As the preceding note says, Windows 7
computers only let network users see the presence of files and folders
that they actually have permission to use, based in most cases on their
username and password. It’s worth explaining just how that permission
is determined. It’s not that difficult a topic, but it’s complicated by
the fact that there are several different ways that permissions are
calculated by Windows networking, depending on settings and the
versions of Windows you encounter. In the following discussion, I refer
to “files,” but the issues are the same for both the files and folders
inside any shared folder.
There
are two levels of security involved when Windows grants a user access
to a file over a network: permission settings on the file itself, which
would apply if the user logged on at the computer directly, and
“network permissions,” which can add additional restrictions when the file is accessed over the network, but can’t grant any additional permissions
that a user wouldn’t have if he or she tried to access the file while
logged in directly to the computer. I’ll explain why this is done
shortly. Let’s look at file permissions first.
File Permissions and Networking
File
permissions determine who can read, modify, write to, or delete a file
or folder based on their user account. Files and folders stored on a
disk formatted with the NTFS file system (which is always used on the
disk that contains Windows 7) can have these permission settings set on
a user-by-user basis as well as by membership in groups like
“Administrators” or even “Everyone.” When you log on to a computer
using your username and password, these settings determine which files
you can look at, and which you can change.
When
you access a file over a network, this permission system still applies.
What can get confusing is, how does the networked computer that
contains a file you want to use determine who you are? The answer to
that question depends on the version of Windows and some settings. Here
are several scenarios you might encounter. Go down through the list to
find the first scenario that describes your situation, and stop there.
In the following discussion, “the network computer” refers to a
computer on the network that has a file you want to use, and “you” and
“your computer” are trying to get to the file.
If
your computer and the network computer are members of a domain network,
your user account is recognized by all computers on the network. You’ll
get access to the file based on the permissions granted to your
account, and to groups to which you belong.
If
your computer and the networked computer are members of a homegroup,
and if you left enabled the Advanced Sharing setting Let Windows Manage
the Workgroup Connections, as it is by default, your computer will
connect to all other homegroup computers using the built-in user
account HomeGroupUser$. The member computers all know the
HomeGroupUser$ account’s password, so homegroup access works regardless
of how your user accounts are set up. Whenever you share a library,
folder, or file with your homegroup, Windows sets permissions on that
library, folder, or file so that the HomeGroupUser$ account has Read
and/or Write access. In this way, all users in the homegroup get the
same access rights to the shared resources.
If
the network computer runs Windows 7 or Vista with Password Protected
Sharing turned on, or XP Professional with Simple File Sharing
disabled, or Windows Server in a domain that your computer is not a
member of, the network computer will see whether it has an account set
up with the same name and password as on your own computer. If so, it
will grant you access to files based on rights set for your account. If
the account or password doesn’t match, your computer will prompt you to
enter an account name or password that is valid on the network computer.
If
both your computer and the network computer run Windows 7, and the
network computer has Password Protected Sharing turned off, a rule
unique to Windows 7 applies:
If the
network computer has an account with the same name as your account, and
that account has a password set, you will be given access to a file
based on privileges set for your account and groups you belong to.
If
the network computer doesn’t have an account with the same name as
yours, or if your account on that computer has no password set, files
will be accessed via the Guest account. Basically, you will only be
able to access files readable or writable by group Everyone.
The
last scenario is that the network computer runs Windows 7 or Vista with
Password Protected Sharing turned off, or XP Home Edition or XP
Professional with Simple File Sharing turned on, and your computer
isn’t running Windows 7. In this case, the network computer grants
access using the Guest account in all cases. Basically, you’ll only be
able to use files that are readable and/or writable by Everyone or
Guest.
Phew! I know this looks
like a big mess, but it actually boils down to just two alternatives: A
network computer either will use a specific account to access files, in
which case you can get to the files that this account can see, or will
use the Guest account, in which case you only can get to files that are
marked as usable by Everyone or Guest.
Another
point to remember is that files stored on removable media typically
don’t use the NTFS format, and don’t have any per-user permission
settings. Floppy disks and flash media formatted with the
FAT or ExFAT file systems are readable and writable by everyone, and
CD/DVD-ROMs are readable by everyone who connects to the computer.
Network permissions, described next, do apply.
Network Permissions
The
preceding permission scheme applies equally to files accessed over the
network and files accessed directly by logging in to a computer. When
you share a folder or drive through the network, though, you can assign
privileges, again based on user accounts that act like a filter for the
file permissions that we just discussed. A network user gets only the
privileges that are listed in both file permissions and network permissions. Figure 1 shows how this works.
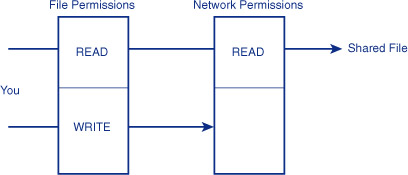
Another way to look at this is, a network user loses any permissions that are omitted from the network permission list. This can be used in complex ways, but mostly only two situations are used:
If
you share a folder and set its network privilege list to give Read
access, but not Write access, to Everyone, then users get Read access if their user account gives them permission, but nobody gets to modify its files over the network.
If
you set the network permissions so that Everyone has both Read and
Write permissions, then users get exactly what they’d get if they tried
to use the file while logged on directly; no more, no less.