Group Policy Defined
Many
technology terms can be confusing, especially when the terms are very
similar to each other. Examples include Group Policy, Group Policy
objects, policies, policy settings, and so on.
Group Policy
is a technology that is built into Windows 2000 and later operating
systems. Group Policy—broken down to the rawest form and definition—is
defined as a mechanism for centralizing configurations for computers and
user accounts.
Understand that Group Policy
objects are the objects that the Group Policy technology uses to
centralize the configurations. GPOs contain collections of policy
settings, which the GPOs are in turn linked to Active Directory nodes
(such as the domain, organizational units, or sites). The objects
contained within the nodes receive the settings contained within the
Group Policy Objects.
Policy settings
are used in many different forms and definitions. Many administrators
use policy settings to refer to any setting within a GPO. Others use the
term to refer to those special settings in the registry that users do
not have permission to modify.
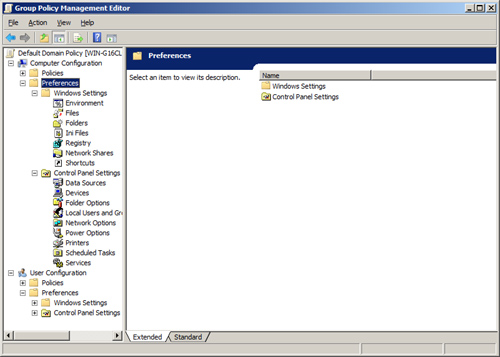
Preference settings is a term that is not used often, but it is important. It is used in conjunction with the preceding term, policy settings. Preferences
are registry settings that are not volatile. Preference settings
“tattoo” the registry with settings. There is an entirely new section in
a GPO within the Group Policy Management Editor that involves
preferences, as shown in Figure 1.
Structural Overview of a GPO
Most
administration of GPOs occurs with those that are stored in Active
Directory.
Active Directory–based
GPOs use a common format and structure. First, all GPOs are accessed and
administered in the same way. There are a few options here, but most
use the Group Policy Management Console (GPMC) and the Group Policy
Management Editor (GPME). For more information about the GPMC, where al aspects of using and working with
the GPMC are discussed. When you use the GPME, the GPO always has a
distinct structure, shown in Figure 2.
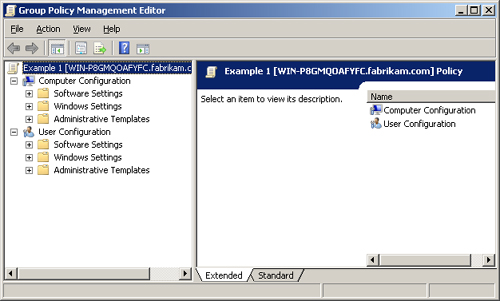
Notice
that there are two sections to the GPO: Computer Configuration and User
Configuration. These sections are very important to keep separate,
because they configure different object types. The Computer
Configuration section controls computer accounts. In a like manner, the
User Configuration section controls user accounts. Although a few
settings fall under
both sections, they do not cross the boundary of the two sections. If
you have a setting that falls under both sections, and you want them
both configured, you must configure both settings for users and
computers to receive the settings.
Keep in mind that
settings located under the Computer Configuration section apply to
computer objects, regardless of the user. In a like manner, settings
located under the User Configuration section apply to user objects,
regardless of the computer.
Computer Configuration
Breaking down the two
sections of the GPO reveals a very consistent structure that will help
you get around in the GPO in the future. First, if you expand the
Computer Configuration section, you will see the nodes shown in Figure 3.
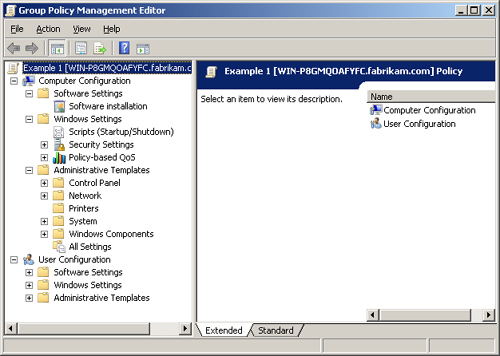
Within this section, you have the following three primary nodes:
Software Settings
Windows Settings
Administrative Templates
The Software Settings node is rather straightforward; it allows you to distribute software via .msi or .zap files.
The Windows Settings node goes a bit deeper, including many subnodes, as shown in Figure 4.
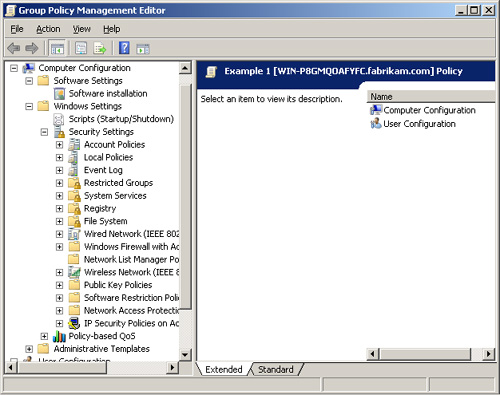
Within
this section of the GPO, you have plenty of options to choose from.
