Keeping Up with Security Patches and Updates
Applying
service packs, updates, and hotfixes in a timely manner is critical to
maintaining the security of an environment. Whether you are talking
about a server operating system, an application such as Exchange Server
2007, a client operating system, or even client applications, keeping
your systems up to date with the latest releases ensures that you are
protected against known vulnerabilities.
Organizations
often underestimate the importance of these updates, so let’s look at
them in a different light. These updates are released to protect
against known vulnerabilities. That means that there is a good possibility that malicious users in the hacker community already know how to exploit them. So, there the system sits, not only does it have an unlocked door, but the criminals know it is unlocked.
In
the past, updates often had to be manually implemented on a
system-by-system basis and, for companies with hundreds (or thousands)
of workstations, it proved to be a monumental task. These manual
processes still exist, but rarely need to be used today.
With
Windows Server 2003, Windows Vista, and Windows XP, utilities exist
that allow you to automate this process and simplify the distribution
of updates. Microsoft has provided several options: Windows Update,
Microsoft Update, Microsoft Windows Server Update Services (WSUS), and
Microsoft Systems Management Server (SMS). In addition, there are a
variety of third-party applications that can assist you with this
endeavor.
Note
In
today’s environments, distribution of updates is often considered the
“easy” part. Automated methods of deployment have made the process
fairly simple. However, one of the most important steps, and one of the
most often overlooked, is the thorough and complete testing of updates
in a lab environment before the release to a production environment.
Strongly consider implementing a patch management system that includes
adequate time and resources for testing.
Windows Update
Windows Update, located at http://www.microsoft.com/windowsupdate,
is a website that scans a local system and determines whether it has
the latest updates applicable to the operating system. Windows Update
is a very useful tool when dealing with a small number of systems. One
shortcoming of Windows Update is that it only addresses updates to the
operating system—not to any applications installed on the computer.
Windows Update was designed for Microsoft Windows 2000 SP2 and earlier.
Those using later versions of the operating system (including Windows
2000 SP3 and higher, Windows 2003, Windows Vista, and Windows XP) can
instead use the Microsoft Update discussed in the following section.
Microsoft Update
So,
what are you to do for the other Microsoft applications on your system,
including Microsoft Outlook? Enter Microsoft Update, located at http://update.microsoft.com.
This website offers the same downloads available on the Windows Update
site, plus the latest updates for Microsoft Office and other Microsoft
applications.
When you visit the website,
it scans your computer and allows you to review a list of available
updates and select the ones you want to implement.
The
site breaks down the available updates into categories, identifying
those that are critical to the security and reliability of your
computer as high-priority updates. Interestingly enough, updates to the
antispam features of Microsoft Outlook are considered high-priority
updates as well, showing that Microsoft has listened to the user
community and no longer considers spam to be simply a “nuisance.”
One
other feature of the Microsoft Update website is the ability to review
your update history. By selecting this link, you can see the update,
the product it applied to, the status of the implementation, the date
it was applied, and the method used to apply the patch—for example,
Windows Update or Automatic Updates, which is discussed in the next
section.
Like Windows Update, Microsoft
Update is intended for managing one system at a time. As useful as it
is for individual users and small environments, other alternatives
should still be considered for larger organizations.
Note
You
can remove an update by using the Add and Remove Programs applet in
Control Panel. When this feature first appeared, it had the reputation
of being somewhat unreliable. Sometimes, updates were removed and the
system experienced problems afterward. However, this process has been
greatly improved over the past several years and is significantly more
stable and reliable now.
Automatic Updates
One
of the most reliable, and least time consuming, methods of implementing
updates from Microsoft is built in to Windows Server 2003, Windows
Vista, and Windows XP. Known as Automatic Updates,
this feature allows your system to automatically download and install
high-priority updates, without manual intervention. Optional updates,
however, still need to be implemented using other methods.
With Automatic Updates, shown in Figure 2,
you can configure the utility to automatically download and install
updates on a daily or weekly basis, at the time of day of your choice
(for example, every Saturday at 2:00 a.m.).
