This section describes the most visible and tangible Windows Vista security improvements, which are listed in Table 1.
Architectural and internal improvements—as well as improvements that
require additional applications or infrastructure.
Table 1. Windows Vista security improvements
| Improvement | Description |
|---|
| User Account Control | Reduces the risk of malware using user privileges to make unwanted changes. |
| Windows Defender | Attempts to detect and block unwanted software. |
| Windows Firewall | Filters incoming and outgoing network traffic. New improvements provide greater flexibility and manageability. |
| Internet Explorer Protected Mode | Reduces risks associated with visiting websites, such as installing malware or visiting fraudulent sites. |
| BitLocker | Encrypts the entire system volume. |
| Encrypting File System | Encrypts files and folders other than system files. Improvements provide greater flexibility and manageability. |
| Auditing enhancements | Provide more granular control over which events are audited. |
| Smart card improvements | Simplify deployment and management of smart cards. |
| Credential Manager enhancements | Enables users to perform common credential management security tasks, such as resetting PINs. |
The sections that follow describe these features in more detail.
User Account Control (UAC)
Over the years,
the most common security threats have changed from viruses, to worms,
and most recently, to spyware and Trojan horses. To help protect users
from these types of malicious software, Microsoft recommends using
accounts with limited privileges (known as Standard user accounts in
Windows Vista, or Limited user accounts in Windows XP). Standard user
accounts help prevent malware from making system-wide changes such as
installing software that affects multiple users—if a user lacks
permission to install a new application to a shared location such as
%SystemRoot%\Program Files, any malware the user accidentally runs is
also prevented from making those changes. In other words, malware run in
the context of the user account has the same security restrictions as
the user.
While
Standard user accounts improve security, using Standard user accounts
with Windows XP and earlier versions of Windows results in two major
problems:
Users cannot
install software, change the system time or time zone, install printers,
change power settings, add a WEP key for wireless settings, or perform
other common tasks that require elevated privileges.
Many poorly written applications require administrative privileges and do not run correctly with limited privileges.
Although logging on
to your computer as a Standard user offers better protection from
malware, working with this type of account has been so difficult in the
past that many organizations choose to give users administrative
privileges on their computers. Windows Vista UAC is a set of features
that offers the benefits of Standard user accounts without the
unnecessary limitations. First, all users (including administrators) run
with limited privileges by default. Second, Windows Vista allows
Standard user accounts to change the time zone (but not the time) and
perform other common tasks without providing administrative credentials,
which enables organizations to configure more users with Standard
accounts. Third, UAC enables most applications—even those that required
administrative privileges on Windows XP—to run correctly in Standard
user accounts.
Admin Approval Mode
With Windows XP and
earlier versions of Windows, any process started by a user logged on as
an administrator would be run with administrative privileges. This
situation was troublesome because malware could make system-wide
changes, such as installing software, without confirmation from the
user. In Windows Vista, members of the Administrators group run in Admin Approval Mode,
which (by default) prompts administrators to confirm actions that
require more than Standard privileges. For example, even though a user
might log on as an administrator, Windows Messenger and Windows Mail
will run only with Standard User privileges.
To
do this, Admin Approval Mode creates two access tokens when a member of
the Administrators local group logs on: one token with full permissions
and a second, restricted token that mimics the token of a Standard
user. The lower-privilege token is used for non-administrative tasks,
and the privileged token is used only after the user’s explicit consent.
As shown in Figure 1, Windows Vista prompts the user for consent before completing an action that requires administrative privileges.
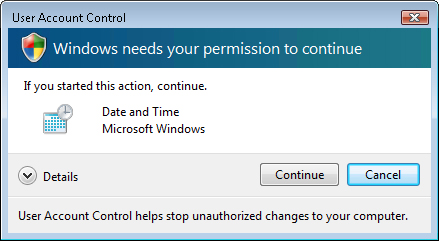
Many organizations will
use the benefits of UAC to create Standard, rather than Administrator,
user accounts. Admin Approval Mode offers some protection for those
users who need administrator privileges—such as developers—by requiring
confirmation before an application makes any potentially malicious
changes. Like most Windows Vista security improvements, the consent
prompt is enabled by default but can be disabled using Group Policy
settings. Additionally, the consent prompt can require the user to type
an administrative password or, for Standard users, simply inform them
that access is not permitted.
