Providing secure remote
connectivity involves designing access through a perimeter network.
Therefore, design a secure perimeter network and decide which services
will reside within it first. Services to consider deploying within the
perimeter network will most likely include various RADIUS components,
VPN servers, publicly accessible application servers, wireless devices,
and supporting network infrastructure devices.
Due to the current security-minded environment,
your network undoubtedly contains a firewall along with one or more
supporting infrastructure devices such as switches and routers as well
as application servers such as Web and File Transfer Protocol (FTP)
servers that are publicly accessible. In addition, the network might
also have a RADIUS service to authenticate virtual private network (VPN)
connections or partner access to existing extranets, or possibly to
provide secure authentication for a preexisting wireless infrastructure.
These network devices and application servers will comprise the current
perimeter network that you inherit or are currently administering.
As the enterprise administrator, you are responsible for upgrading the current environment to provide support for:
This lesson provides the background to build a remote access solution and help lay the groundwork for designing a NAP solution.
|
After this lesson, you will be able to:
Understand the technical requirements when designing perimeter networks. Understand which services to provide in a perimeter network. Determine appropriate firewall services to provide for various types of perimeter networks. Design VPN solutions. Design a RADIUS solution for a small enterprise. Design a RADIUS solution to support branch offices within the same forest. Design a RADIUS solution to support a multi-forest environment.
Estimated lesson time: 45 minutes
|
1. Designing the Perimeter Network
Most
perimeter network designs involve one or two firewall devices to
protect the edge network. Traffic from the outside passes through one or
more inspection points before it is allowed into the perimeter network
to access services deployed there or into the secure environment.
Typical designs involve a single perimeter device with two or more
network interfaces or two inspection points with two security devices,
one inspecting traffic into the perimeter network from an untrusted
external environment and another inspecting traffic as it enters the
secure environment from the perimeter network.
As the enterprise administrator, you must assess
the type of traffic you allow into your perimeter network and what
traffic is permitted into the secure network. You need to determine how
and at what layer you inspect this traffic to fulfill your security
requirements successfully. You must assess the services to be deployed
in the perimeter network for public accessibility as well as for a
secure remote access solution.
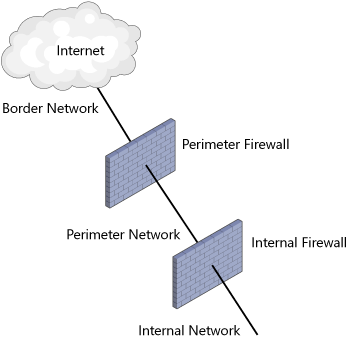
Types of Perimeter Network Architectures
There are many types of perimeter network
layouts. The design guides here provide descriptions for the basic
security feature sets included in most designs. Network architectures
will generally include three distinct regions or zones:
Border network
Perimeter network
Internal network
The border network provides the direct
connection to the external environment, which usually is a connection to
an ISP, that is often through a router. The border router can offer
some protective features such as access lists to manage specific
unwanted traffic from certain Internet Control Message Protocol (ICMP)
types such as echo requests associated with pinging. A perimeter
firewall along with associated security devices and services provides
the bulk of protection for the border network. Other than a switch used
to provide connectivity to the perimeter security services, there are
usually no other network application services of significance within
this zone.
The perimeter network is a semi-protected area
secured by a perimeter firewall and, possibly, an internal firewall.
Services located in this area include Web servers for public access that
connect to internal SQL servers along with many other application
servers. Most of the discussion in this lesson focuses on other services
located within this area.
The internal network is the location of the
secure environment. It houses the corporate user and server environment.
Some security designs include another firewall service separating the
internal user network from the server farms.
Figure 1 displays the typical architecture of the three-zone network environment, using two firewall services.
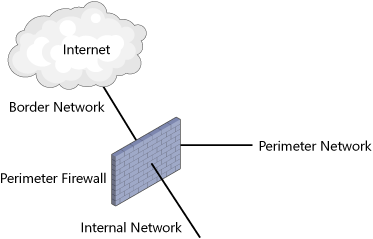
If the perimeter firewall is composed of three
or more network interfaces, an internal firewall is more of a logical
association with the same physical device providing the services for the
perimeter firewall than of a physical association with its network
interfaces. Figure 2
displays an alternative architecture of the network environment
employing three or more zones, using a single physical firewall service
dividing up separate logical security domains.
These
logical designs display a basis for targeting services and security
features when designing the perimeter network. As the enterprise
administrator, you are responsible for the security of the services that
are deployed in the perimeter network. Consider questions such as:
Which services should be deployed in the perimeter network to provide secure VPN connections?
Which supporting services are necessary to provide secure VPN connections?
Do internal users require a secured wireless connection?
Should the access points for wireless users be deployed as part of the perimeter network design?
If
RADIUS is to be used to centralize management of authentication for
remote access and wireless users, which RADIUS components, if any,
should be deployed in the perimeter network?
