3. Sample Topology Considerations
These topologies provide some general guidance, but organizations
ultimately need to design a virtualized solution that works best for
them. These topologies provide a starting point, but should be taken
with consideration and adjusted to meet the needs of each organization
instead of simply reusing the sample topologies. There are a few key
issues with the sample topology; these are discussed in this section.
Guest Placement
With the published example, Microsoft has dedicated particular
virtual hosts for specific Lync Server roles such as only Front-End
Servers, only A/V Conferencing Servers, or only Directors. The obvious
issue with this type of deployment is that if a single host server
fails, it will bring down all the virtual machines running on that
server. With many of these roles, each host becomes a single point of
failure. So, although mixing roles across different host servers might
make performance testing or troubleshooting slightly more difficult, it
does remove one piece of hardware from being a single point of failure.
Disk Layout
The examples provided by Microsoft also use RAID 0 disk
configurations for the host servers in most cases. Although this
provides a performance benefit over other RAID configurations, the
reality is that most organizations prefer to offer some form of
redundancy at the physical disk level. If a single disk in a RAID 0
array fails, the entire array is lost, and all virtual machine disks on
that array are unavailable. Using a redundant disk configuration such
as RAID 5 or RAID 1+0 for most host servers offers some redundancy with
slightly reduced performance.
Edge Virtual Machine Collocation
One security concern the Microsoft design addresses is the fact that
the Edge Server should not be located on the same host machine as any
other server roles. This is because the Edge Server is designed to sit
in a perimeter network surrounded by firewalls on both sides.
Caution
Placing Edge Servers on a host machine within
the internal network is a bit of a security concern, which is why
Microsoft recommends separating these virtual machines.
In reality, many organizations will probably deploy Edge Servers on
the same host as other virtual machines. With the ability to tag
individual virtual machine adapters with a specific VLAN, the perimeter
network traffic can be directed to only the adapters assigned to Edge
Servers. Of course this means the perimeter network traffic passes
through the host hypervisor at some level, but this seems to be a
security issue less important for organizations because of the
flexibility gained with VLAN tagging. Of course, the proper firewall
rules should be in place to protect both the host and guest operating
systems. If nothing else, it might make sense to use perimeter network
hosts to also deploy virtual reverse proxy servers such as Microsoft
Forefront Threat Management Gateway, which also is typically placed in
a perimeter network.
Reverse Proxy
An often overlooked component of a deployment can be the
requirement for a reverse proxy server when enabling remote access. The
sample topology does not account for these
servers, but organizations should plan for these additional virtual
machines when deploying Lync Server. The requirements for each server
are not nearly as high as for a Lync Server role, but do consume some
resources on a host. Because these servers are typically placed in a
perimeter network, the same concerns exist as when virtualizing an Edge
Server deployment.
4. Additional Topologies
This section builds on the guidance suggested by Microsoft and
offers some additional sample topologies. These have not been
performance tested by Microsoft and are only a suggested starting
point. Each topology should be thoroughly tested for performance by an
organization before being placed into production.
Small Business
Small businesses looking to take advantage of virtualizing Lync
Server 2010 on-premises will likely be looking to leverage the core
feature set with remote access and possibly telephony integration. The
priority in this configuration is to deploy as many features as
possible with the least amount of hardware. High availability and
failover are not requirements in this scenario, but the downside here
is that a host or guest VM failure causes a complete loss in service.
The small business topology is shown in Figure 3.
Figure 3 Sample Small Business Virtual Topology
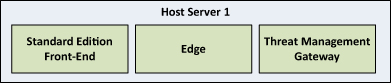
A single virtual host can be used with the following hardware configuration:
• 2.26 GHz or higher CPU with 12 processor cores
• 48 GB RAM
• 500 GB SAS Disk (RAID 1+0)
• Six network adapters
Three virtual machines will be created: one Standard Edition
Front-End Server with the Mediation Server collocated, one Edge Server,
and one reverse proxy server running Microsoft Forefront Threat
Management Gateway.
The Standard Edition Front-End Server would have the following configuration:
• Four virtual CPUs
• 16 GB RAM
• One network adapter
The Edge Server would have the following configuration:
• Four virtual CPUs
• 16 GB RAM
• Two network adapters
The Threat Management Gateway would have the following configuration:
• Two virtual CPUs
• 4 GB RAM
• Two network adapters
Medium-Sized Business
For those businesses that require a higher level of availability in
Lync deployments, it becomes necessary to use more host server hardware
and create additional virtual machines. This sample builds on the
deployment for a small business, but provides redundancy at each role
while adding monitoring and archiving abilities. Shared storage through
an iSCSI SAN is a requirement for providing database clustering
capabilities. This is only an example and can be modified to meet the
needs of a business. The sample medium-sized business topology is
depicted in Figure 4.
Figure 4 Sample Medium-Sized Business Virtual Topology
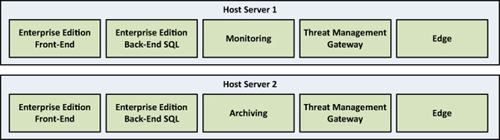
Two virtual hosts can be used with the following hardware configuration:
• 2.26 GHz or higher CPU with 16 processor cores
• 72 GB RAM
• 500 GB SAS Disk (RAID 1+0)
• 10 network adapters
Each host will run one virtual machine with the Enterprise Edition Front-End Server role in the following configuration:
• Four virtual CPUs
• 16 GB RAM
• One network adapter
Each host will run one virtual machine with the
Back-End Server role in the following configuration. The two Back-End
Servers can use SQL Server Failover Clustering to provide
high-availability across hosts:
• Four virtual CPUs
• 16 GB RAM
• Four network adapters
Note
The additional network adapters here are for
SQL Server Failover Clustering. In addition to the regular adapter, a
private heartbeat network should be used. Also, because SQL clustering
requires a shared disk, network adapters for iSCSI access to a SAN are
required. Two are used here to allow iSCSI multipathing for redundancy.
Each host will run one virtual machine with the Edge Server role in the following configuration:
• Four virtual CPUs
• 16 GB RAM
• Two network adapters
Each host will run one virtual machine with Microsoft Forefront Threat Management Gateway in the following configuration:
• Two virtual CPUs
• 4 GB RAM
• Two network adapters
One host will run a Monitoring Server virtual machine and the other
will run the Archiving Server virtual machine. Both will use the
following configuration:
• Four virtual CPUs
• 16 GB RAM
• One network adapter