Enabling Non-Administrators to Make Configuration Changes
Standard user
accounts in Windows Vista can make configuration changes that don’t
compromise the computer’s security. For example, Standard user accounts
in Windows Vista have the right to change the time zone on their
computers, an important setting for users who travel. In Windows XP,
ordinary user accounts do not have this right by default, an
inconvenience that causes many IT professionals to deploy accounts for
mobile users as administrators and sacrifice the security benefits of
using ordinary user accounts. Additionally, Standard users can now
connect to encrypted wireless networks protected and add VPN
connections—two tasks commonly required by enterprises.
However, Standard user
accounts in Windows Vista do not have the right to change the system
time, because many applications and services rely on an accurate system
clock. As shown in Figure 2, a user who attempts to change the time is prompted for administrative credentials.
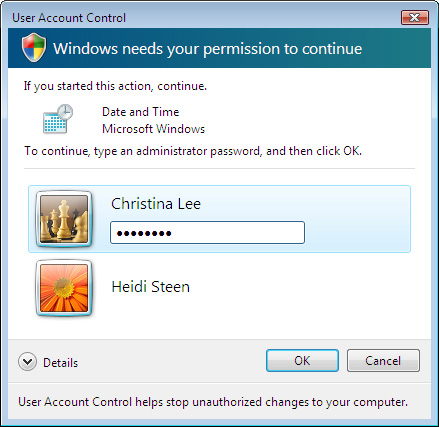
Some applications do not
run in Windows XP without administrative privileges, because these
applications attempt to make changes to file and registry locations that
affect the entire computer (for example, C:\Program Files, C:\Windows;
HKEY_LOCAL_MACHINE) and Standard user accounts lack the necessary
privileges. Registry and file virtualization in Windows Vista redirects
many of these per-machine file and registry writes to per-user
locations. This feature enables applications to be run by a Standard
user, where on previous operating systems, these applications would have
failed as Standard user. Ultimately, this will enable more
organizations to use Standard user accounts because applications that
would otherwise require administrative privileges can run successfully
without any changes to the application.
Note
Do
not confuse file and registry virtualization with operating system
virtualization products such as Microsoft Virtual PC or Microsoft
Virtual Server. File and registry virtualization virtualizes just those
operating system components, not the computer’s hardware. |
Windows Defender
Windows Defender is a
feature of Windows Vista that provides protection from spyware and
other potentially unwanted software. Windows Defender is
signature-based, using descriptions that uniquely identify spyware and
other potentially unwanted software to detect and remove known
applications. Windows Defender regularly retrieves new signatures from
Microsoft so that it can identify and remove newly created spyware and
other potentially unwanted software. Microsoft does not charge for
signature updates.
Additionally,
Windows Defender real-time protection monitors critical touch-points in
the OS for changes usually made by spyware. Real-time protection scans
every file as it is opened and also monitors the Startup folder, Run
keys in the registry, Windows add-ons, and other areas of the OS for
changes. If an application attempts to make a change to one of the
protected areas of the operating system, Windows Defender prompts the
user to take appropriate action.
As shown in Figure 3,
Windows Defender can also run a scan on-demand to detect and remove
known spyware. By default, Windows Defender will scan Windows Vista
computers daily at 2:00 AM for malware infections; however, you can
configure this behavior. Although Windows Defender real-time protection
attempts to prevent most infections, nightly scanning allows Windows
Defender to detect and remove newly discovered malware that might have
circumvented the defenses of real-time protection.
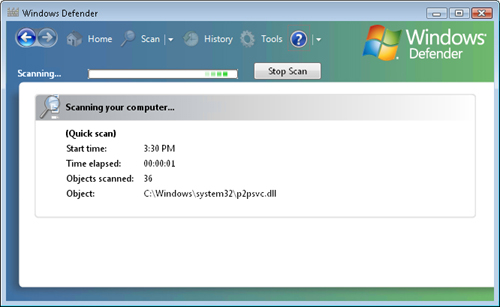
The
Microsoft SpyNet Community enables Windows Defender to communicate
discoveries about new applications and whether users identify
applications as malware or legitimate. Depending on how you configure
Windows Defender, it can provide feedback to the SpyNet community about
new applications and whether users choose to allow the application to be
installed. Feedback from the SpyNet Community helps Microsoft and users
distinguish malware from legitimate software, enabling Windows Defender
to more accurately identify malware and reduce the number of false
alarms. Providing private feedback to the SpyNet Community is optional;
however, all users can benefit from the information gathered by the
community.
