security
technologies. While understanding security technologies often requires
more detailed knowledge, the security scenarios that these technologies
serve are practical and straightforward. The sections that follow
describe how Windows Vista security features work together to improve
the security of three major, common concerns: wireless networks, spyware
and other kinds of malware, and network worms.
Wireless Networks
Wireless
networks have improved user productivity by allowing people to connect
to the Internet and to their internal networks from almost
anywhere—meeting rooms, airports, hotels, coffee shops, and thousands of
other wireless hotspots. However, public wireless networks are almost
never encrypted, and even private wireless networks might fail to meet
your organization’s security requirements. Note that a wired
public Internet connection carries the same risk. Public connections of
any kind must be clear-text at Layer 2 because you don’t have the
opportunity to exchange security keys. For this reason, it’s imperative
that you use a virtual private network (VPN) to encrypt your data when
connecting to your internal network over a public network.
Wireless networking was
built into Windows XP, and it is also built into Windows Vista.
However, Windows Vista provides significant improvements to the
manageability, and thus the security, of wireless networking. With
Windows Vista, you can configure wireless security settings for mobile
clients in your organization using Active Directory Group Policy or
automated scripts. You can also configure Windows Firewall to block all
incoming requests from public wireless networks (the default), while
allowing specific incoming requests when connected to your internal
network.
Windows Vista also makes connecting to private wireless networks more secure. Wireless Single Sign-On
can connect to a wireless network before the user authenticates to the
Active Directory domain. Windows Vista also supports the latest wireless
security, including Wi-Fi Protected Access 2 (WPA2).
Help Desk Calls Related to Malware
Security
threats have constantly changed to adapt to each new generation of
operating system. In the past several years, the prevalence of malware
(a broad term that encompasses viruses, worms, Trojans, and rootkits,
as well as spyware and other potentially unwanted software) has soared.
Viruses, worms, and Trojans can spread from computer to computer by exploiting software vulnerabilities or tricking users with social engineering
techniques. Spyware and potentially unwanted software spread via these
techniques and also by legitimate installations initiated by users.
Users will install an application, unaware of the undesired
functionality of the program or of a program the application comes
bundled with.
Because
of the challenges in identifying malware, it might be impossible to
eliminate the threat completely. However, Windows Vista has many new
security features to protect computers from malware. Most significantly,
User Account Control (UAC) limits the ability of malware to install by
enabling IT professionals to deploy users as Standard users, rather than
Administrators. This helps prevent users from making potentially
dangerous changes to their computers without limiting their ability to
control other aspects on their computers, such as time zone or power
settings. For anyone who does log on as an administrator, UAC makes it
more difficult for malware to have a computer-wide impact.
Similarly, the
Protected Mode of Internet Explorer runs Internet Explorer without the
necessary privileges to install software (or even write files outside of
the Temporary Internet Files directory), thereby reducing the risk that
Internet Explorer can be abused to install malware without the user’s
consent. Windows Defender detects many types of spyware and other
potentially unwanted software, and prompts the user before applications
can make potentially malicious changes. Windows Service Hardening limits
the damage attackers can do in the event that they are able to
successfully compromise a service, thereby reducing the risk of
attackers making permanent changes to the operating system or attacking
other computers on the network. While Windows Vista cannot eliminate
malware, these new technologies can significantly reduce
malware-associated costs.
Windows Vista is designed
to block many types of common malware installation techniques. The
sections that follow describe how Windows Vista protects against malware
that attempts to install without the user’s knowledge through bundling
and social engineering, browser exploits, and network worms.
Protecting Against Bundling and Social Engineering
Two of the most common
ways malware becomes installed on a computer are bundling and social
engineering. With bundling, malware is packaged with useful software.
Often the user is not aware of the negative aspects of the bundled
software. With social engineering, the user is tricked into installing
the software. Typically, the user receives a misleading e-mail
containing instructions to open an attachment or visit a website.
Windows
Vista offers significantly improved protection against both bundling and
social engineering. With the default settings of Windows Vista, malware
that attempts to install via bundling or social engineering must
circumvent two levels of protection: UAC and Windows Defender.
UAC either prompts the
user to confirm the installation of the software (if the user is logged
on with an administrative account) or prompts the user for
administrative credentials (if the user is logged on with a Standard
account). This feature makes users aware that a process is trying to
make significant changes and allows them to stop the process. Standard
users are required to contact an Administrator to continue the
installation.
Windows
Defender real-time protection blocks applications that are identified
as malicious. Windows Defender also detects and stops changes the
malware might attempt to make, such as configuring the malware to run
automatically upon a reboot. Windows Defender notifies the user that an
application has attempted to make a change and gives the user the
opportunity to block or proceed with the installation.
