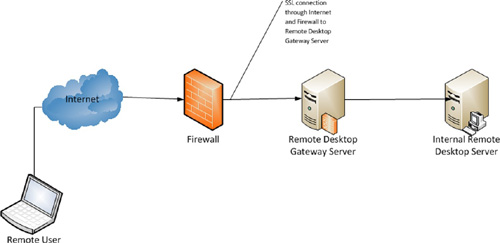
5. Installing and configuring Remote Desktop Gateway
The Remote Desktop Gateway provides the ability to
securely connect to Remote Desktop applications from outside your
corporate firewall without the need for a VPN connection. A Remote
Desktop Gateway creates a SSL tunnel between the client computer and
the gateway server. The Remote Desktop Session is then created within
this tunnel. Figure 22 depicts a typical Remote Desktop Gateway deployment.
|
Remote Desktop Gateway firewall ports
The Remote Desktop Gateway will need port 443 opened
inbound on your Internet firewall to allow connections from outside.
Port 443 is the default port used for SSL services.
|
In the following exercise, we will go through the
process of installing and configuring a Remote Desktop Gateway. For
this exercise, we will be configuring a dedicated server for the Remote
Desktop Gateway services.
1. | Open Server Manager on the server you wish to set up as the Remote Desktop Gateway.
|
2. | Select the Roles node. Then click the Add Role link. The Add Roles wizard will launch. Click Next to continue.
|
3. | Select the Remote Desktop Services role. Then click Next.
|
4. | At the Introduction to Remote Desktop Services page, click Next.
|
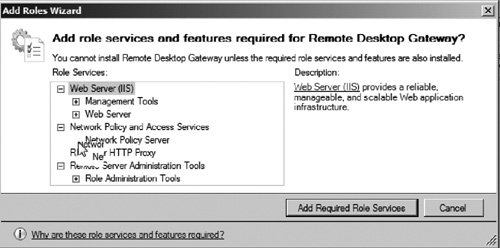
5. | Select the Remote Desktop Gateway on the role services selection page.
|
6. | When prompted, select the option Add Required Role Services (see Figure 23).
This will add other roles required to support the Remote Desktop
Gateway role service. This includes IIS components and the RPC/HTTP
proxy feature. Click Next to continue.
|
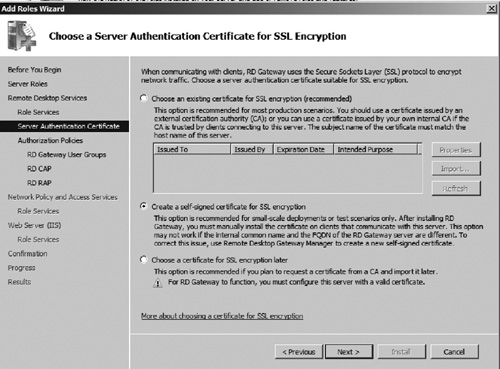
7. | You
now need to select a certificate that will be used to provide SSL
encryption for RDP connections. For a production deployment, this
certificate should be requested from an internal PKI or a public
certificate provider. For the purpose of this exercise, let us choose
the option to create a self-signed certificate (see Figure 24). Click Next to continue.
The next step of the wizard requires that you create a Remote Desktop
Connection Authorization Policy (RD CAP) and Remote Desktop Resource
Authorization Policy (RD RAP). The RD CAP determines which users are
allowed to connect through the Remote Desktop Gateway. The RD RAP
specifies which systems remote users can access when connecting through
the Remote Desktop Gateway.
|
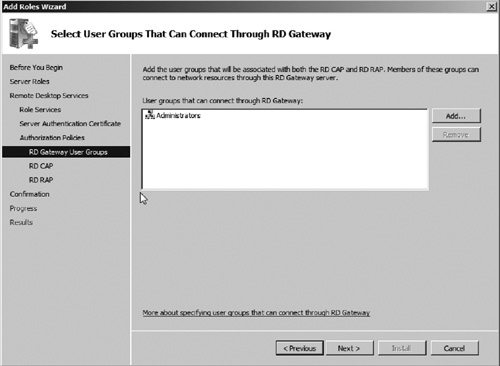
8. | Select the option to create authorization policies Now. Then click Next.
