Almost any application build
by Microsoft has a high level of integration and dependency with Active
Directory; Lync Server is no exception. Lync Server cannot be installed
without Active Directory and it needs certain attributes available in
Active Directory. Lync Server provides wizards that help administrators
properly prepare and configure Active Directory to properly support Lync
Server. Following these configurations, in order, makes it easy for an
administrator to deploy Lync Server successfully.
Active Directory requirements include
All Domain Controllers (DC) in the forest must be 2003 SP2 or higher.
The domain functional level for domains containing Lync Server must be 2003 Native or higher (not 2003 Interim).
The forest functional level for the forest must be 2003 Native or higher (not 2003 Interim).
Schema Extensions
To
provide the necessary attributes used by Lync Server, it is necessary
to extend the schema with the provided extensions. This process is
easiest to run on a system destined to be a Lync Server, and by someone
who is currently a member of the Schema Administrators group must
perform it. If you add your account to Schema Administrators for
installing Lync Server, be sure to log off and on to ensure you have a
Kerberos ticket that reflects the recent group membership change. Prior
to extending the schema, first install the following components:
From the Lync Server installation media, follow these steps:
1. | Launch Setup.exe.
|
2. | When the wizard displays, browse to your intended installation location. Choose whether to check for updates, and then click OK.
|
3. | When prompted, carefully read the software license terms, and then click the I accept the terms in the license agreement option if you agree to the terms. Then click OK.
|
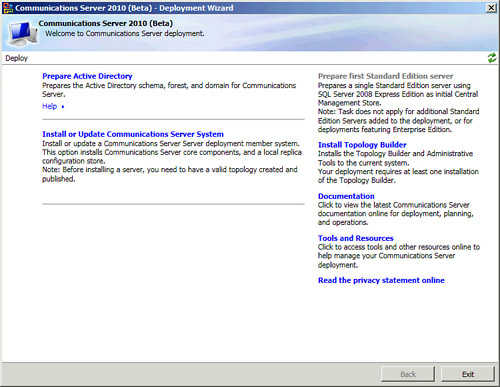
4. | When
the Deployment Wizard launches, it determines the current state of the
environment and prompts you for installations as needed. In the case of a
fresh installation, you are offered the opportunity to prepare Active
Directory. Click Prepare Active Directory, as shown in Figure 1.
Note
Be sure the Schema Master role is available and that you have Schema Admin credentials.
|
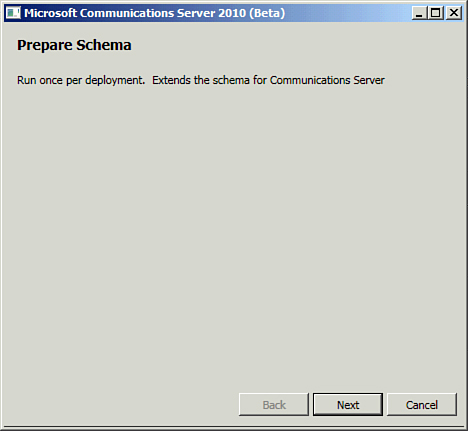
5. | Assuming the prerequisites are met, click Run on Step 1: Prep Schema, which will launch the wizard shown in Figure 2.
|
6. | Click Next.
|
7. | When the commands are executed, click Finish.
|
8. | Using tools such as Repadmin or ADSIEDIT, spot check DCs to ensure that the updated schema partition has replicated.
|
New Active Directory classes created include
msRTCSIP-GlobalTopologySettings— This class is a container that holds global topology setting objects.
msRTCSIP-GlobalTopologySetting— The local global topology setting object.
msRTCSIP-ConnectionPoint-Generic— SCP to specify computer as a Live Lync Server.
New Active Directory attributes include
msRTCSIP-TenantId— This attribute is a unique identifier of the tenant. This identifier should be unique across all tenants.
msRTCSIP-UserPolicies— This attribute is used to store name-value pairs.
msRTCSIP-OwnerUrn— This attribute is the Uniform Resource Name (URN) of the owner for the application contact.
msRTCSIP-TargetUserPolicies— This attribute is used to store name-value pairs for target policies on a Lync Server user.
msRTCSIP-DeploymentLocator— This attribute is used in a split-domain topology and contains a fully qualified domain name (FQDN).
msRTCSIP-PrivateLine— This attribute contains the device ID of a private line device.
msRTCSIP-AcpInfo— This attribute is used to store user audio conferencing provider information.
msRTCSIP-GroupingID— This attribute is a unique identifier of a group, used to group address book entries.
ms-Exch-UC-Voice-Mail-Settings— This multivalued attribute holds voice mail settings. This attribute is shared with Exchange Unified Messaging (UM).
