3. Components of an Active Directory Infrastructure
AD DS provides the foundation for IDA in and management of an
enterprise network. It is worthwhile to spend a few moments reviewing
the components of an Active Directory infrastructure.
Note:
WHERE TO FIND ACTIVE DIRECTORY DETAILS
For more details about
Active Directory, refer to the product Help installed with Windows
Server 2008 and to the Windows Server 2008 R2 home page located at http://technet.microsoft.com/en-us/windowsserver/bb310558.aspx.
Active Directory data store As mentioned in the previous section, AD DS stores its identities in the directory—a data store hosted on domain controllers. The directory is a single file database named Ntds.dit
and is located by default in the %SystemRoot%\Ntds folder on a domain
controller. The database is divided into several partitions, including
the schema, the configuration, and the domain naming context that
contains the data about objects within a domain—the users, groups, and
computers, for example. Depending on the environment, there may also be
application partitions and a partial attribute set (PAS), also called the global catalog. Domain controllers
Domain controllers (DCs) are servers that perform the AD DS role and
maintain a copy of the Active Directory data store, along with other
data important to the domain. As part of that role, they also run the
Kerberos Key Distribution Center (KDC) service, which performs
authentication and other Active Directory services. Domain One or more domain controllers are required to create an Active Directory domain.
A domain is an administrative unit within which certain capabilities
and characteristics are shared. First, all domain controllers replicate
the domain’s partition of the data store, which contains, among other
things, the identity data for the domain’s users, groups, and computers.
Because all DCs maintain the same identity store, any DC can
authenticate any identity in a domain. Additionally, a domain defines
the boundaries of administrative policies such as password complexity
and account lockout policies. Such policies configured in one domain
affect all accounts in the domain and do not affect accounts in other
domains. Changes can be made to objects in the Active Directory database
by any domain controller and will replicate to all other domain
controllers. Therefore, in networks where replication of all data
between domain controllers cannot be supported, it might be necessary to
implement more than one domain to manage the replication of subsets of
identities. Forest A forest is a collection of one or more Active Directory domains. The first domain installed in a forest is called the forest root domain. A forest contains a single definition of network configuration and a single instance of the directory schema. A forest
is a single instance of the directory—no data is replicated by Active
Directory outside the boundaries of the forest. Therefore, the forest
defines a security boundary. Tree The DNS namespace of domains in a forest creates trees within the forest. If a domain is a subdomain of another domain, the two domains are considered a tree. For example, if the treyresearch.net forest contains two domains, treyresearch.net and antarctica.treyresearch.net,
those domains constitute a contiguous portion of the DNS namespace, so
they are a single tree. If, conversely, the two domains are treyresearch.net and proseware.com,
which are not contiguous in the DNS namespace, the domain is considered
to have two trees. Trees are the direct result of the DNS names chosen
for domains in the forest.
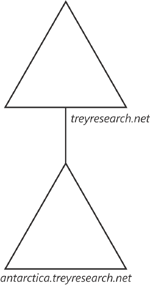
Figure 2
illustrates an Active Directory forest for Trey Research, which
maintains a small operation at a field station in Antarctica. Because
the link from Antarctica to the headquarters is expensive, slow, and
unreliable, Antarctica is configured as a separate domain. The DNS name
of the forest is treyresearch.net. The Antarctica domain is a child domain in the DNS namespace, antarctica.treyresearch.net, so it is considered a child domain in the domain tree.
Functional level The functionality available in an Active Directory domain or forest depends on its functional level.
The functional level is an AD DS setting that enables advanced
domain-wide or forest-wide AD DS features. There are six domain
functional levels (Windows 2000 native, Windows 2000 mixed, Windows
Server 2003, Windows Server 2003 interim, Windows Server 2008, and
Windows Server 2008 R2) and five forest functional levels (Windows
Server 2000, Windows Server 2003, Windows Server 2003 interim, Windows
Server 2008, and Windows Server 2008 R2). As you raise the functional
level of a domain or forest, features provided by that version of
Windows become available to AD DS. For example, when the forest
functional level is raised to Windows Server 2008 R2, the ability to
enable the Active Directory Recycle Bin becomes available. With the
Active Directory Recycle Bin, objects deleted within Active Directory
are preserved in the state they were in prior to deletion. This allows
easy restoration of previously deleted objects, if required. The
important thing to know about functional levels is that they determine
the versions of Windows permitted on domain controllers. Before you
raise the domain functional level to Windows Server 2008, all domain
controllers must be running Windows Server 2008.
Organizational units
Active Directory is a hierarchical database. Objects in the data store
can be collected in containers. One type of container is the object
class called container.