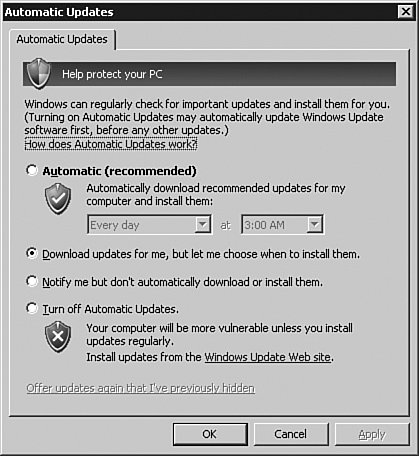
Alternatively, you can select one of the following options:
Download Updates for Me, But Let Me Choose When to Install Them.
Notify Me But Don’t Automatically Download or Install Them.
Turn Off Automatic Updates.
When
connecting to Microsoft Update or Windows Update, this method has a few
drawbacks that must be mentioned. First, by automatically downloading
and applying hotfixes, you are not afforded the opportunity to download
and implement them in a test lab prior to deployment. Second, some
high-priority updates require a reboot and might automatically restart
your system without your prior approval.
To mitigate these shortcomings, you can configure Automatic Updates to not
download and install updates directly from Microsoft, but can instead
receive updates from a Microsoft Windows Server Update Services (WSUS)
server, discussed next.
Windows Server Update Services (WSUS)
Realizing
the increased administration and management efforts that challenge
administrators of larger environments, Microsoft created the Microsoft
Software Update Services (SUS), and the newer version called Windows
Server Update Services (WSUS). This no-charge add-in component is
designed to simplify the process of keeping computers in your
organization up to date with the latest updates and service packs. WSUS
communicates directly and securely with Microsoft to gather the latest
security updates for a variety of Microsoft products, including
Exchange Server, and enables administrators to manage the distribution
of these updates to clients and servers in their environment. By
utilizing WSUS, administrators can download updates, test them, and
schedule the deployment to additional systems.
Utilizing
Background Intelligent Transfer Service (BITS), the application allows
administrators to download updates in the background, using available
network bandwidth, to minimize the impact on their user community.
WSUS version 3.0 includes a new MMC-based user interface and has the following features:
Advanced filtering and reporting
Improved performance and reliability
Branch office optimizations and reporting rollup
Microsoft Operations Manager Management Pack
Note
You can find more information on WSUS and download the product from http://www.microsoft.com/windowsserversystem/updateservices/default.mspx.
Client-Based Virus Protection
One
of the primary reasons why the installation of service packs and
software updates in a timely manner is so important is the prevalence
of computer viruses. Many viruses are written to exploit specific
vulnerabilities that are found in computer operating systems and
applications—both on clients and servers. Because Microsoft products
are used so widely throughout the world, those who create viruses
generally write them specifically to attack Microsoft products. This
has resulted in the creation of an entire industry focused solely on
protecting businesses and individuals from attack.
Companies
truly concerned with protecting their environment from attack should
use a multilayer approach to virus protection. By including antivirus
applications on gateways, Exchange servers, and on the desktop,
outbreaks can be prevented, or quickly detected and dealt with.
There
are many ways to distribute viruses, and one of the most effective is
by installing unauthorized software on a workstation and turning it
into a distribution point. This method might (or might not) utilize an
existing messaging system. If it does not, gateway and Exchange-level
antivirus methods might not be able to help at all. By implementing a
separate antivirus solution on the desktop itself, you can minimize
your exposure to attack.
An aggressive
plan should be in place to keep antivirus signature files and engines
up to date. Virus outbreaks that once took days (or weeks) to become
widespread can now travel around the globe in a matter of hours.
Antivirus updates (often referred to as “signature files”) should be
updated daily at a minimum and more often if your product supports it.
Windows Lockdown Guidelines and Standards
Microsoft
has gone to great lengths to provide secure and reliable products. This
endeavor was not accomplished in a vacuum—Microsoft has worked closely
with companies, government
agencies, security consultants, and others to identify and address
security issues in the computer industry. Through this concerted effort
and teamwork, security standards and guidelines have been developed
that are applicable to not only Microsoft products, but also to the
computing industry as a whole.
In
addition to researching and implementing Microsoft recommended security
standards and guidelines, responsible administrators can also use
recommended best practices that have been compiled by the National
Institute of Standards and Technologies (NIST) and the National
Security Agency (NSA).
Both NIST and NSA provide security lockdown configuration standards and guidelines that can be downloaded from their websites (http://www.nist.gov and http://www.nsa.gov, respectively).