Encrypting Communications Between Outlook and Exchange
As
a MAPI client, Outlook 2007 uses RPCs to communicate with Exchange
Server 2007. RPCs are interprocess communications (IPC) mechanisms that
can either use or not use encryption during the transfer of
information. By default, Outlook 2007 encrypts data between Outlook and
the Exchange server. However, Outlook 2003 does not have this security
feature enabled by default.
To enable this feature in Outlook 2003, perform the following steps:
1. | In Outlook 2003, select Tools, E-Mail Accounts.
|
2. | Select View or Change Existing E-Mail Accounts, and then click Next.
|
3. | Click Change and, on the next window, click More Settings.
|
4. | Select
the Security tab. Under the Security section, click the Encrypt Data
Between Microsoft Office Outlook and Microsoft Exchange Server check
box.
|
5. | Click OK to close the window.
|
6. | Click Next and then click Finish when you are done.
|
Authenticating Users
By
default, both Outlook 2003 and Outlook 2007 use the credentials of the
user who is currently logged on to the local computer to access the
Outlook profile and mailbox. Both applications are also configured to
first utilize Kerberos for the authentication process and, if this
fails, utilize NT LAN Manager (NTLM). Administrators have the option of
setting Outlook to only use Kerberos if they want to implement stronger
security methods. The Kerberos/NTLM or NTLM Only options exist for
backward compatibility with older systems. When using Kerberos, the
user’s credentials are encrypted when communicating with Active
Directory for authentication.
To view or change the current authentication options in Outlook 2007, perform the following procedure:
1. | In Outlook 2007, select Tools, Account Settings.
|
2. | On the Account Settings page, select the email account, and click the Change icon.
|
3. | On the Change E-Mail Account page, click More Settings.
|
4. | Select
the Security tab. Under Logon Network Security, select Kerberos
Password Authentication from the drop-down box, and then click OK.
|
5. | On the Change E-Mail Account page, click Next to complete the process, click Finish, and then click Close.
|
User Identification
An
additional level of security can be applied to users accessing email
through the Outlook client. In the event of a user closing Outlook, but
not locking their computer or logging off the network, it is possible
for an unauthorized user to access the system, start Outlook, and
access the user’s email.
It is possible to
configure Outlook 2007 to require the user to input their username and
password before accessing Outlook.
It
should be noted that few organizations implement this security option,
as most find that logging on and off the system properly provides
adequate protection.
Blocking Attachments
A
common and often effective way for viruses and malicious scripts to
spread from user to user is through email. When a user receives a
message with an attachment, simply opening the attachment can allow the
virus to activate and, if proper security measures are not in place,
the virus can do damage to the system or spread to other users.
To
mitigate this threat, Microsoft has incorporated attachment blocking in
Outlook and Outlook Web Access (OWA). By default, Outlook is configured
to block attachments that contain file types that can run programs.
Known as “executable” files, these blocked file types include those
with .exe, .bat, .com, .vbs, and .js on the end of the filename.
It
is important to note that this does not automatically protect you from
being infected with a virus, as other file formats, including Microsoft
Office files such as Word or Excel documents, can potentially contain
viruses. However, implementing an antivirus solution on the client PC
greatly reduces the possibility of such a file causing harm.
Users
who are utilizing Outlook to send an attachment are notified when
attaching an executable file that it is likely to be blocked by the
recipient. An example of the warning message received is shown in Figure 2.
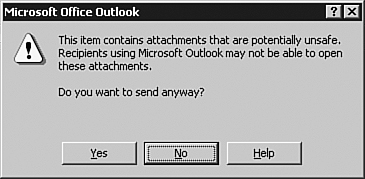
If the user elects to send the message anyway, it might still be blocked on the receiving end.
Outlook
does not provide any way for the end user to unblock these attachments.
However, savvy users have found that, in many instances, they can
rename the file to a nonexecutable extension (such as .txt) and send the file with instructions on how to rename the file back.
Note
File
types can be categorized as Level 1 (the user cannot view the file) or
Level 2 (the user can open the file only after saving it to disk). By
default, Outlook classifies most executable file types as Level 1 and
blocks the receipt of the file by users. There are no Level 2 file
types by default. However, administrators can use Group Policy to
manage how a file type is categorized. For example, if members of your
organization regularly receive Visual Basic scripts (.vbs),
you can change the categorization from Level 1 to Level 2 for that
extension. Extreme caution should be used before changing this setting,
as executable attachments are one of the most commonly used methods of
distributing viruses.