3. Design Goals for Access Control
Before you start applying
NTFS permissions to resources, you should develop design goals for
access control as a part of your overall security strategy. Basic
security strategy suggests that you provide each user and group with the
minimum level of permissions needed for job functionality. Some of the
considerations when planning access control include the following:
Defining the resources that are included within your network—in this case, the files and folders residing on the file system
Defining
which resources will put your organization at risk, including defining
the resources and defining the risk of damage if the resource was
compromised
Developing security strategies that address possible threats and minimize security risks
Defining
groups that security can be applied to based on users within the group
membership who have common access requirements, and applying permissions
to groups as opposed to users
Applying additional security settings through Group Policy if your Windows 7 clients are part of an Active Directory network
Using
additional security features, such as Encrypted File System (EFS), to
provide additional levels of security or file auditing to track access
to critical files and folders
After you have decided what your design goals are, you can start applying your NTFS permissions.
3.1. Applying NTFS Permissions
NTFS permissions control
access to NTFS files and folders. This is based on the technology that
was originally developed for Windows NT. Ultimately, the person who owns
an object has complete control over the object. You configure access by
allowing or denying NTFS permissions to users and groups.
Normally, NTFS permissions are
cumulative, based on group memberships if the user has been allowed
access. This means that the user gets the highest level of security from
all the different groups they belong to. However, if the user had been
denied access through user or group membership, those permissions
override the allowed permissions. Windows 7 offers seven levels of NTFS
permissions plus special permissions:
Full Control This permission allows the following rights:
Traverse folders
and execute files (programs) in the folders. The ability to traverse
folders allows you to access files and folders in lower subdirectories,
even if you do not have permissions to access specific portions of the
directory path.
List the contents of a folder and read the data in a folder's files.
See a folder's or file's attributes.
Change a folder's or file's attributes.
Create new files and write data to the files.
Create new folders and append data to the files.
Delete subfolders and files.
Delete files.
Compress files.
Change permissions for files and folders.
Take ownership of files and folders.
If you select the Full Control permission, all permissions will be checked by default and can't be unchecked.
Modify This permission allows the following rights:
Traverse folders and execute files in the folders.
List the contents of a folder and read the data in a folder's files.
See a file's or folder's attributes.
Change a file's or folder's attributes.
Create new files and write data to the files.
Create new folders and append data to the files.
Delete files.
If you select the Modify
permission, the Read & Execute, List Folder Contents, Read, and
Write permissions will be checked by default and can't be unchecked.
Read &c Execute This permission allows the following rights:
Traverse folders and execute files in the folders.
List the contents of a folder and read the data in a folder's files.
See a file's or folder's attributes.
If you select the Read
& Execute permission, the List Folder Contents and Read permissions
will be checked by default and can't be unchecked.
List Folder Contents This permission allows the following rights:
Read This permission allows the following rights:
Write This permission allows the following rights:
Overwrite a file.
View file ownership and permissions.
Change a file's or folder's attributes.
Create new files and write data to the files.
Create new folders and append data to the files.
Special Permissions This allows you to configure any permissions beyond the normal permissions, like auditing, and take ownership.
Any user with Full Control
access can manage the security of a folder. However, to access folders,
a user must have physical access to the computer as well as a valid
logon name and password. By default, regular users can't access folders
over the network unless the folders have been shared.
To apply NTFS permissions,
right-click the file or folder to which you want to control access,
select Properties from the context menu, then select the Security tab.
The Security tab lists the users and groups that have been assigned
permissions to the file or folder. When you click a user or group in the
top half of the dialog box, you see the permissions that have been
allowed or denied for that user or group in the bottom half.
Complete Exercise 1 to manage NTFS security.
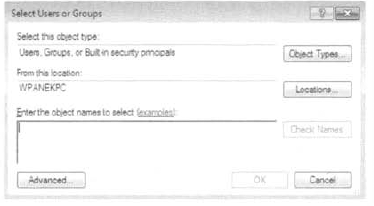
Right-click
the file or folder to which you want to control access, select
Properties from the context menu, and click the Security tab. Click the Edit button to modify permissions. Click
the Add button to open the Select Users Or Groups dialog box. You can
select users from the computer's local database or from the domain you
are in (or trusted domains) by typing in the user or group name in the
Enter The Object Names To Select portion of the dialog box and clicking
OK.
You
return to the Security tab of the folder Properties dialog box.
Highlight a user or group in the top list box, and in the Permissions
list, specify the NTFS permissions to be allowed or denied. When you
have finished, click OK.
|
Through the Advanced button
of the Security tab, you can configure more granular NTFS permissions,
such as Traverse Folder and Read Attributes permissions.
To remove the NTFS
permissions for a user, computer, or group, highlight that entity in the
Security tab and click the Remove button. Be careful when you remove
NTFS permissions. You won't be asked to confirm their removal as you are
when deleting most other types of items in Windows 7.
3.2. Controlling Permission Inheritance
Normally, the
directory structure is organized in a hierarchical manner. This means
you are likely to have subfolders in the folders to which you apply
permissions. In Windows 7, by default, the parent folder's permissions
are applied to any files or subfolders in that folder as well as any
subsequently created objects. These are called inherited permissions.
