5. Editing Registry Entries for Another Windows Installation
If you need to retrieve Registry entries from an
installation of Windows installed on another hard disk or partition,
you can load any of that installation’s hive files for editing or
exporting.
To edit the other installation’s Registry, you need to locate its hive files. They are usually found in the locations shown in Table 2.
Table 2. Usual Location of Hive Files
| Key | Default Location and Hive File |
|---|
| HKEY_LOCAL_MACHINE\SAM | \windows\system32\config\sam |
| HKEY_LOCAL_MACHINE\Security | \windows\system32\config\security |
| HKEY_LOCAL_MACHINE\Software | \windows\system32\config\software |
| HKEY_LOCAL_MACHINE\System | \windows\system32\config\system |
| HKEY_LOCAL_MACHINE\Components | \windows\system32\config\components |
| HKEY_USERS\.Default | \windows\system32\config\default |
To edit another Windows installation’s Registry, use the technique I described under “Editing Registry Entries for Another User,” but instead of locating a user’s NTUSER.DAT
file, locate the desired hive file on the other hard drive or
partition. Unload it after you’ve exported or corrected the desired
information.
In some cases, you will find that you cannot
view or modify keys loaded from another installation. This occurs if the
keys are protected with security attributes that list specific users or
groups defined in the other installation. In this case, you need to
first take ownership of the keys and then add yourself as a user who is
authorized to read or change the keys. The next section describes this.
Note
You rarely should have to
modify Registry security settings, but it does happen. The usual case
is that an incorrectly designed program places information in a subkey
of HKEY_LOCAL_MACHINE\Software that is intended to be shared
and modified by all users running the program. Because Windows does not
permit standard users to modify any keys in HKEY_LOCAL_MACHINE\Software
by default, the program might malfunction. Modifying permissions so
that standard users can edit the shared key is sometimes necessary to
fix the problem. Microsoft also sometimes recommends modifying Registry
security in emergency security bulletins. |
6. Editing Registry Security
Just as files and folders in an NTFS-formatted
disk partition have security attributes to control access based on user
and group identity, Registry keys and values also have a complete set of
Access Control attributes that determine who has rights to read, write,
and modify each entry.
If you absolutely must change permissions or
auditing controls, locate the desired key or value, right-click it, and
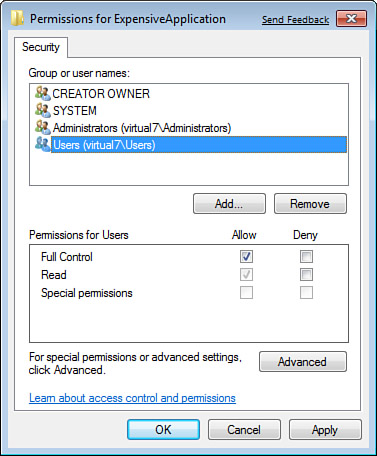
select Permissions. The Permissions dialog box looks just like the
comparable dialog box for files and folders (see Figure 3),
and lets you set read, write, and modify rights for specific groups and
users. You’ll find a corresponding set of audit settings.
In
most cases, a software vendor supplies precise instructions for making
changes necessary to work around an application problem. Here, I
describe a general procedure to make a given key readable and writeable
by all users. You might do this to make a key capable of sharing
information between users, or to repair an alternate Windows
installation, as mentioned in the previous section. To set more generous
permissions, follow these steps:
1. | Locate and select the key in the left pane.
|
2. | Right-click it and select Permissions.
|
3. | Select the Users entry in the top Group or User Names section. If Users is not listed, click Add, type Users, and click OK.
|
4. | In the lower section, check Full Control and then click Apply. If this is successful, click OK.
|
5. | If
you are unable to make the changes even though you’re running the
Registry Editor as an Administrator, click Advanced and select the Owner
tab.
|
6. | If the Current Owner is listed as unknown, select Administrators in the lower list and click OK.
|
7. | Click OK to close the Advanced Security Settings dialog box, and return to Step 3.
|
This is a risky procedure because it
could result in another user or application being unable to access its
own Registry keys. Use this as a procedure of last resort.