1. Effective Permissions
Admittedly, the subject of permissions can be fraught with
anxiety—one reason simplicity should be your watchword. However, there
will be times when a resource will have acquired a kudzu-like
accretion of permissions and it will be your job to wield the
machete.
To determine what the effective permissions are on an
object—that is, what permissions apply to a given user or group—follow
these steps:
Right-click the file or folder for which you want to view
permissions. Select Properties.
Click the Security tab and then click Advanced. Click the
Effective Permissions tab.
Click the Select button to open the Select User, Computer,
Or Group dialog box.
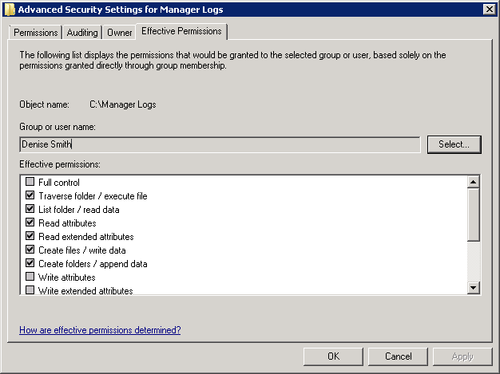
Locate the user or group you want and then click OK. The
selected check boxes (as shown in Figure 1) indicate the effective
permissions of the user or group for that file or folder.
Note:
Share permissions are not part of the effective permissions
calculation. Access to shared folders can be denied through share
permissions even when access is allowed through NTFS file
permissions.
1.1. Factors Considered in Determining Effective
Permissions
The factors that are considered when determining effective
permissions are as follows:
Global group membership
Local group membership (except when accessing objects
remotely)
Local permissions
Local privileges (except when accessing objects
remotely)
Universal group membership
2. Defining User Rights
As if various kinds of permissions weren’t enough, we must also
address the concept of user rights.
What users can and cannot do depends on the rights and
permissions that have been granted to them. Rights generally apply to
the system as a whole. The ability to back up files or to log on to a
server, for example, is a right that the administrator can grant or
withhold. Rights can be assigned individually, but most often they are
characteristics of groups, and a user is assigned to a particular
group on the basis of the rights that the user needs.
Permissions, indicate the access that a user (or group) has to specific
objects, such as files, directories, and printers. For example, the
question of whether a user can read a particular directory or access a
network printer is a permission.
Rights, on the other hand, are divided into
two types: privileges and logon rights. Privileges include
such functions as the ability to run security audits or force shutdown
from a remote system—obviously not tasks that are done by most users.
Logon rights are almost self-explanatory: they
involve the ability to connect to a computer in specific ways. Rights
are automatically assigned to the groups in Windows SBS 2008, although
they can be assigned to individual users as well. Assignment by group
is usually preferred, so whenever possible, assign rights by group
membership to keep administration simple.
When membership in groups defines rights, rights can be removed
from a user by simply removing the user from the group. Table 1 lists the logon
rights and the groups to which they are assigned by default.
Table 1. Logon rights assigned to groups by default
| NAME | DESCRIPTION | GROUPS ASSIGNED THE RIGHT ON THE SBS DOMAIN
CONTROLLER | GROUPS ASSIGNED THE RIGHT ON WORKSTATIONS AND
SERVERS |
|---|
| Access This Computer From The
Network | Permits connection to the computer through the
network | Administrators, Authenticated Users,
Everyone | Administrators, Backup Operators, Users,
Everyone |
| Allow Logon Locally | Permits logging on to the computer
interactively | Administrators, Account Operators, Backup
Operators, Print Operators, Server Operators | Administrators, Backup Operators,
Users |
| Allow Logon Through Terminal
Services | Allows logging on as a Terminal Services
client | Administrators | Administrators, Remote Desktop
Users |
In Windows SBS, it is much simpler to control logon access through individual user accounts unless
your network is relatively large and you are using Windows Server 2008
built-in groups in addition to Windows SBS groups.
3. Managing Default User Rights Assignments
To see the user rights assignment on the Windows SBS server, select
Administrative Tools from the Start menu and then select Local
Security Policy. Expand Local Policies and then click User Rights Assignment.
To change one of the policies, right-click the name and select
Properties. If the Add Users Or Group button is available (as shown in
Figure 2), you can
click it to add additional users who will have the user right.
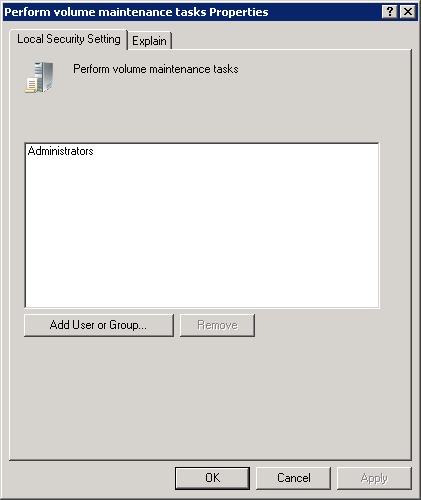
If the Add Users Or Group button is unavailable, this user right
can be granted only by adding the user or group to the groups already
listed.