Account Policies control all aspects of user account passwords. Local
Policies offer extensive control over auditing and user rights, as well
as a variety of security settings. The security settings section alone
includes over 75 individual policy settings.
Other settings include
Windows Firewall, public key infrastructure (PKI), and IP security. In
the Software Restriction Policies node, you can establish black lists
and white lists of software that users can run. These policies can be
set for hash rules, path rules, or certificate rules, as well as network
zone rules.
The Administrative
Templates node is the final section of the Computer Configuration
section, and the largest. This section covers a wide variety of settings
for the computer, as shown in Figure 5.
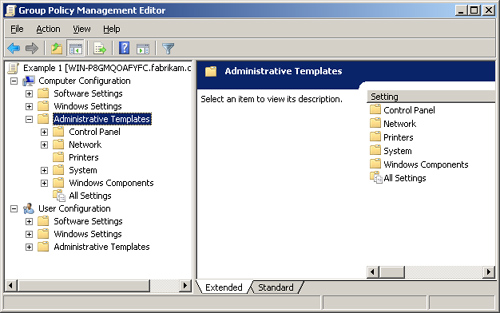
Although there are only
five major nodes within the Administrative Templates node, these nodes
control over 1,250 individual settings. As you can see, the top-level
nodes—including Control Panel, Network, Printers, System, and Windows
Components—cover a wide range of areas for a computer.
User Configuration
The
User Configuration section is similar to the Computer Configuration
section. The main difference is that the settings target user account
settings, not computer account settings. If you expand the User
Configuration section, as shown in Figure 6, you will see that there are three primary nodes:
Software Settings
Windows Settings
Administrative Templates
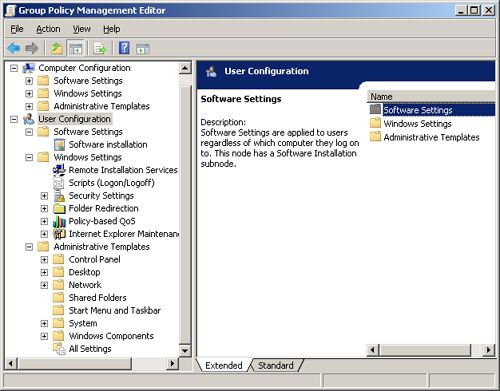
As in the
Computer Configuration section, you can create a policy in the User
Configuration section that distributes software to user accounts. Both
.msi and .zap files can be distributed using Group Policy.
The Windows Settings
node within the User Configuration section is distinctly different from
the Windows Settings node in the Computer Configuration section.
Immediately you see that there are policies related to Remote
Installation Services and Microsoft Internet Explorer maintenance.
Expanding the Security Settings node shows that only public key policies
are available, as shown in Figure 7.
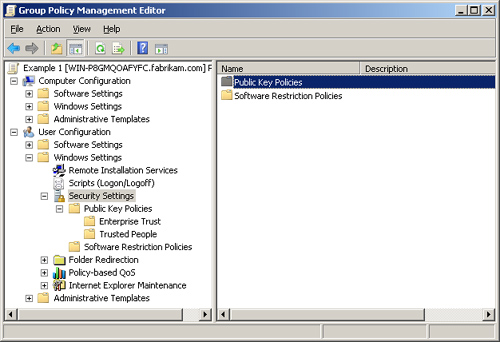
The final node is
Administrative Templates. With so few settings in the other two nodes,
it is no surprise that this node contains the majority of the settings
that fall under the User Configuration section of a GPO. After expanding
this node, you will see that it contains more top-level nodes than the
Computer Configuration section. Some of the subnodes are the same as in
the Computer Configuration section, but many are different, as you can
see in Figure 8.
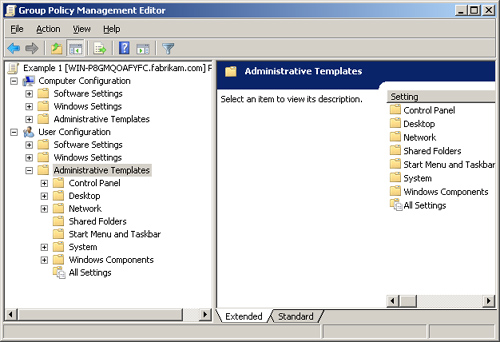
The
settings in the Administrative Templates node are intended for
controlling the user profile. The user profile maintains and controls
the user desktop and overall “look and feel” of the desktop environment.
Therefore, it is not surprising that this node contains nodes called
Shared Folders and Start Menu and Taskbar.
Although
some of the nodes exist within both the User Configuration and Computer
Configuration sections, the settings could not be more different. This
is because each section controls a different portion of the registry.
The Administrative Templates node and subnodes in the User Configuration
section contain over 1,200 policy settings—almost as many as in the
Computer Configuration section.