Note
Windows Defender adds events to the System event log. Combined with event subscriptions
or a tool such as Microsoft Operations Manager (MOM), you can easily
aggregate and analyze Windows Defender events for your organization. |
These levels of protection are illustrated in Figure 1.
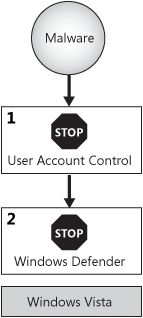
With Windows XP
and earlier versions of Windows, bundling and social engineering malware
installations were likely to succeed because none of these protections
was included with the operating system or service packs.
|
Defense-in-depth
is a proven technique of layered protection that reduces the exposure
of vulnerabilities. For example, you might design a network with three
layers of packet filtering: a packet-filtering router, a hardware
firewall, and software firewalls on each of the hosts (such as Internet
Connection Firewall). If an attacker manages to bypass one or two of the
layers of protection, the hosts are still protected.
The real benefit of
defense-in-depth is its ability to protect against human error. While a
single layer of defense is sufficient to protect you under normal
circumstances, an administrator who disables the defense during
troubleshooting, an accidental misconfiguration, or a newly discovered
vulnerability can disable that single layer of defense. Defense-in-depth
provides protection even when a single vulnerability exists.
While most new
Windows Vista security features are preventative countermeasures that
focus on directly mitigating risk by blocking vulnerabilities from being
exploited, your defense-in-depth strategy should also include detective
and reactive countermeasures. Auditing and third-party
intrusion-detection systems can help to analyze an attack after the
fact, enabling administrators to block future attacks and possibly
identify the attacker. Backups and a disaster recovery plan enable to
you react to an attack and limit the potential data lost.
|
Protecting Against Browser Exploit Malware Installations
Historically,
many malware installations have occurred because the user visited a
malicious website, and the website exploited a vulnerability in the web
browser to install the malware. In some cases, users received no warning
that software was being installed. In other cases, users were prompted
to confirm the installation, but the prompt might have been misleading
or incomplete.
Windows Vista provides four layers of protection against this type of malware installation:
Automatic
Updates, enabled by default, helps keep Internet Explorer and the rest
of the operating system up to date with security updates that can fix
many security vulnerabilities.
Internet
Explorer Protected Mode provides only extremely limited rights to
processes launched by Internet Explorer, even if the user is logged on
as an administrator. Any process launched from Internet Explorer has
access only to the temporary Internet files directory. Any file written
to that directory cannot be executed.
For
administrators, UAC prompts the user to confirm before computer-wide
configuration changes are made. For Standard users, the limited
privileges block most permanent per-computer changes unless the user can
provide administrative credentials.
Windows
Defender notifies the user if malware attempts to install itself as a
browser helper object, start itself automatically after a reboot, or
modify another monitored aspect of the operating system.
These levels of protection are illustrated in Figure 2.
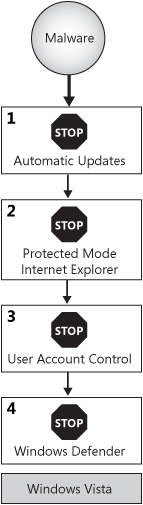
Protecting Against Network Worms
While
bundling, social engineering, and browser exploits all rely on the user
to initiate a connection to a site that hosts malware, worms can infect
a computer without any interaction from the user. Network worms spread
by sending network communications across a network to exploit a
vulnerability in remote computers and install the worm. Once installed,
the worm continues looking for new computers to infect.
If the worm attacks a Windows Vista computer, Windows Vista offers four levels of protection:
Windows
Firewall blocks all incoming traffic that has not been explicitly
permitted (plus a few exceptions for core networking functionality in
the domain and private profiles). This feature blocks the majority of
all current worm attacks.
If
the worm attacks a patched vulnerability in a Microsoft component,
Automatic Updates—which is enabled by default—might have already
addressed the security vulnerability.
If
the worm exploits a vulnerability in a service that uses Windows
Service Hardening and attempts to take an action that the service
profile does not allow (such as saving a file or adding the worm to the
startup group), Windows Vista will block the worm.
If
the worm exploits a vulnerability in a user application, limited
privileges enabled by UAC block system-wide configuration changes.
These levels of protection are illustrated in Figure 3.
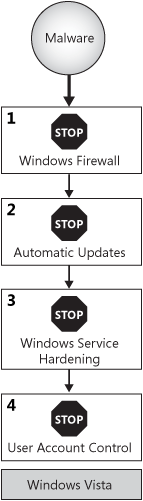
The original release
of Windows XP lacked all of these levels of protections. With Windows XP
Service Pack 2, Windows Firewall and Automatic Updates are enabled, but
the other levels of protection offered by Windows Vista are
unavailable.