You see the default containers, including Users, Computers, and
Builtin, when you open the Active Directory Users And Computers snap-in.
Another type of container is the organizational unit
(OU). OUs provide not only a container for objects but also a scope
with which to manage the objects. That is because OUs can have objects
called Group Policy objects
(GPOs) linked to them. GPOs can contain configuration settings that
will be applied automatically by users or computers in an OU.
Sites
When you consider the network topology of a distributed enterprise, you
will certainly discuss the network’s physical locations or sites. Sites
in Active Directory, however, have a very specific meaning. An Active
Directory site is an object that represents a portion of the enterprise
within which consistent, high-bandwidth network connectivity is
expected. A site creates a boundary of replication and service usage.
Domain controllers within a site replicate changes within seconds.
Between different sites, however, changes are replicated on a controlled
basis with the assumption that intersite connections are slow,
expensive, or unreliable compared to the connections within a site.
Additionally, clients prefer to use distributed services provided by
servers in their site or in the closest site. For example, when a user
logs on to the domain, the Windows client first attempts to authenticate
with a domain controller in its site. Only if no domain controller is
available in the site will the client attempt to authenticate with a DC
in another site.
Each of these components
is discussed in detail later in this training kit. At this point, if
you are less familiar with Active Directory, it is important only that
you have a basic understanding of the terminology, the components, and
their relationships.
4. Preparing to Create a New Windows Server 2008 Forest
Before you install the AD DS
role on a server and promote it to act as a domain controller, plan your
Active Directory infrastructure. Some of the information you will need
to create a domain controller includes the following:
The domain’s name and
DNS name. A domain must have a unique DNS name, such as contoso.com, as
well as a short name, such as CONTOSO, called a NetBIOS name. NetBIOS is a network protocol
that has been used since the first versions of Microsoft Windows NT and
is still specified and used for backward compatibility. Whether
the domain will need to support domain controllers running previous
versions of Windows. When you create a new Active Directory forest, you
will configure the functional level. If the domain will include only
Windows Server 2008 R2 domain controllers, you can set the functional
level accordingly to benefit from the enhanced features introduced by
this version of Windows. Details for how DNS will be implemented to support Active Directory. It is a best practice to implement DNS for your Windows domain zones by using Windows DNS Service; however, it is possible to support a Windows domain on a third-party DNS service. IP
configuration for the domain controller. Domain controllers require
static IP addresses and subnet mask values. Additionally, the domain
controller must be configured with a DNS server address to perform name
resolution. If you are creating a new forest and will run Windows DNS
Service on the domain controller, you can configure the DNS address to
point to the server’s own IP address. After DNS is installed, the server
can look to itself to resolve DNS names. The
user name and password of an account in the server’s Administrators
group. The account must have a password—the password cannot be blank. The location in which the data store (including Ntds.dit)
and system volume (SYSVOL) should be installed. By default, these
stores are created in %SystemRoot%; for example, C:\Windows, in the NTDS
and SYSVOL folders, respectively. When creating a domain controller,
you can redirect these stores to other drives.
Note:
MORE INFO DEPLOYMENT OF AD DS
This list comprises the
settings that you are prompted to configure when creating a domain
controller. There are several additional considerations regarding the
deployment of AD DS in an enterprise setting that you should review. See
the AD DS Deployment Guide at http://technet.microsoft.com/en-us/library/cc753963(WS.10).aspx for more information.
5. Adding the AD DS Role Using the Windows Interface
After you have collected the
prerequisite information listed earlier, you are ready to add the AD DS
role. There are several ways to do so. In this lesson, you learn how to
create a domain controller by using the Windows interface. In the next
lesson, you learn to do so by using the command line.
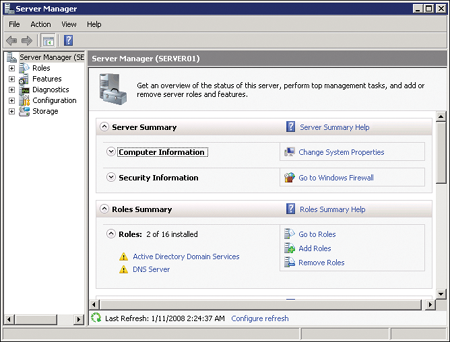
Windows Server 2008
provides role-based configuration, installing only the components and
services required for the roles a server plays. This role-based server
management is reflected in the administrative console, Server Manager,
as shown in Figure 3. Server Manager consolidates the information, tools, and resources needed to support a server’s roles.
You can add roles to a server by using
the Add Roles link on the home page of Server Manager or by
right-clicking the Roles node in the console tree and choosing Add
Roles. The Add Roles Wizard presents a list of roles available for installation and guides you through the installation of selected roles.
|