|
9. | Add the groups that will be associated with both the RD RAP and RD CAP policies (see Figure 25). In this exercise, let us use the Administrators group. After adding groups that you want to associate with authorization policies, click Next.
|
10. | Enter a name for the RD CAP policy. In this exercise, we will use the default TS_CAP_01.
|
11. | Select the authentication methods you want to support. For our example, we will use the Password method. After selecting the authentication policy, click Next
to continue. |
12. | Enter a name for the RD RAP policy (see Figure 26). We will use the default name TS_RAP_01.
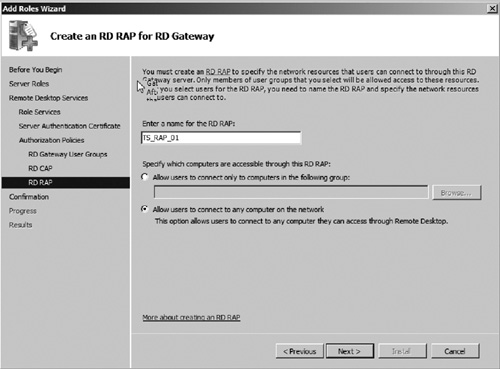
|
13. | You
can now limit which computers users can connect to through the gateway
by specifying a computer group within Active Directory. As best
practice, you should create an Active Directory group and place
computers that you want to allow gateway access to in that group. In
our exercise, we will select the option Allow users to connect to any computer on the network. After selecting what users can connect to, click Next to continue.
Limiting Which Computers Users Can Access Through Gateway
|
14. | On the Network Policy and Access Services page, click Next.
|
15. | Ensure that the Network Policy Server option is selected, and then click Next. This is an additional component that is required to support the Remote Desktop Gateway.
|
16. | Click Next on the IIS overview page.
|
17. | Accept the currently selected IIS role services by click Next. Again these role services are required to support the Remote Desktop Gateway.
|
18. | Verify your installation settings on the summary page. Then click Install.
|
19. | When the installation is complete, click Close.
|
This completes the basic setup of the Remote Desktop
Gateway. You can now configure a Remote Desktop client to connect to a
server using the gateway. You can configure the Remote Desktop client
to use the gateway by modifying the Connect From Anywhere settings on the advanced tab (see Figure 27).
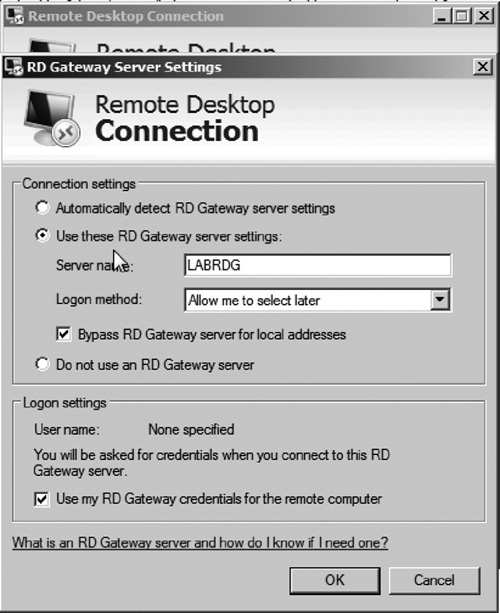
|
Remote Desktop Gateway self-signed certificate
If you use the self-signed certificate for the
Remote Desktop Gateway, you will need to manually add the certificate
to the trusted certificates store on any clients connecting through the
gateway. If a client does not trust the self-signed certificate, the
connection will fail.
|
The Remote Desktop Gateway server is a
great way to provide business partners or home users with access to
secure remote sessions without the need for VPN. The use of the Remote
Desktop Gateway also allows you to limit access to specific users and
then can limit which computers those users
can connect to. Additionally, the Remote Desktop Gateway can be
integrated with NAP to ensure that the connecting computers comply with
corporate security policies.