In addition to
these features, Windows Defender includes Software Explorer. Software
Explorer provides users with control over many different types of
applications, including applications that install themselves into the
browser and into applications that start automatically. Software
Explorer is primarily intended for users who manage their own computers.
In enterprise environments, IT departments will typically handle
software removal.
Windows Firewall
Windows Vista has
an enhanced version of the Windows Firewall that was first included in
Windows XP Service Pack 2. The Windows Firewall combines the
functionality of a bidirectional host firewall and Internet Protocol
security (IPsec) into a single, unified utility with a consistent user
interface. Unlike a perimeter firewall, the Windows Firewall runs on
each computer running Windows Vista and provides local protection from
network attacks that might pass through your perimeter network or
originate inside your organization. It also provides
computer-to-computer connection security (IPsec) that allows you to
require authentication and data protection for all communications.
The Windows Firewall is
a stateful firewall, so it inspects and filters all TCP/IP version 4
(IPv4) and TCP/IP version 6 (IPv6) traffic. Unsolicited incoming traffic
is dropped unless it is a response to a request by the host (solicited
traffic) or it is specifically allowed (that is, it has been added to
the exceptions list or permitted by an inbound rule). Outgoing traffic
from interactive applications is allowed by default, but outgoing
traffic from services is limited by the firewall to that which is
required according to each service’s profile in Windows Service
Hardening. You can specify traffic to be added to the exceptions list
and create inbound and outbound rules according to application name,
service name, port number, destination network, domain membership, or
other criteria by configuring Windows Firewall with Advanced Security
settings.
For traffic that is
allowed, the Windows Firewall also allows you to request or require that
computers authenticate each other before communicating and to use data
integrity and data encryption while exchanging traffic.
In Windows Vista, the Windows Firewall has many new features, including:
Management integration with IPsec
Windows XP and earlier operating systems used two separate interfaces,
even though the Windows Firewall and IPsec had a significant amount of
feature overlap. Now, as Figure 4 shows, you can manage both using a single interface.
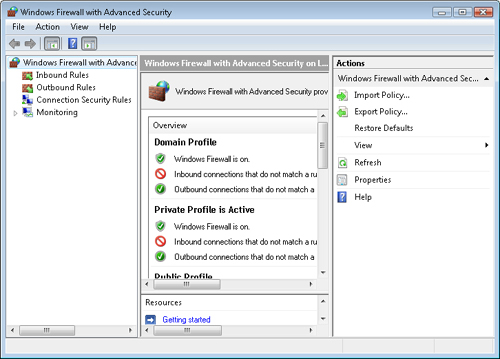
New user and command-line interfaces Improved interfaces simplify management and enable automated, scripted control over firewall settings.
Full IPv6 support If your organization uses IPv6, you can now take advantage of the Windows Firewall.
Outbound filtering
You can filter traffic being sent from a client computer as well as
traffic being received by the computer. This enables you to restrict
which applications can send traffic and where they can send it. For
example, you might filter management alerts so that they can be sent
only to your internal network. The outbound filtering feature in the
Windows Firewall is not intended to prevent an infected computer from
communicating, which is generally not possible (the malware might simply
disable the firewall). Rather, outbound filtering allows administrators
to assign policies to machines to prohibit known behavior, such as
preventing unauthorized peer-to-peer software from communicating.
Windows Service Hardening
This feature limits the actions a service can take and also limits how
the service communicates on the network, reducing the damage caused
during a security compromise.
Full Group Policy integration This enables you to centrally configure the Windows Firewall on all computers in your Active Directory domain.
Filtering traffic by new properties The Windows Firewall can filter traffic by:
IP address authentication
The Windows Firewall supports IP address authentication with the
ability to have two rounds of authentication with different credentials
in each, including user credentials if desired.
Application-based IPsec policies The Windows Firewall now supports application-based IPsec policies.
Simplified IPsec policy
This type of policy makes it much easier to deploy Server and Domain
Isolation. When configured with a simplified policy, client computers
make two connections to a destination: one in clear-text and one with
IPsec. The client computer will drop whichever connection does not
receive a reply. With a single rule, then, client computers can adapt themselves to communicate with IPsec or in clear-text, whichever the destination supports.