Data Theft
As mobile computers,
network connectivity, and removable media have become more common, so
has data theft. Many businesses and government organizations store
extremely valuable data on their computers, and the cost of having the
data fall into the wrong hands could be devastating.
Today,
many organizations mitigate the risk of data theft by limiting access
to data. For example, applications might not allow confidential files to
be stored on mobile computers. Or, users simply might not be allowed to
remove computers from the office. While these limitations do
successfully reduce the risk, they also reduce employee productivity by
not allowing the staff to benefit from mobile computing.
Windows Vista
provides data protection technologies designed to meet stricter security
requirements while still allowing users to work with confidential data
in a variety of locations. Consider the following common data theft
scenarios, and how Windows Vista mitigates the risks of each.
Physical Theft of a Mobile Computer or a Hard Disk, or Recovering Data from a Recycled or Discarded Hard Disk
Operating systems
can only provide active protection for the data stored on your hard disk
while the operating system is running. In other words, file access
control lists (such as that provided by NTFS) cannot protect data if an
attacker can physically access a computer or hard disk. In recent years,
there have been many cases of stolen mobile computers whose
confidential data was extracted from the hard disk. Data is often
recovered from computers that are recycled (by assigning an existing
computer to a new user) or discarded (at the end of a computer’s life),
even if the hard disk had been formatted.
Windows Vista reduces the
risk of this type of data theft by allowing administrators to encrypt
files stored on the disk. As with Windows XP, Windows Vista supports Encrypting File System (EFS).
EFS enables administrators and users to selectively encrypt files or to
mark an entire folder to encrypt all files it contains. In addition to
the capabilities offered by Windows XP, Windows Vista enables you to
configure EFS using Group Policy settings so that you can centrally
protect an entire domain without requiring users to understand
encryption.
EFS cannot protect
Windows system files, however. Protecting Windows from offline attack
(booting from removable media to access the file system directly or
moving the hard disk to a different computer) helps ensure the integrity
of the operating system even if a computer is stolen. BitLocker Drive
Encryption, new to Windows Vista, provides encryption for the entire
system volume—thus protecting not only the operating system but also any
data stored on the same volume (drive letter). BitLocker can work
transparently with supported hardware, or it can require multifactor
authentication by requiring users to enter a password before allowing
the volume to be decrypted. Depending on your security requirements, you
can use BitLocker with existing computer hardware by storing the
decryption keys on removable media or even having users type in a
decryption key before Windows boots.
Copying Confidential Files to Removable Media
Organizations with
strict security requirements often limit access to confidential data to
computers on the local network, and then do not allow those computers to
be removed from the facility.
Historically, these organizations would remove floppy drives from the
computers to prevent users from saving confidential files. Recently,
however, there has been a huge increase in the types of removable media
available. Specifically, mobile phones, PDAs, portable audio players,
and USB drives often have several gigabytes of storage capacity. Because
they are small and extremely common, they might be overlooked even if a
facility has security staff available to search employees entering or
leaving a building.
Windows Vista enables you
to use Group Policy settings to limit the risk of removable media. Using
the Group Policy settings in Computer Configuration\Administrative
Templates\System\Device Installation\Device Installation Restrictions,
Administrators can:
Allow
installation of entire classes of devices (such as printers) using the
Allow Installation Of Devices Using Drivers That Match These Device
Setup Classes setting.
Disallow
all unsupported or unauthorized devices using the Prevent Installation
Of Devices That Match Any Of These Device IDs setting.
Disallow any kind of removable storage device using the Prevent Installation Of Removable Devices setting.
Override
these policies if necessary for troubleshooting or management purposes
using the Allow Administrators To Override Device Installation Policy
setting.
Accidentally Printing, Copying, or Forwarding Confidential Documents
Often, users need to
share confidential documents to collaborate efficiently. For example, a
user might e-mail a document to another user for review. However, once
the document is copied from your protected shared folder or intranet,
you lose control of the document. Users might accidentally copy,
forward, or print the document, where it can be found by a user who
shouldn’t have access.
There’s no perfect solution to protect electronic documents from copying. However, the Rights Management Services (RMS)
client, built into Windows Vista, enables Windows Vista computers to
open RMS-encrypted documents and enforce the restrictions applied to the
document. With an RMS infrastructure and an application that supports
RMS, such as Microsoft Office, you can:
Allow a user to view a document, but not save a copy of it, print it, or forward it.
Restrict users from copying and pasting text within a document.
Make it very difficult to open the document using a client that does not enforce RMS protection.
To
use RMS, you need an RMS infrastructure and supported applications in
addition to Windows Vista. However, Windows Vista is a key part of RMS.