The following Active Directory classes are modified to add a mayContain:
Forest Prep
After the schema has been
updated, the setup enables you to continue the remaining steps. The next
logical step is to prepare the forest for the Lync Server installation.
Continuing with the existing Deployment Wizard, follow these steps:
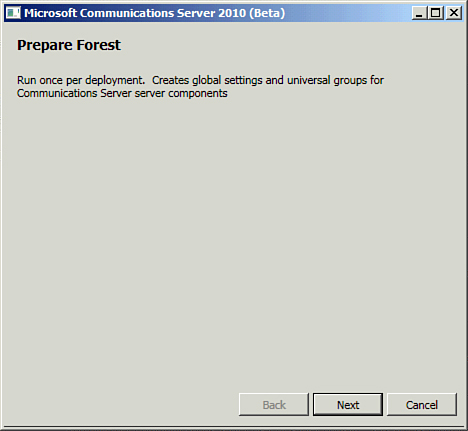
1. | Click Run on Step 3: Prepare Current Forest. The Prepare Forest task will launch as shown in Figure 3.
|
2. | Click Next.
|
3. | When the commands are executed, click Finish.
|
4. | Verify that the changes Forest Prep performed have replicated.
|
Tip
An easy way to do this is to use ADSIEdit or Ldp to check multiple DCs to see whether the new CS and RTC groups are present.
Domain Prep
As with most
Microsoft applications, after the forest is prepared, the domain must be
prepared. Important to note is that the steps domain prep performs are
different from those in forest prep. So even if a forest is comprised of
a single domain, it is necessary to perform both tasks. Domain prep
should be performed on all domains that host Lync Server users or
servers.
1. | Click Run on Step 5: Prepare Current Domain.
|
2. | When the commands are executed, click Finish.
|
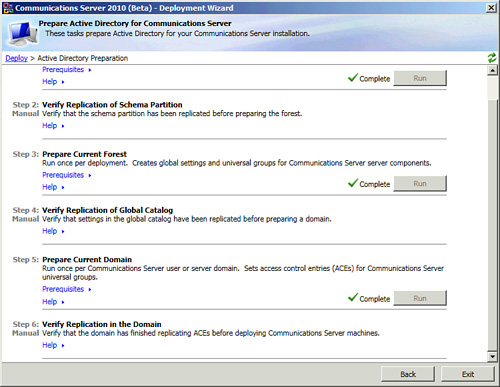
3. | Verify
replication of the Access Control Entries set by Domain Prep, and then
click Exit. This will return you to the Deployment Wizard, as shown in Figure 4.
|
2010 Security Groups
Domain Prep performs
several tasks, including setting permissions on various objects and
containers and creating several groups for use with Lync Server. The
groups created are detailed lists.
The service groups are
RTCHSUniversalServices—
Includes service accounts used to run Front End Server and enables
servers read/write access to Lync Server global settings and Active
Directory user objects
RTCComponentUniversalServices—
Includes service accounts used to run conferencing servers, web
services, Mediation Server, Archiving Server, and Monitoring Server
RTCProxyUniversalServices— Includes service accounts used to run Lync Server Edge Servers
The administration groups are
RTCUniversalServerAdmins— Allows members to manage server and pool settings
RTCUniversalUserAdmins— Allows members to manage user settings and move users from one server or pool to another
RTCUniversalReadOnlyAdmins— Allows members to read server, pool, and user settings
The infrastructure groups are
RTCUniversalGlobalWriteGroup— Grants write access to global setting objects for Lync Server.
RTCUniversalGlobalReadOnlyGroup— Grants read-only access to global setting objects for Lync Server.
RTCUniversalUserReadOnlyGroup— Grants read-only access to Lync Server user settings.
RTCUniversalServerReadOnlyGroup—
Grants read-only access to Lync Server settings. This group does not
have access to pool-level settings; it accesses only settings specific
to an individual server.
Forest preparation then adds service and administration groups to the appropriate infrastructure groups, as follows:
RTCUniversalServerAdmins
is added to RTCUniversalGlobalReadOnlyGroup,
RTCUniversalGlobalWriteGroup, RTCUniversalServerReadOnlyGroup, and
RTCUniversalUserReadOnlyGroup.
RTCUniversalUserAdmins
is added as a member of RTCUniversalGlobalReadOnlyGroup,
RTCUniversalServerReadOnlyGroup, and RTCUniversalUserReadOnlyGroup.
RTCHSUniversalServices,
RTCComponentUniversalServices, and RTCUniversalReadOnlyAdmins are added
as members of RTCUniversalGlobalReadOnlyGroup,
RTCUniversalServerReadOnlyGroup, and RTCUniversalUserReadOnlyGroup.
Forest preparation also creates the following role-based access control (RBAC) groups: