Managing the Local GPOs
As stated earlier, only
users who have membership in the local Administrators group can manage
the local GPOs. This includes user from the local SAM or from Active
Directory. In either case, if User Account Control (UAC) is enabled, the
security dialog box from UAC will appear, forcing users with
administrative privileges to agree to the privileges that opening the
MMC snap-in requires.
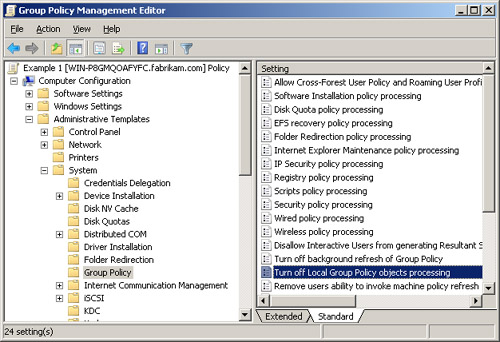
Another new feature is the
option to disable local GPOs. Through Active Directory–based GPOs, local
GPOs can be disabled, and thus excluded from the evaluation of overall
Resultant Set of Policy (RSoP). The policy that you would set is “Turn
off Local Group Policy objects processing.” This policy setting is
located under Computer Configuration\Administrative
Templates\System\Group Policy, as shown in Figure 4.
GPOs in Active Directory
Although
GPOs that are created in Active Directory can total into the hundreds
or even thousands, they all follow the same regimen. To go a step beyond
that, all GPOs in Active Directory are created, managed, and controlled
through a central console. It is this centralization that gives Group
Policy such power and control over the entire network of computers.
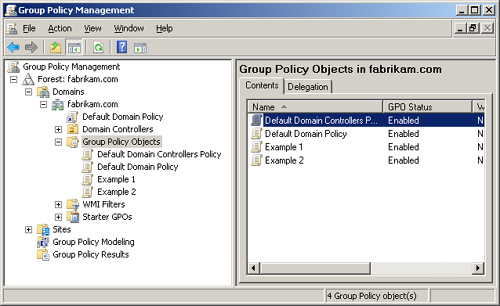
All GPOs that are stored
in Active Directory have the same structure. You must use the GPMC to
access one of these GPOs. Within the GPMC, you can expand the console to
see the list of GPOs that are in Active Directory. To access this list,
follow these steps:
1. | In the Run dialog box, type gpmc.msc.
|
2. | In the GPMC, expand the Forest and Domains nodes.
|
3. | In the Domains node, expand the Group Policy Objects node.
|
Note
To
run the GPMC, the computer must be a member of the domain. Also, if you
are running the GPMC with Windows Server 2008, the GPMC is not
installed by default and must be installed before it can be accessed.
|
You should see a list of GPOs, as shown in Figure 5.
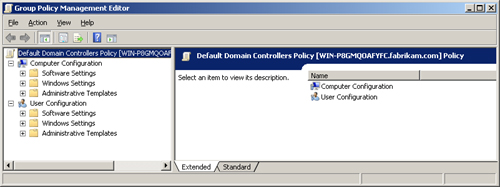
From this list, you can edit
any of the GPOs to see the policy settings that are already set, or you
can configure more settings. To edit a GPO, right-click it, and then
click Edit. This launches the Group Policy Management Editor with your
selected GPO active in the interface, as shown in Figure 6.
All of the GPOs that are
stored in Active Directory are available in this list through the GPMC.
Note, however, that if you have multiple Active Directory domains, you
will need to ensure that you are viewing the correct domain in the GPMC
to see your GPO. GPOs are stored in only one domain. There is no
mechanism to synchronize the settings between two GPOs in different
domains.
For example, suppose
that you wanted all domain controllers in all domains to have the same
set of user rights. These settings would be established in the Default
Domain Controllers Policy in each domain. If you made a configuration to
the User Rights in DomainA, the Default Domain Controllers Policy in
DomainB would not be updated. You would need to manually make this
change in the DomainB GPO if you wanted the domain controllers in that
domain to be updated.
After the creation and
configuration of GPOs in Active Directory, one step remains before the
GPO can perform any actions on computers or users on the network: you
must link the GPO to an Active Directory node. Without this final
linking step, the GPO is stored in Active Directory and on domain
controllers, but it does not perform any action.
GPOs in Active Directory can be linked to the following nodes:
It should be obvious
that if a GPO is linked to the domain it will affect all computer and
user accounts located in the domain by default. This is important to
remember, because linking GPOs to the domain node or site nodes can
potentially affect too many objects.
Important
Most
GPOs will be linked to organizational units. GPOs linked to the domain
or sites can affect too many types of computer or user accounts. Some
settings can be configured in a GPO linked to the domain, such as DNS
suffix, password policies, account lockout policies, screen saver
settings, and various Internet Explorer settings. Any settings that are
set in the GPOs linked to sites are typically “network”-related
settings. This might include firewall settings, proxy settings,
Distributed File System (DFS), and software installation points. |
The design and
implementation of your organizational units is critical to a successful
GPO deployment for two reasons: because the majority of GPOs in Active
Directory will be linked to Organizational Units, and because there is
only one organizational unit in a default installation of Active
Directory.
More Info
Windows Server 2008 Active Directory Resource Kit (Microsoft Press, 2008) covers this in great detail. |