Internet Explorer Security Features
Microsoft Internet
Explorer 7 Plus features a focus on the core security architecture
changes that offer dynamic protection against data theft, fraudulent
websites, and malicious and hidden software, as well as improvements to
the platform for web developers. Microsoft has made architectural
enhancements to Internet Explorer 7 that make it less of a target for
attackers and other malicious people, which will help users browse with
better peace of mind. However, as security is tightened, compatibility
and extensibility tend to suffer. With Internet Explorer 7, Microsoft is
working hard to ensure that this balance is met effectively so that
users can have the safest and best possible browsing experience.
Note
The
“Plus” in the name indicates the version of Internet Explorer 7
included in Windows Vista, which includes capabilities that do not exist
in Internet Explorer 7 for Windows XP. |
Internet Explorer 7 includes the following security features:
Internet Explorer Protected Mode
In Protected Mode, Internet Explorer 7 runs with reduced permissions to
help prevent user or system files or settings from changing without the
user’s explicit permission. The new browser architecture also
introduces a “broker” process that helps to enable existing applications
to elevate out of Protected Mode in a more secure way. This additional
defense helps verify that scripted actions or automatic processes are
prevented from downloading data outside of the low-rights directories
such as the Temporary Internet Files folder. Protected Mode is only
available when using Internet Explorer 7 with Windows Vista when UAC is
enabled. Protected Mode is not available in the version of Internet
Explorer 7 for Windows XP.
URL handling protections
Internet Explorer 7 has a single function to process URL data,
significantly reducing the internal attack surface. This new data
handler ensures greater reliability while providing more features and
increased flexibility to address the changing nature of the Internet as
well as the globalization of URLs, international character sets, and
domain names.
ActiveX Opt-In ActiveX Opt-In
automatically disables all controls that the developer has not
explicitly identified for use on the Internet. This mitigates the
potential misuse of preinstalled controls. In Windows Vista, users are
prompted by the Information Bar before they can access a previously
installed ActiveX Control that has not yet been used on the Internet but
has been designed to be used on the Internet. This notification
mechanism enables the user to permit or deny access on a
control-by-control basis, further reducing
available surface area for attacks. Web sites that attempt automated
attacks can no longer secretly attempt to exploit ActiveX Controls that
were never intended to be used on the Internet.
Protection against cross-domain scripting attacks
New cross-domain script barriers help protect users from cross-domain
attacks, which attempt to transfer cookies and other information to
domains that should not have access to it. This adds further protection
against malware by limiting the ability of malicious websites to
manipulate vulnerabilities in other sites and initiate the download of
undesired content to a user’s computer.
Fix My Settings
Most users install and operate applications using the default
configuration, so Internet Explorer 7 ships with security settings that
provide the maximum level of usability while maintaining controlled
security. There are rare instances in which a custom application might
legitimately require a user to lower security settings from the default,
but it is critical that the user reverse those changes when the custom
settings are no longer needed. The Fix My Settings feature warns users
with an Information Bar when current security settings might put them at
risk. Clicking the Fix My Settings option in the Information Bar
instantly resets Internet Explorer 7 security settings to the
Medium-High default level. In Active Directory environments, you can
configure the required permissions for internal applications, so
security restrictions do not need to be a concern.
Phishing filters and window restrictions
Phishing websites attempt to use social engineering techniques to trick
users into providing private information. For example, a website might
impersonate an intranet site to trick the user into typing his or her
user name and password. The Phishing filter works by analyzing site
content for known characteristics of phishing techniques, and by using a
global network of data sources to assess whether a site should be
trusted. Additionally, all windows display the address bar, and scripts
can no longer conceal the address bar. This makes it easier for users to
identify the source of a web site and makes it obvious that a window is
in fact from a site and not from the operating system, thus mitigating
certain social engineering attempts to steal a user’s password by
mimicking a logon dialog box. Additionally, scripts can be restricted
from opening, resizing, or repositioning windows.
Security Status Bar
The new Security Status Bar in Internet Explorer 7 helps users quickly
differentiate authentic websites from suspicious or malicious ones by
enhancing access to digital certificate information that helps validate
the trustworthiness of e-commerce sites. The new Security Status Bar
also provides users with clearer, more prominent visual cues indicating
the safety and trustworthiness of a site, and it supports information
about High Assurance certificates for stronger identification of secure
sites (such as banking sites).
Additionally,
each of these features are configurable by using Group Policy, enabling
centralized control over Internet Explorer security.
