5. Protecting Against “Drive-By” Downloads of IE Add-Ons
A
recurring cause of instability in Windows machines is attributable to
what’s sometimes called “drive-by” downloads from the Web. How many
times have you visited a website only to see a pop-up dialog box saying
you need to install software for the website to work on your browser?
Sometimes it’s clearly stated why this is necessary (for playing a
video, a proprietary sound file, or Flash animation, for example), and
other times, the reason is not so clear. All you know is that you are
faced with the decision of letting some (typically) unknown source
install software on your computer so you can enjoy the web page, or
opting out and moving on. Maybe you assume it can do no harm because
it’s only an addition to IE and not to your operating system. But
because IE is often the back door through which viruses, adware,
spyware, Trojan horses, and other malware infect your computer, being
cautious at this juncture is extremely important.
These spur-of-the-moment additions that websites can push at you are called IE add-ons,
and they are typically ActiveX controls (although not all are). ActiveX
controls and active script (sometimes called script or JavaScript) are
small programs used extensively on the Internet. Without scripts,
websites would be much more static and boring. Script and ActiveX
controls allow all sorts of animation and other entertaining features
on the Internet. Websites become more interactive by offering
customized content based on information about your computer, your
browser, and so on. Common add-ons include extra toolbars, animated
mouse pointers, stock tickers, and pop-up ad blockers.
Add-ons can be installed from a variety of locations and in several ways, including these:
Download and installation while viewing web pages
User installation via an executable program
As preinstalled components of the operating system
As preinstalled add-ons that come with the operating system
A
risk of add-ons is that these programs can also be used to collect
information from your computer for harmful purposes. After 6 months or
a year of surfing the Web with IE, many users don’t recall what add-ons
they authorized and don’t know what those add-ons might be doing to
compromise the stability of their systems.
You
could unknowingly have many add-ons installed. This can happen if you
previously gave permission for all downloads from a particular website,
or because the add-on was part of another program that you installed.
Some add-ons are installed with Microsoft Windows.
You’ll
sometimes be given more information about potentially damaging add-ons
so you can make an informed decision about installing one. Some add-ons
have digital signatures that verify who wrote them. This is called a certificate.
IE verifies a signature and can tell you if it’s valid. If a signature
is reported as invalid, you definitely shouldn’t trust the publisher as
asserting a truthful identity. Allowing installation of ActiveX
controls that have invalid signatures obviously is not recommended and
introduces additional risk to your computer.
IE blocks file downloads in these circumstances when you are using the default security settings:
When a file has an invalid signature on its certificate
When a file has no signature on its certificate
When you or someone else who uses your computer has blocked the source of the file
Even
if an add-on has a legitimate certificate, it doesn’t mean the program
won’t mess up your computer. In the end, it is your decision whether to
install an add-on. Make the decision based on whether you know the
source to be trustworthy. After installing an add-on, if your system or
IE becomes unstable, use the information in the following section to
track and remove the add-on.
Allowing Add-Ons with Invalid Signatures
Some
add-ons are known to be bad; Microsoft has blocked these intentionally.
You can’t install or run add-ons from blocked publishers on the
computer. If you really want to, you can force the use of an add-on
that has an invalid signature:
1. | In IE, click the Tools button, click Internet Options, and then click the Security tab.
|
2. | In the Security Level for This Zone box, click Custom Level.
|
3. | Scroll down to Download Unsigned ActiveX Controls and choose Enable or Prompt.
|
Another approach is to unblock a specific publisher. This is a safer approach because it doesn’t open you up to all invalid signatures. To do this, follow these steps:
1. | Click the Tools button, click Manage Add-Ons.
|
2. | Select
the publisher you want to unblock and then click Enable (you can also
right-click the add-on entry and click Enable from the context menu
that appears).
|
3. | Some
publishers’ add-ons have related add-ons that are affected when you
enable or disable them. From the Enable Add-Ons dialog box that
appears, select any related add-ons and click Enable.
|
Viewing and Managing Your IE Add-Ons
You
can review all your add-ons, update selected ones, choose ones to
remove, and, if you’ve been having IE crashes, potentially see which
one was responsible for your last IE crash. (Crashing can happen if the
add-on was poorly built or was created for an earlier version of IE.)
You work with your add-ons using the IE Add-On Manager, which even
shows some add-ons that were not previously shown and could be very
difficult to detect.
To see all add-ons for Internet Explorer, follow these steps:
1. | Click the Tools button, and then click Manage Add-Ons. You’ll see the Manage Add-Ons window, shown in Figure 4.
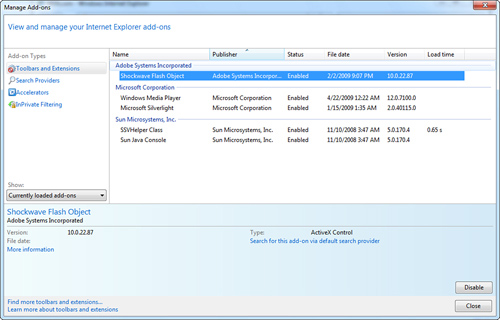
|
2. | In the Show drop-down list, select the set of add-ons you want to see.
|
Add-ons
are sorted into four groups in the Show list. All add-ons represent a
complete list that includes all the add-ons that reside on your
computer. Currently loaded add-ons are only those that were needed for
the current web page or a recently viewed web page. Choosing Run
Without Permission shows add-ons that do not explicitly require
permissions to run. Choosing Downloaded Controls lists all
browser-based controls (such as Java plug-ins).
Some add-ons can crash your IE session. If you experience a system crash after you’ve installed an add-on, you have two options:
Disable it—
If an add-on causes repeated problems, you can disable the add-on.
Click the add-on you want to disable and then click Disable. Some web
pages, or IE, might not display properly if an add-on is disabled. It
is recommended that you disable an add-on only if it repeatedly causes
IE to close. Add-ons can be disabled but not easily removed.
Report it— When
prompted, you might want to report the glitch to Microsoft. This is
completely anonymous and requires nothing from you but your permission.
Microsoft claims the info is used improve its products and to encourage
other companies to update and improve theirs.
Note
If
you disable an add-on and then realize it was needed, click the add-on
you want to enable, select the entry in Manage Add-Ons and then click
Enable. |
Internet
Explorer Add-On Crash Detection attempts to detect crashes in IE that
are related to an add-on. If IE identifies the faulty add-on, you’ll be
informed. You then have the option of disabling add-ons to diagnose
crashes and improve the overall stability of IE.