You can specify how permissions
are inherited by subfolders and files by clicking the Advanced button
on the Security tab of a folder's Properties dialog box. This calls up
the Permissions tab of the Advanced Security Settings dialog box. To
edit these options, click the Change Permissions button. You can edit
the following options:
If an Allow or a Deny check box
in the Permissions list on the Security tab has a shaded check mark,
this indicates that the permission was inherited from an upper-level
folder.
If the check mark is not shaded,
it means the permission was applied at the selected folder. This is
known as an explicitly assigned permission. Knowing which permissions
are inherited and which are explicitly assigned is useful when you need
to troubleshoot permissions.
3.3. Understanding Ownership and Security Descriptors
When an object is
initially created on an NTFS partition, an associated security
descriptor is created. A security descriptor contains the following
information:
The user or group that owns the object
The users and groups that are allowed or denied access to the object
The users and groups whose access to the object will be audited
After an object is created, the
Creator Owner of the object has full permissions to change the
information in the security descriptor, even for members of the
Administrators group. You can view the owner of an object from the
Security tab of the specified folder's Properties by clicking the
Advanced button. Then click the Owner tab to see who the owner of the
object is. From this dialog box you can change the owner of the object.
Although the owner of an
object can set the permissions of an object so that the administrator
can't access the object, the administrator or any member of the
Administrators group can take ownership of an object and thus manage the
object's permissions. When you take ownership of an object, you can
specify whether you want to replace the owner on subdirectories and
objects of the object. If you would like to see who owns a directory
from the command prompt, type dir /q.
In the next section, we will discuss how to determine the effective permissions of a file or folder.
4. Determining Effective Permissions
To determine a user's
effective rights (the rights the user actually has to a file or folder),
add all of the permissions that have been allowed through the user's
assignments based on that user's username and group associations. After
you determine what the user is allowed, you subtract any permissions
that have been denied the user through the username or group
associations.
As an example, suppose
that user Marilyn is a member of both the Accounting and Execs groups.
The following assignments have been made to the Accounting group
permissions:
| Permission | Allow | Deny |
|---|
| Full Control | | |
| Modify | X | |
| Read & Execute | X | |
| List Folder Contents | | |
| Read | | |
| Write | | |
The following assignments have been made to the Execs group permissions:
| Permission | Allow | Deny |
|---|
| Full Control | | |
| Modify | | |
| Read & Execute | | |
| List Folder Contents | | |
| Read | X | |
| Write | | |
To determine Marilyn's
effective rights, you combine the permissions that have been assigned.
The result is that Marilyn's effective rights are Modify, Read &C Execute, and Read, so she basically has Modify (the highest right).
As another example, suppose
that user Dan is a member of both the Sales and Temps groups. The
following assignments have been made to the Sales group permissions:
| Permission | Allow | Deny |
|---|
| Full Control | | |
| Modify | X | |
| Read & Execute | X | |
| List Folder Contents | X | |
| Read | X | |
| Write | X | |
The following assignments have been made to the Temps group permissions:
| Permission | Allow | Deny |
|---|
| Full Control | | |
| Modify | | X |
| Read & Execute | | |
| List Folder Contents | | |
| Read | | |
| Write | | X |
To determine Dan's effective
rights, you start by seeing what Dan has been allowed: Modify, Read
& Execute, List Folder Contents, Read, and Write permissions. You
then remove anything that he is denied: Modify and Write permissions. In
this case, Dan's effective rights are Read & Execute, List Folder
Contents, and Read. Now let's take a look at how to see what rights
users have.
5. Viewing Effective Permissions
If permissions have been
applied at the user and group levels and inheritance is involved, it
can sometimes be confusing to determine what the effective permissions
are. To help identify which effective permissions will actually be
applied, you can view them from the Effective Permissions tab of
Advanced Security Settings, or you can use the ICACLS command-line
utility.
To see what the effective
permissions are for a user or group, you click the Select button and
then type in the user or group name. Then click OK. If a box is checked
and not shaded, then explicit permissions have been applied at that
level. If the box is shaded, then the permissions to that object were
inherited.
The ICACLS command-line
utility can also be used to display or modify user access rights. The
options associated with the ICACLS command are as follows:
/grant grants permissions.
/remove revokes permissions.
/deny denies permissions.
/setintegritylevel sets an integrity level of Low, Medium, or High.
One issue that IT people run
into is what happens to the security when you move or copy a file or
folder. Let's take a look at NTFS permissions when moved or copied.
6. Determining NTFS Permissions for Copied or Moved Files
When you copy or move NTFS
files, the permissions that have been set for those files might change.
The following guidelines can be used to predict what will happen:
If you move a file from one folder to another folder on the same volume, the file will retain the original NTFS permissions.
If
you move a file from one folder to another folder between different
NTFS volumes, the file is treated as a copy and will have the same
permissions as the destination folder.
If you copy a file from one folder to another folder on the same volume or
on a different volume, the file will have the same permissions as the destination folder.
If you copy or move a file or folder to a FAT partition, it will not retain any NTFS permissions.
Now that you have seen how to
deal with the NTFS security, you need to understand shared permissions.
In the next section, we will look at sharing resources.