BitLocker
Using
BitLocker Drive Encryption, organizations can reduce the risk of
confidential data being lost when a user’s mobile PC is stolen. Its
full-volume encryption seals the symmetric encryption key in a Trusted Platform Module (TPM) 1.2 chip (available in some newer computers) or a USB flash drive. BitLocker has two TPM modes:
TPM only
This is transparent to the user, and the user logon experience is
unchanged. However, if the TPM is missing or changed, BitLocker will
enter recovery mode, and you will need a recovery key or PIN to regain access to the data. This provides protection from hard-disk theft with no user training necessary.
TPM with startup key The user will also need a startup key
to log on to the computer. A startup key can either be physical (a USB
flash drive with a machine-readable key written to it) or personal (a
password set by the user). This provides protection from both hard-disk
theft and stolen computers (assuming the computer was shut down or
locked); however, it requires some effort from the user.
Note
To manage TPM chips, Windows Vista includes the TPM Management snap-in. |
BitLocker works by
storing “measurements” of various parts of the computer and operating
system in the TPM chip. In its default configuration, BitLocker
instructs the TPM to measure the master boot record, the active boot
partition, the boot sector, the Windows Boot Manager, and the BitLocker
storage root key. Each time the computer is booted, the TPM computes the
SHA-1 hash of the measured code and compares this to the hash stored in
the TPM from the previous boot. If the hashes match, the boot process
continues; if the hashes do not match, the boot process halts. At the
conclusion of a successful boot process, the TPM releases the storage
root key to BitLocker; BitLocker decrypts data as Windows reads it from
the protected volume.
BitLocker protects
Windows from offline attacks. An offline attack is a scenario in which
an attacker starts an alternate operating system to gain control of the
computer. The TPM releases the storage root key only when instructed to
by BitLocker running within the instance of Windows Vista that initially
created the key. Because no other operating system can do this (even an
alternate instance of Windows Vista), the TPM never releases the key,
and therefore the volume remains a useless encrypted blob. Any attempts
to modify the protected volume will render it unbootable.
Note
BitLocker
Drive Encryption provides protection for the Windows partition and is
not a replacement for the EFS. BitLocker Drive Encryption does not
provide encryption for the data stored outside the Windows partition but
does provide an added security layer for EFS by further encrypting the
EFS keys within the Windows partition. In addition, EFS provides an
additional security layer when multiple users use the same partition. A
user can have both BitLocker Drive Encryption and EFS enabled or either
technology enabled alone. If EFS is disabled, BitLocker Drive Encryption
will continue to function and vice versa. |
As shown in Figure 5,
individual users can enable BitLocker from Control Panel. Most
enterprises should use Active Directory to manage keys, however.
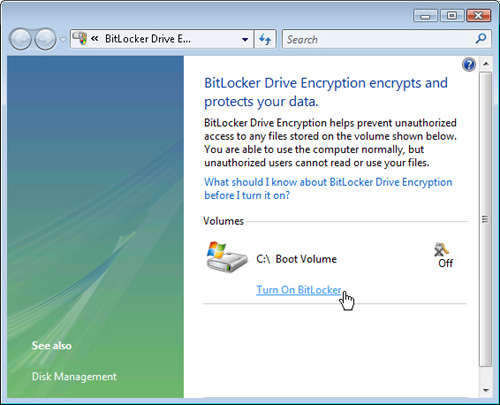
Key management and
data recovery requirements are the primary reason BitLocker is targeted
towards enterprises. As with any type of encryption, if you lose the
key, you also lose access to your data. Just as if you were a malicious
attacker, the entire Windows partition will be inaccessible without the
key. The most effective way to manage keys is to leverage an
enterprise’s existing Active Directory Domain Services infrastructure to
remotely escrow recovery keys. BitLocker also has a disaster recovery
console integrated into the early boot components to provide for “in the
field” data retrieval. Individual users can use the BitLocker
key-management tools to create a recovery key or an additional startup
key and store the key on removable media (or any location besides the
encrypted volume). Administrators can create scripts to automate key
creation and recovery.
BitLocker provides an important layer of protection, but it is only one part of Windows Vista data protection. BitLocker:
DOES make it very difficult for an attacker to gain access to your data from a stolen computer or hard disk.
DOES
encrypt the entire Windows volume, including the hibernation file, the
page file, and temporary files (unless they are moved to some other
volume).
DOES allow you to easily recycle or reuse drives by simply deleting the encryption keys.
DOES NOT protect data from network attacks.
