Lync Mobility relies on various services and must be carefully planned
for to ensure a successful deployment. The LyncDiscover, UCWA, and MCX
services are all installed by default on all Front End Servers. No
additional configuration is required to install these services.
However, configuration is required for DNS, Certificates, Reverse
Proxy, Hardware Load Balancers, and Mobile policies. This section
outlines the steps to deploy Lync Mobile Services.
1. Certificate and DNS Requirements
The LyncDiscover service requires a static
DNS entry that is dedicated to this service. The DNS requirements for
Lync mobile are given in Table 1.
Table 1. LyncDiscover DNS Requirements
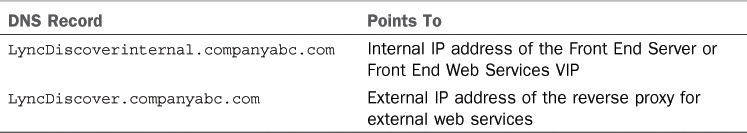
The LyncDiscover service will be used by
Mobile devices and Lync 2013 desktop clients. To properly support
devices that are connected to either the internal corporate network or
a public network, both the LyncDiscoverinternal and the LyncDiscover
records must be created, and must point to the appropriate IP addresses.
DNS Requirements for Push Notifications
As described earlier, push notifications
require federation with the Microsoft Push Notification Clearing House.
For this service to function properly, the appropriate DNS records must
be deployed to support inbound federation to the organization. This
includes the DNS SRV records for federation autodiscovery. The
Microsoft Push Notification Clearing House does not have the capability
for manually defining a Lync Access Edge Server for federation;
therefore, when push notification communicating is happening, the
service must validate the federation connection using the DNS SRV
records.
For push notifications to work, be sure to deploy the _sipfederationtls._tcp.<sipDomain> DNS SRV record, and point this record to the Access Edge Server used for federation.
Certificate Requirements for LyncDiscover
The certificate implications for the previous
requirements become increasingly important in Lync Server 2013. In the
past a single, privately issued certificate was common for all Front
End Services. When certificates are being configured for a Lync Front
End Server, there is an option to assign a certificate for Default,
Internal Web Services, and External Web Services. This essentially
enables administrators to assign a certificate for each of the web
service directories, and then all other Lync services. With Lync
Mobile, the possibility of devices that would not automatically trust
the privately issued certificate connecting to the LyncDiscoverinternal
service will require either the configuration of a public certificate
for the web services, or the manual installation of root certificates
on mobile devices.
Table 2 outlines a possible certificate configuration to provide Autodiscover Services to all endpoints.
Table 2. LyncDiscover Certificate Requirements
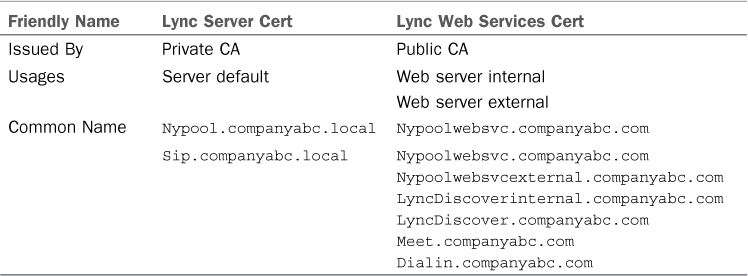
In the configuration outlined in Table 2,
the web services certificate could be applied to the Front End Server
web services, as well as the public reverse proxy interface. This would
allow for internal clients that are connecting to the internal
LyncDiscover service to connect seamlessly, as well as external clients.
The preceding example is just one
way to work with the certificate requirements for LyncDiscover. There
are many ways to meet the requirements of an organization. The key is
that the LyncDiscover records must be present on a certificate, and the
clients must trust that certificate.