6. Managing UPN Suffixes
User principal name (UPN) suffixes are the part of a
user's name that appears after the @ symbol. So, for instance, the UPN
suffix of [email protected] would be stellacon.com. By default, the UPN suffix is determined by the name of the domain in which the user is created. In this example, the user wpanek was created in the domain stellacon.com,
so the two pieces of the UPN logically fit together. However, you might
find it useful to provide an alternative UPN suffix to consolidate the
UPNs forest-wide.
For instance, if you manage a forest that consists of stellacon.com and stellacon2.com, you might want all of your users to adopt the more generally applicable stellacon.com
UPN suffix. By adding additional UPN suffixes to the forest, you can
easily choose the appropriate suffix when it comes time to create new
users. Exercise 3 shows you how to add additional suffixes to a forest.
Open the Active Directory Domains And Trusts administrative tool by clicking Start => Administrative Tools =>Active Directory Domains And Trusts. Right-click Active Directory Domains And Trusts in the left side of the window and select Properties. On
the UPN Suffixes tab of the Active Directory Domains And Trusts
Properties dialog box, enter an alternate UPN suffix in the Alternate
UPN Suffixes field. Click the Add button to add the suffix to the list.
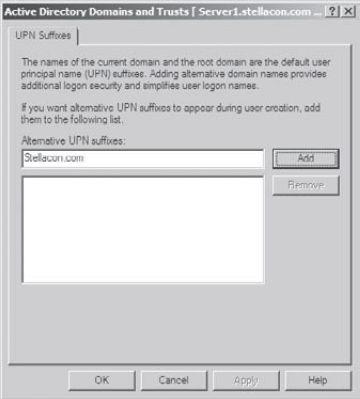
To remove a UPN suffix, select its name in the list and click the Remove button.
|
7. Managing Global Catalog Servers
One of the best features of a distributed directory
service like Active Directory is that you can store different pieces of
information in different places within an organization. For example, a
domain in Japan might store a list of users who operate within a
company's Asian operations business unit, while one in New York would
contain a list of users who operate within its North American
operations business unit. This architecture allows systems
administrators to place the most frequently accessed information on
domain controllers in different domains, thereby reducing disk space
requirements and replication traffic.
However, you may encounter a problem when you deal
with information that is segmented into multiple domains. The issue
involves querying information stored within Active Directory. What
would happen, for example, if a user wanted a list of all of the
printers available in all domains within the Active Directory forest?
In this case, the search would normally require information from at
least one domain controller in each of the domains within the
environment. Some of these domain controllers may be located across
slow WAN links or may have unreliable connections. The end result would
include an extremely long wait while retrieving the results of the
query, that is, if any results came up without timing out.
Fortunately, Active Directory has a mechanism that
speeds up such searches. You can configure any number of domain
controllers to host a copy of the GC. The GC contains all of the schema
information and a subset of the attributes for all domains within the
Active Directory environment. Although a default set of information is
normally included with the GC, systems administrators can choose to add
additional information to this data store if it is needed. To help
reduce replication traffic and to keep the GC's database small, only a
limited subset of each object's attributes are replicated. This is
called the partial attribute set (PAS). You can change the PAS by
modifying the schema and marking attributes for replication to the GC.
Servers that contain a copy of the GC are known as
GC servers. Now, whenever a user executes a query that requires
information from multiple domains, they need only contact the nearest
GC server for this information. Similarly, when users must authenticate
across domains, they do not have to wait for a response from a domain
controller that may be located across the world. The end result is that
the overall performance of Active Directory queries increases.
Exercise 4
walks you through the steps you need to take to configure a domain
controller as a GC server. Generally, GC servers are only useful in
environments that use multiple Active Directory domains.
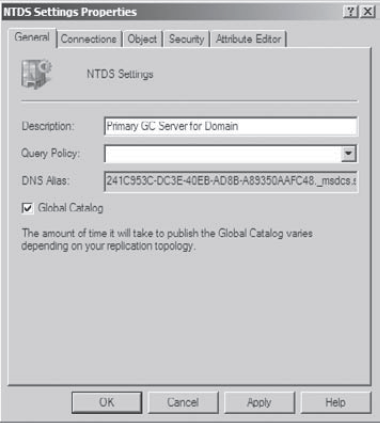
Open the Active Directory Sites And Services administrative tool by clicking Start => Administrative Tools => Active Directory Sites And Services. Find the name of the local domain controller within the list of objects (typically under Default First Site Name => Servers), and expand this object. Right-click NTDS Settings and select Properties. In the NTDS Settings Properties dialog box, type Primary GC Server for Domain
in the Description field. Note that there is a checkbox that determines
whether this computer contains a copy of the Global Catalog. If the box
is checked, then this domain controller contains a subset of
information from all other domains within the Active Directory
environment. Select the Global Catalog checkbox, and then click OK to
continue.
When you are finished, close the Active Directory Sites And Services administrative tool.
|
8. Managing Universal Group Membership Caching
Many networks run into problems due to available
network bandwidth and server hardware limitations. For this reason, it
may not be wise to install a GC in smaller branch offices. Windows
Server 2008 can help these smaller sites by deploying domain
controllers that use universal group membership caching.
Once enabled, universal group membership caching
stores information locally once a user attempts to log on for the first
time. With the use of a GC, the domain controller retains the universal
group membership for that logged on user.
The next time that user attempts to log on, the
authenticating domain controller running Windows Server 2008 will
obtain the universal group membership information from its local cache
without the need to contact a GC. The universal group membership
information is retained, by default, on the domain controller for 8
hours.
Some of the advantages of using universal group membership caching are as follows:
Faster logon times
Since the domain controller does not need to contact a global catalog, logon authentication is faster.
Reduced network bandwidth
The domain controller does not have to handle object replication for all the objects located in the forest.
Ability to use existing hardware.
There is no need to upgrade hardware to support a GC.
Exercise 5 shows you the steps that you need to take to configure universal group membership caching.
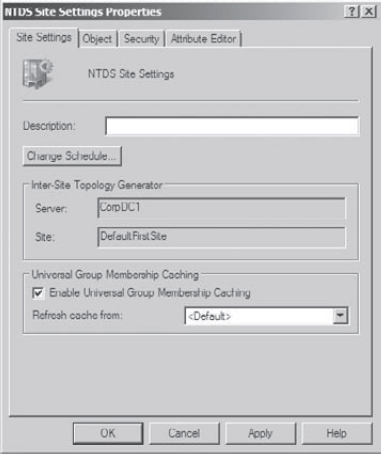
Open the Active Directory Sites And Services administrative tool by clicking Start => Administrative Tools => Active Directory Sites And Services.
Click Sites, then Click DefaultFirstSite. In the right pane, right-click NTDS Settings and choose Properties.
In
the NTDS Site Settings Properties dialog box, check the box labeled
Enable Universal Group Membership Caching and then click OK to continue.
When you are finished, close the Active Directory Sites And Services administrative tool.