DOES NOT protect data while Windows is running.
DOES NOT protect data on volumes other than the Windows partition. Use EFS to encrypt data on other volumes.
Other security
technologies, such as EFS, Windows Firewall, and NTFS file permissions
provide data protection while Windows is running.
|
There are three pillars of information security, known as the CIA triad:
Confidentiality Let people who should see your data access it, but nobody else. Integrity Know who has created, viewed, and modified your data, and prevent unauthorized changes and impersonations of legitimate users. Availability Allow users to access data when they need it, even when attacks and natural disasters occur.
BitLocker provides
confidentiality by encrypting data and making it more difficult for an
attacker who has physical access to a hard drive to access that data.
BitLocker can also provide integrity by detecting changes to critical
system files. It does not improve availability, however. In fact, if you
don’t plan to quickly recover systems with lost keys, BitLocker might
reduce availability.
|
Encrypting File System (EFS)
EFS
is a file encryption technology (supported only on NTFS volumes) that
protects files from offline attacks such as hard-disk theft. EFS is
entirely transparent to end users, because encrypted files behave
exactly like unencrypted files. However, if a user does not have the
correct decryption key, the file is impossible to open, even if an
attacker bypasses the operating system security.
EFS is especially useful
for securing sensitive data on mobile PCs or on computers that several
users share. Both kinds of systems are susceptible to attack by
techniques that circumvent the restrictions of access control lists
(ACLs). An attacker can steal a computer, remove the hard disk drives,
place the drives in another system, and gain access to the stored files.
Files encrypted by EFS, however, appear as unintelligible characters
when the attacker does not have the decryption key.
Windows Vista includes the following new features for EFS:
Storing both
user and recovery keys on smart cards. If smart cards are used for
logon, EFS operates in a Single Sign-On mode, where it uses the logon
smart card for file encryption without further prompting for the PIN.
New wizards guide users through the process of creating and selecting
smart card keys, as well as the process of migrating their encryption
keys from an old smart card to a new one. The command-line utilities for
smart cards have also been enhanced to include these features. Storing
encryption keys on smart cards provides especially strong protection for
mobile and shared computer scenarios.
Encrypting the system page file.
Auditing Enhancements
Windows
Vista auditing is very granular, allowing you to enable auditing for
very specific events. This reduces the number of irrelevant events,
potentially reducing the “noise” generated by false-positive auditing
events. This, in turn, can enable operations staff to more easily detect
significant events. Combined with the new Windows Event Collector
service, you can build a system to aggregate only the most important
security events in your organization.
Smart Card Improvements
For many organizations, the
risk that a password will be stolen or guessed is not acceptable. To
supplement password security, organizations implement multifactor
authentication that requires both a password and a second form of
identification. Often, that second form of identification is a smart
card, which contains a digital certificate that uniquely identifies the
card holder and a private key for use in authentication.
Both Windows 2000 and
Windows XP support authentication via smart cards. However, previous
versions of Windows required administrators to deploy and maintain
additional components to support their smart card infrastructure, such
as cryptography modules and communications support for card readers.
Smart card improvements in Windows Vista both simplify and improve smart
card management.
To simplify development of smart card software tools (which is typically done by the smart card provider), a common cryptographic service provider (CSP) implements all the standard back-end cryptographic functions that hardware and software developers need. In addition, integrated
third-party Card Modules make it easier to rapidly deploy a smart card
solution and enable protected, predictable communications between the
CSP and other components of the smart card infrastructure. Microsoft is
also working with smart card providers to improve the technology by
certifying smart card modules and making module updates available with
Windows Update.
Additionally, smart card
users will need to enter their PINs less frequently because of Kerberos
improvements, and users will be able to reset their PINs without calling
the support desk.
Credential Manager Enhancements
Windows Vista
includes new tools to enable administrators to better support credential
management for roaming users, including the new Digital Identity
Management Services (DIMS) and a new certificate enrollment process.
Among other improvements, users can now reset their own smart card personal identification numbers
(PINs) without calling the support center. Additionally, users can now
back up and restore credentials stored in the Stored User Names And
Passwords key ring.
To improve the
security of Task Scheduler, Windows Vista can use Service-for-User (S4U)
Kerberos extensions to store credentials for scheduled tasks, instead
of storing the credentials locally where they might be compromised. This
has the added benefit of preventing scheduled tasks from being impacted
by password expiration policies.