With the agents configured, it is time to
begin discovering potential clients. Before you enable client
discovery, verify that Client Push Installation is configured properly.
If you have Client Push enabled and run a system discovery, you will
immediately begin to install the ConfigMgr client on all systems
assigned to the site (based on site boundaries). Client Push is not a
requirement for discovery. It is suggested you first use the Client
Push Installation Wizard to install clients, and then enable Client
Push.
Two common settings will appear through most discovery methods:
Recursive— When enabled, this specifies that the discovery method searches child objects.
Include Groups—
Discovers objects within groups. When this is enabled, you will
probably discover more objects, but this also increases the likelihood
of discovering the same object more than once.
Another
common element between most discovery methods is the Polling Schedule
tab. Use this tab to create a recurring schedule. You can also enable
the check box to run the discovery as soon as possible.
Active Directory System Group Discovery
Active
Directory (AD) System Group Discovery is a discovery method that polls
the domain controller for System Group objects in the domain or
Lightweight Directory Access Protocol (LDAP) path specified on a
schedule configured by the ConfigMgr administrator. Here are the
default group account attributes returned by Active Directory System
Group Discovery:
Organizational Unit
Global Groups
Universal Groups
Nested Groups
Nonsecurity Groups
AD
System Group Discovery will only discover these attributes for systems
that have previously been discovered by some other method (AD System
Discovery, Heartbeat Discovery). After enabling AD System Group
Discovery, click the starburst to configure the desired container to
search. As displayed in Figure 1, you have the ability to select the local domain or local namespace or use a custom LDAP or GC query.
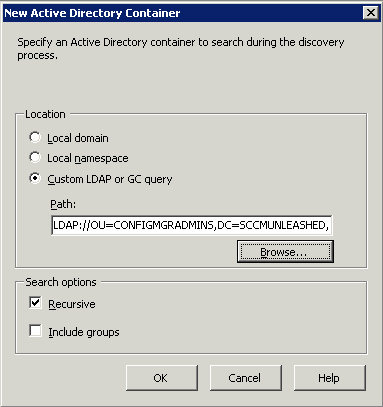
Review the log file adsysgrp.log for detailed information when the discovery method executes.
Active Directory Security Group Discovery
Active
Directory Security Group Discovery is a discovery method that polls the
domain controller for Security Group objects in the domain or LDAP
path, based on a schedule configured by the ConfigMgr administrator.
Configuring
this discovery method is very similar to configuring AD System Group
Discovery. AD Security Group Discovery will only discover these
attributes for systems previously discovered by some other method (AD
System Discovery, Heartbeat Discovery). Specify the container to
discover, and determine if you want to discover recursively, and within
groups. Finally, set a polling interval. Review the adsgdis.log file
for detailed information when the discovery method executes.
Active Directory System Discovery
Active
Directory System Discovery is the key discovery method used to create
data discovery records (DDRs) for computers. DDRs contain data such as
operating system (OS) name and version, Internet Protocol (IP)
addresses and subnets, and AD site names. You can use these DDRs to
target installations for client deployment. Active Directory System
Discovery is agentless, and you can use it to discover what is in your
environment before installing client agents on computers. This
capability gives the administrator an understanding of the network
infrastructure and deployment challenges in advance.
Configuring
this discovery method is very similar to configuring AD System Group
Discovery. Specify the container to discover, and determine if you want
to discover recursively, and within groups. Finally, set a polling
interval.
If you used Systems Management
Server (SMS) 2003, you will also notice a new tab named Active
Directory Attribute. This tab allows you to add more Active Directory
attributes to the system discovery process. You can add any computer
object attribute from Active Directory, such as
OperatingSystemServicePack and terminalserver.
Active Directory User Discovery
Active
Directory User Discovery is a discovery method that polls the domain
controller for user objects in the domain or LDAP path specified on a
schedule configured by the ConfigMgr administrator. Here are the
default user attributes returned by Active Directory User Discovery:
The
first two tabs are configured the same as the other Active Directory
discoveries—simply specify the container and polling interval. The most
interesting tab is the Active Directory Attribute tab, shown in Figure 2.
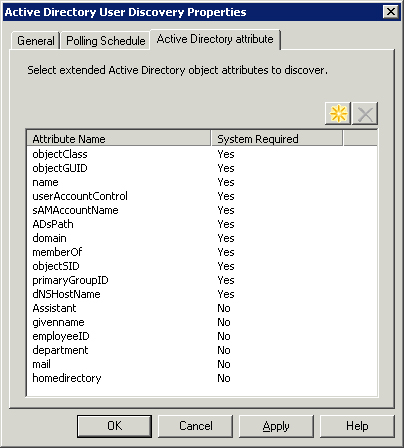
The
System Required column indicates whether the Attribute name is a
required attribute. All the attributes where System Required is equal
to No in Figure 2
are attributes manually added to discovery. As you can see, it is
possible to discover much more information about users than the
defaults. You can identify employeeID, mail (email address), manager,
department, and more. You can find all available attributes using the
ADSIEdit MMC snap-in.
Review the adusrdis.log file for detailed information when the discovery method executes.
|
For
all the AD discovery methods, if the Active Directory environment used
by ConfigMgr is not well maintained, you can end up with a lot of
garbage in your collections. Moreover, if you enable Push Install, your
site will “spin” on those garbage systems when trying to install the
ConfigMgr client. Because most AD environments are not copasetic, it is
important to discover only those Organizational Units (OUs) that are
known to be clean, or not enable Push Install.
|