Securing the Perimeter Network
What is not shown in either design is the type
of security services offered by the firewall devices at the perimeter or
the internal location in the two firewall device designs. Knowing the
types of security devices used to secure access into the perimeter
network as well as into the internal environment offers you, the
enterprise administrator, a better idea of how services deployed in the
perimeter network can be protected. Different types of security devices
provide varying levels of security. This lesson focuses only on
enterprise-class devices. These devices typically provide one or more of
the following:
NAT uses private IP addresses that have
significant meaning when used within your organization. When traffic is
sent out to the Internet, these addresses require translation to an
acceptable public IP address. NAT was originally devised to overcome the
eventual shortage of public IP addresses. One of the benefits of using
NAT in your firewall design is that your internal addressing structure
is hidden from outside attackers—not a major source of security but a
significant fact. A possible detriment when using NAT is that certain
services, when run through it, have problems and require services such
as NAT editors for Point-to-Point Tunneling Protocol (PPTP) tunnels or
NAT Traversal (NAT-T) for IPsec tunnels and Layer 2 Tunneling Protocol
(L2TP) tunnels.
Stateful
inspection firewalls provide an accounting of all traffic that
originated on an interface in a state table. When the connection traffic
is returned, the state table determines whether the traffic originated
on that interface.
Circuit-level firewalls provide a more in-depth
inspection of traffic than does a stateful firewall. Circuit-level
firewalls provide session maintenance and enable the use of protocols
that require secondary connections such as FTP. Circuit-level firewalls
are usually the way stateful inspection services are carried out in
today’s retail firewalls.
Proxy servers are intermediaries that provide
security by requesting a service on behalf of a client; the client is
not directly connected to the service. The proxy service can inspect all
headers involved in the transaction, providing an extra layer of
protection. Frequently requested content can be cached and reused to
reduce bandwidth. Proxy servers can also provide authenticated requests,
NAT, and authentication request forwarding.
The ultimate in protection is an
application-layer firewall. Not only are all the incoming and outgoing
packet headers inspected and state tables maintained, but the data
streams can be inspected to provide security against attacks hidden in
the data payloads of ordinary Web service packets such as HTTP, other
Web-related request and data packets, and many other
application-specific request and response packets.
Planning for ISA Server
Protecting the perimeter network has been a
primary focus of Microsoft Internet Security and Acceleration (ISA)
Server. ISA Server 2006 is the current version and provides an
integrated edge security gateway for remote access, branch office
connectivity, and Internet access protection. ISA Server figures
prominently in any Microsoft solution because it integrates well with
Microsoft remote access services as well as provides secure tunneling
for site-to-site VPNs.
Note: Forefront Edge Security and Access
ISA Server 2006 is now part of the new
Microsoft Forefront Edge Security and Access product line. The Microsoft
Forefront line of products provides a comprehensive set of security
products from the edge of the network starting with Internet Security
and Acceleration (ISA) Server all the way to the desktop, providing
firewall services, protection from malware and spyware, network edge
security services, and much more.
A
common use of ISA Server in the perimeter network is in a back-to-back
design. The perimeter network is protected by ISA Server operating as a
firewall against the outside while providing filtering and reverse
proxying of services offered in the perimeter network. A second server
running ISA Server stationed between the perimeter network and the
internal network acts as an application-layer firewall and proxy server,
inspecting and securing all requests as they move inbound to the
internal network. The servers running ISA Server at the perimeter
firewall or at the internal edge can be deployed in a variety of
fashions to provide high availability and load balancing.
Figure 3 displays some of the roles that ISA Server can play when deployed in the perimeter network.

ISA Server 2004 and ISA Server 2006 support
Network Access Quarantine Control as a complementary service to
Microsoft Windows Server 2003. ISA Server 2004 or ISA Server 2006, when
installed on Windows Server 2003 SP1 or later, can use Quarantine
Control, which is provided by the Routing and Remote Access service of
Windows Server 2003 and is limited to providing access control to VPN
and remote access clients only. The service requires custom connection
profiles on the clients, along with server-side scripts to check for
compliance by remote access clients. The Quarantine Control service does
not at this time have any components that allow for integration with
the newer NAP service and Network Policy Server (NPS) services in
Windows Server 2008 other than NPS providing RADIUS services to VPN
clients using ISA Server as the VPN server.
More Info: ISA Server help
A site often helpful with ideas that involve ISA Server is http://www.isaserver.org.
This site is well maintained and well organized and offers a wealth of
ideas about design, add-ons, and configuration in ISA Server.
Note: ISA Server 2006 and Windows Server 2008
ISA Server 2006, at the time of this writing,
is not available for installation on Windows Server 2008 and is
available as a 32-bit application server only. Plans for the next
version of ISA Server and the Forefront Security products are tailored
for Windows Server 2008 and will be available for 64-bit platforms.
Third-Party Firewall Products
With the security field growing at an
increasing pace, third-party firewall products are plentiful. Many of
these products fit a paradigm similar to ISA Server. Many of the major
firewall product vendors have also included multiple feature sets in
their firewall product offerings. This makes it even more attractive to
pair a firewall product from one of these top-selling vendors with ISA
Server. A common scenario is to use a firewall appliance for the
perimeter firewall and an ISA Server cluster for the internal firewall.
Many of these third-party products provide an integrated assortment of
security services such as:
Stateful firewall services
Intrusion prevention services
Anti-malware services
Application-layer firewall services
At a minimum, the
firewall appliance should provide circuit-level services along with an
inline intrusion prevention service module to ensure inspection at the
application layer for inbound requests from the border network. ISA
Server or an ISA Server cluster installed as the internal firewall can
provide proxy, packet filtering, circuit-level firewall services, and
application-layer inspection of packets originating from either the
border network or the perimeter network for access to internal hosts or
responses returned to internal clients.